Hello everyone! It has been 3 months since the last episode. I spent most of this time improving my Vulristics project. So in this episode, let’s take a look at what’s been done.
Alternative video link (for Russia): https://vk.com/video-149273431_456239139
Also, let’s take a look at the Microsoft Patch Tuesdays vulnerabilities, Linux Patch Wednesdays vulnerabilities and some other interesting vulnerabilities that have been released or updated in the last 3 months. Finally, I’d like to end this episode with a reflection on how my 2023 went and what I’d like to do in 2024.
New Vulristics Features
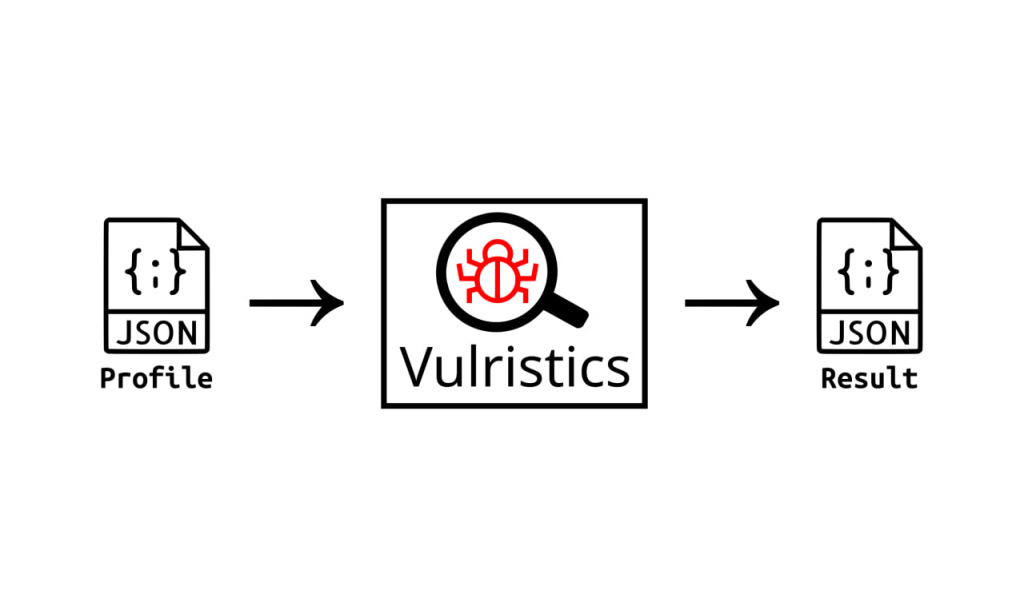
Vulristics JSON input and output
In Vulristics you can now provide input data in JSON format and receive output in JSON format. Which opens up new opportunities for automation.