A few days ago I saw an interesting youtube video (UPD. 14.05.18 Not available anymore). It is demonstrating the exploitation of the RCE vulnerability in Tenable Nessus Professional 7.0.3. Currently we have very few information about this vulnerability: only youtube video, which is mentioned only on ExploitWareLabs.
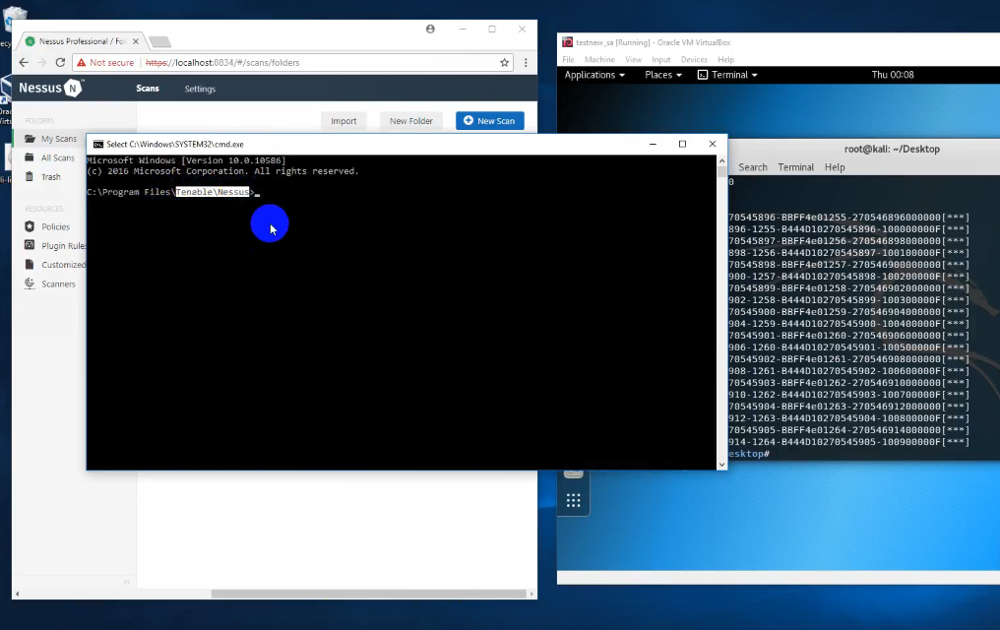
While there is no exploit in public access, it’s hard to say how it actually works. It’s also not clear what versions of Nessus are affected. 7.0.3 is the latest version currently. Because of API disabling in Nessus 7 many users are still on 6.11.3. It is not clear whether they are affected or not.
This even can be a fake video. Therefore, I specifically write “potential RCE”. I will update this post when more data is available.
UPD. 14.05.18 In the comments to my post anonymous account Destring Portal posted a comment with the second video of Nessus RCE exploitation and it seems, that it was made by the same author. In this video, the author runs a remote shell on the Nessus host and executes various commands. I will add review of this second video bellow.

UPD. 10.05.18 Renaud Deraison, Co-Founder and CTO of Tenable, commented on my post at Linkedin:
Our research team studied the video and we have several reasons to doubt its authenticity. We’ve conducted a thorough audit over the last 48 hours based the few details that are in the video and didn’t find anything. We reached out the researcher and instead of replying he removed the video*. We’ll communicate if indeed there is a risk.
In general, you are right though – the security of scanners is of paramount importance. This actually is a topic I’ve been extremely worried about ever since the early days of Nessus. We have a number of security mechanisms in place (interpreted language for the detection scripts, ciphered temporary files, very limited runtime environment) which really aim to limit the risk of being exploited but also to mitigate the risk should the scanner be compromised. I actually did a few talks in the past about scanning “rogue hosts” and we continue to treat all input as hostile.
Again, we’re continuing to investigate the matter and will let you know if we find anything.
* currently video is still available on the same address; it could be probably blocked for some time. (UPD. 14.05.18 Not available anymore)
In any case, it’s a good reason to talk about vulnerabilities of such kind, how they appear and how to protect Vulnerability Scanners from attackers.