About Remote Code Execution – Windows Shell (CVE-2026-21510) vulnerability. A vulnerability from the February Microsoft Patch Tuesday. The Windows Shell is the primary interface through which users interact with the Windows operating system. It includes visible elements such as the Desktop, Taskbar, and the Start Menu. Protection Mechanism Failure (CWE-693) allows an attacker to execute arbitrary code on the system by bypassing the Windows SmartScreen mechanism and Windows Shell warnings. To exploit the vulnerability, an attacker needs to convince a user to open a specially crafted shortcut file (.LNK) or follow a malicious link.
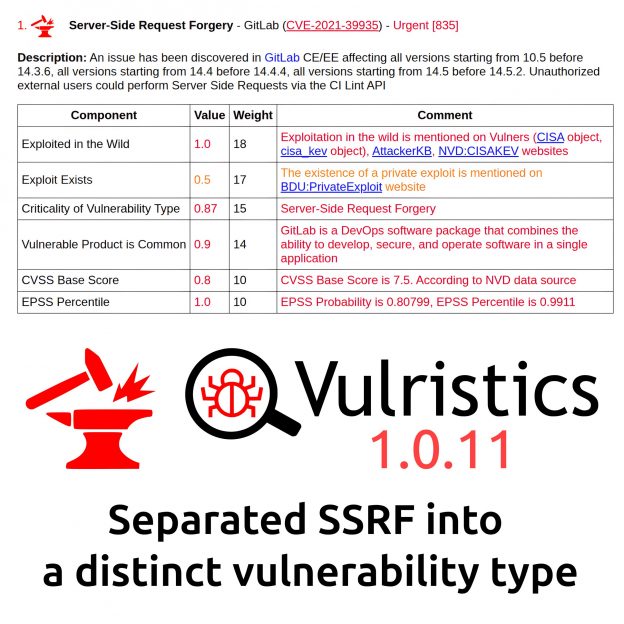
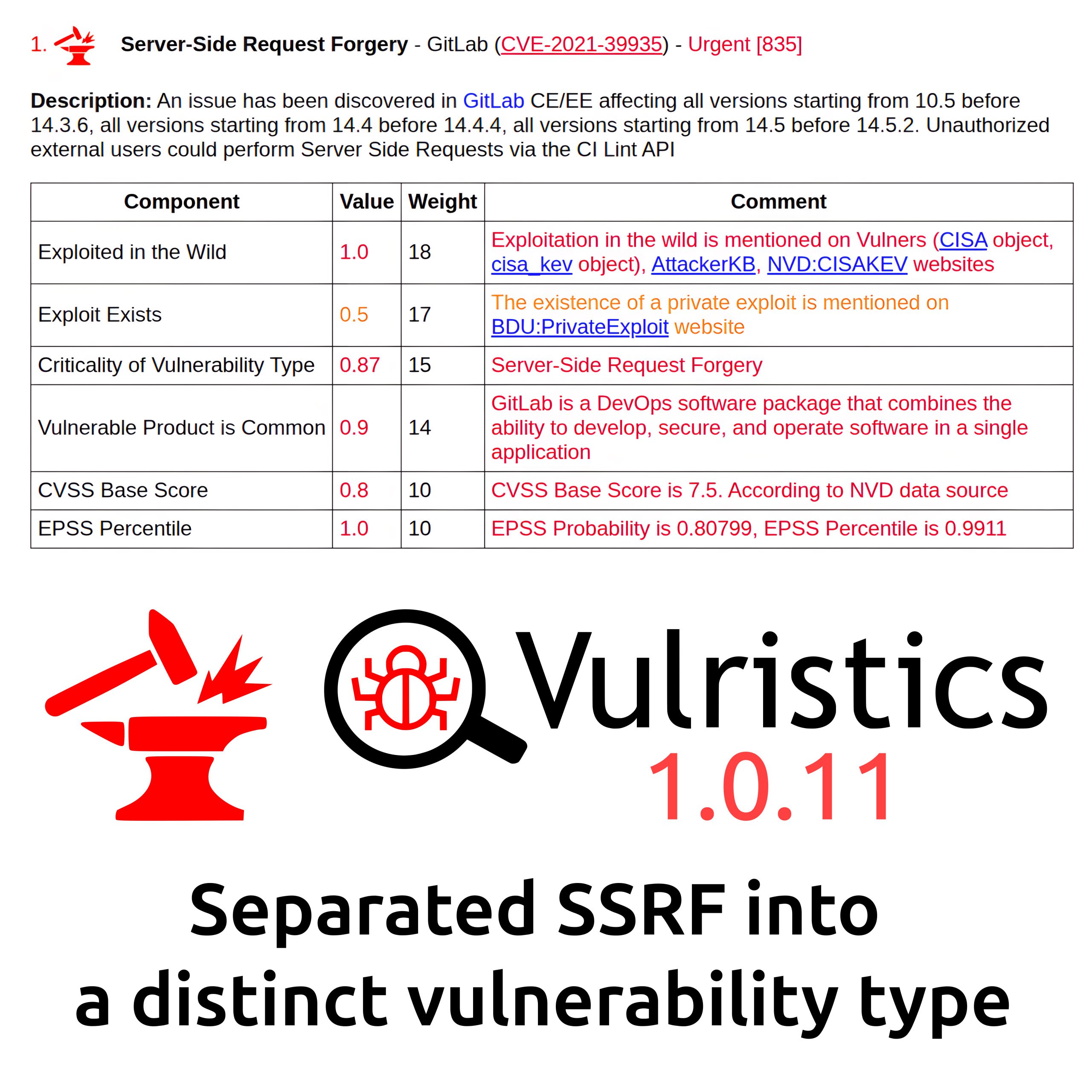
👾 Microsoft reports exploitation in the wild. The vulnerability has been listed in the CISA KEV since February 10.
💬 Microsoft classified the vulnerability as Security Feature Bypass, however it seems more appropriate to classify it as Remote Code Execution.
🛠 No public exploits are available yet.