Adding custom NASL plugins to Tenable Nessus. Making custom NASL scripts (plugins) for Nessus is a pretty complicated process. Basically, NASL (Nessus Attack Scripting Language) is an internal instrument of Tenable and it seem that they are not really interested in sharing it with the community. The only publicly available official documentation, NASL Reference Guide and NASL2 reference manual, was written at least 13 years ago. Certainly many things changed since then in the actual product.

However, it’s still possible to add custom NASL scripts into the plugin set of your Nessus server. Let’s see how to do it. Everything was tested in the latest Nessus 8.
The official information about importing custom NASL plugins is available in SecurityCenter 5.7.x User Guide at page 69 (see “Custom Plugins” section).
Note that the plugin should have big enough ID, for example more than 900000:
...
if (description)
{
script_id(900005);
script_version("1.0");
script_set_attribute(attribute:"plugin_modification_date", value:"2018/10/29");
script_name(english:"Custom Test Plugin");
script_summary(english:"Custom Description of the plugin");
script_set_attribute(attribute:"synopsis", value: "Custom Synopsis of the plugin.");
script_set_attribute(attribute:"description", value:"Custom Description of the plugin.");
...If we want to import it to some Nessus server, we need to make a special feed archive. This archive should contain a script and a custom_feed_info.inc file that looks like this:
PLUGIN_SET = "201809291526";
PLUGIN_FEED = "Custom";PLUGIN_SET value is just a timestamp in a format YYYYMMDDHHMM
So, we can generate it with bash script like this:
$ pset=`date +"%Y%m%d%H%M"`; echo -e "PLUGIN_SET = \"$pset\";\nPLUGIN_FEED = \"Custom\";" > custom_feed_info.inc;
$ cat custom_feed_info.inc
PLUGIN_SET = "201810231949";
PLUGIN_FEED = "Custom";Now we will add feed add script.nasl and custom_feed_info.inc to custom_nasl_archive.tar.gz archive:
$ tar -cvzf custom_nasl_archive.tar.gz custom_feed_info.inc script.nasl
custom_feed_info.inc
script.naslNote that feed may contain several scripts and, in this case, add them by *.nasl instead of script.nasl.
We send this archive to the server:
$ scp custom_nasl_archive.tar.gz user@nessus.corporation.ru:/home/user
custom_nasl_archive.tar.gz 100% 2162 49.0KB/s 00:00Then we go to the server and switch off the signature check (because our custom plugin doesn’t have it):
$ ssh user@nessus.corporation.ru
$ sudo su
# /opt/nessus/sbin/nessuscli fix --set nasl_no_signature_check=yes
Successfully set 'nasl_no_signature_check' to '...yes...'.And then we update the server using custom_nasl_archive.tar.gz file:
# /opt/nessus/sbin/nessuscli update /home/user/custom_nasl_archive.tar.gz
[info] Scan API is enabled for pro v7
* Update successful. The changes will be automatically processed by Nessus.And finally we launch nessusd with option -t, that means “check the timestamp of each plugin”:
# /opt/nessus/sbin/nessusd -t
nessusd (Nessus) 8.0.0 [build 20153] for Linux
Copyright (C) 1998 - 2018 Tenable, Inc.
Processing the Nessus plugins...
[##################################################]
All plugins loaded (11sec)After this we can stop nessusd with [ctr+c]. We can also restart nessusd after this, but it seems to be optional:
# service nessusd restart
When we login into the Nessus GUI we see a new plugin:
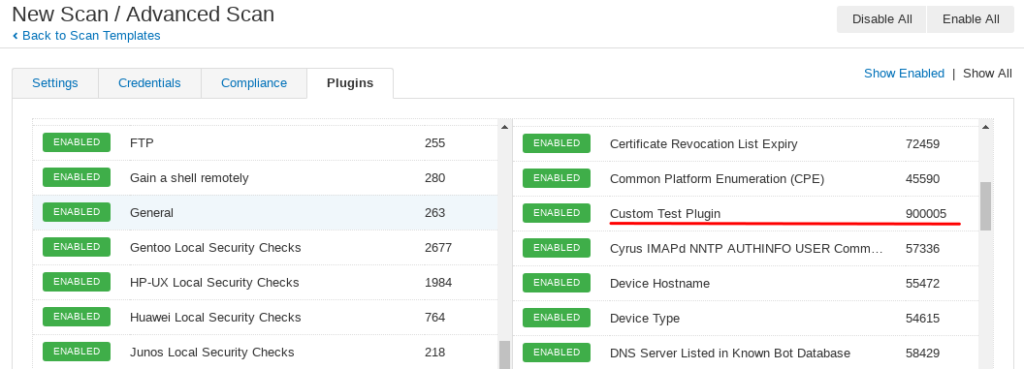
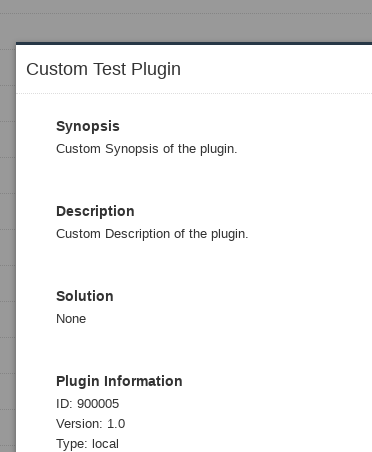
Plugin text:
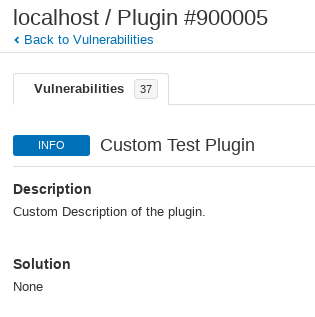
And in the scan results:
In conclusion
As you can see, it works. Of course, there is another question: does it make sense to use this tool, given the complexity of the development process.
Luckily, Nessus installation still contains console tool, also called nasl, that could be used for script debugging. But, in my opinion, for the most cases it’s much easier to develop stand-alone script, for example, using expect. And even you want to keep of security checks in Nessus, it’s easier to use .audit than NASL.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

I think .audit is a good choice for a supported platform – like Windows – although multiple tests on same setting can be a bit of a problem.
However, for non-supported devices – say looking for default passwords on IoT devices, .nasl is only solution within Nessus.
Just remember that if you add custom plugin to Nessus and initiate a scan with SecurityCenter in every scan you make this plugin will be launched unless you add this custom plugin to SecurityCenter but this is another story 😉