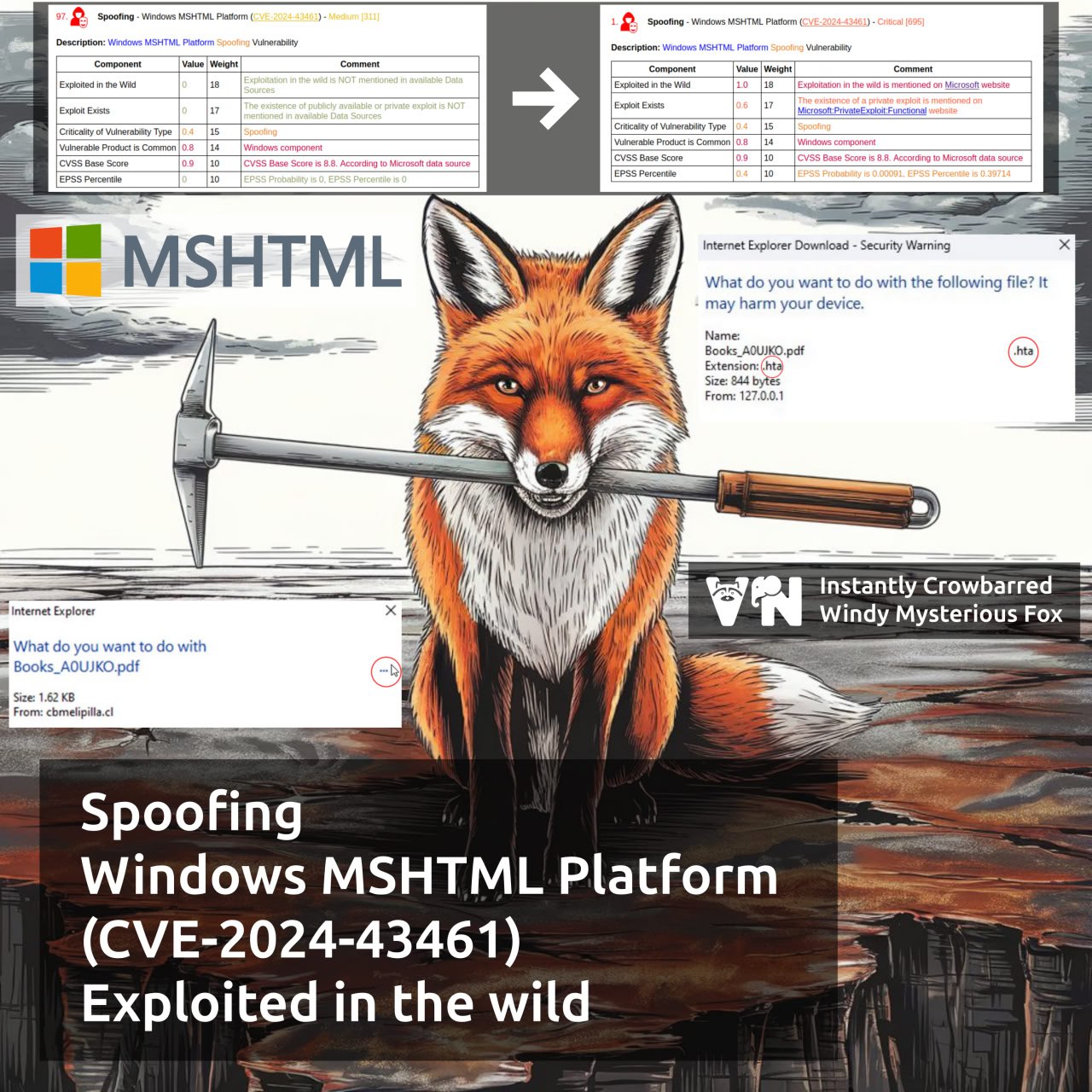
The severity of the Spoofing – Windows MSHTML Platform vulnerability (CVE-2024-43461) has increased. The vulnerability was fixed in September Microsoft Patch Tuesday. At the time of publication, Microsoft had not yet flagged this vulnerability as being exploited in the wild. They did this only 3 days later, on September 13.
ZDI Threat Hunting team researcher Peter Girnus discovered the vulnerability while investigating the Void Banshee APT attack. The vulnerability was exploited in the same attack chain as the trending Spoofing – Windows MSHTML Platform (CVE-2024-38112) vulnerability, patched in July.
Using this vulnerability, the attackers hid the extension of the malicious HTA file being opened by adding 26 Braille space characters to its name. Thus, victims may think that they are opening a harmless PDF document.
Installing the security update does not remove spaces in the file name, but Windows now shows the actual file extension. 👍

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: September episode of “In The Trend of VM”: 7 CVEs, fake reCAPTCHA, lebanese pagers, VM and IT annual bonuses | Alexander V. Leonov