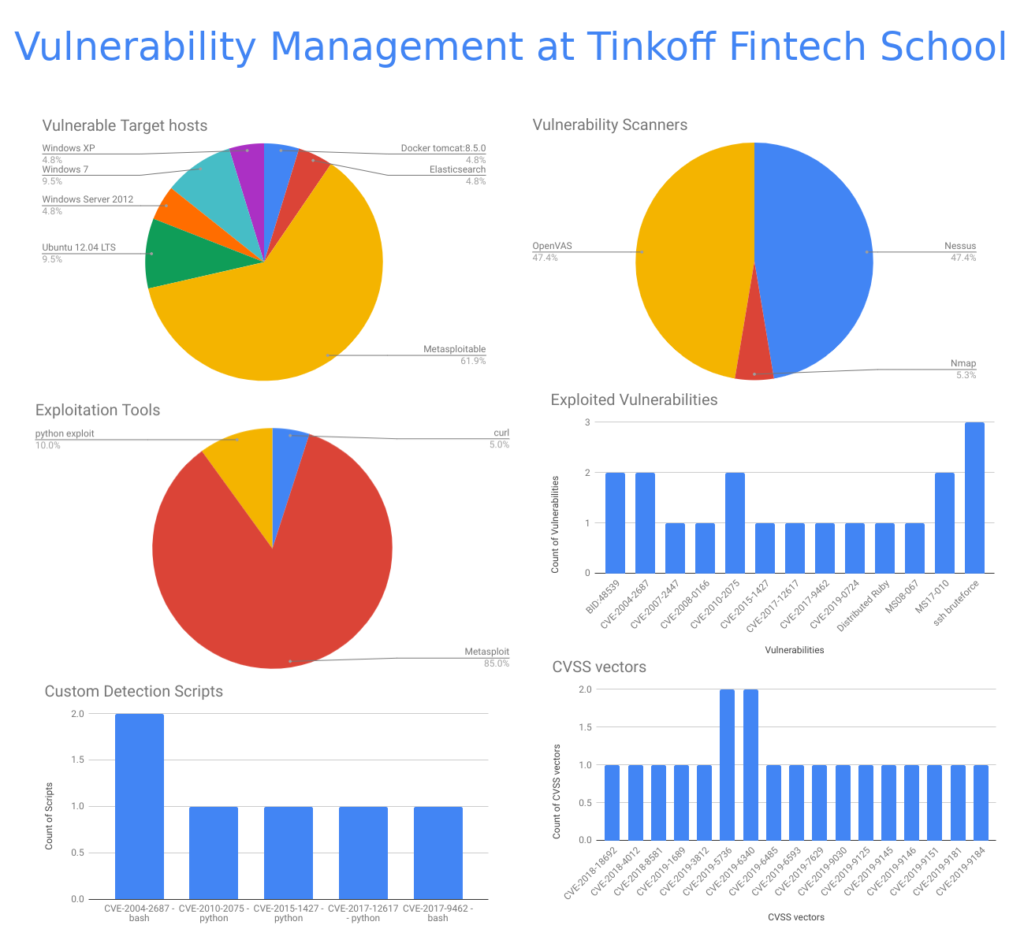
Hello guys! The third episode of Last Week’s Security news, July 5 – July 11. There was a lot of news last week. Most of them was again about PrintNightmare and Kaseya.
The updates for PrintNightmare (CVE-2021-34527) were finally released mid-week. It became possible not only to disable the service, but also to update the hosts. This is especially important for desktops that need to print something. But the problem is that these patches can be bypassed. “If you have a system where PointAndPrint NoWarningNoElevationOnInstall = 1, then Microsoft’s patch for #PrintNightmare CVE-2021-34527 does nothing to prevent either LPE or RCE”. Microsoft has updated their security update guide after that: “if you set this reg key to = 1 then the system is vulnerable by design”. It seems that solving this problem requires hardening and registry monitoring.
Continue reading