Do you need CentOS 8 with IceWM as desktop Operating System? Most likely not. Especially if you want it to work smoothly without any worries and troubles. However, if you enjoy playing with new desktop environments, you might find it fun.
My reasons were as follows:
- I wanted to use the same Linux distribution for server and desktop. Just to minimize possible surprises during the deployment.
- I wanted to know what is going on in the RPM-based part of Linux world. The only way to achieve this is to use such distribution every day.
- I was tired of problems with the Virtual Box guest additions in CentOS 7 (yes , I run it all as a virtual machine), especially after the 3.10 kernel updates. It was time to move on.
- I didn’t want to use Gnome 3, because it’s slow and ugly (however it’s fully functional!). And there were no other DEs in CentOS 8 repositories at that time.
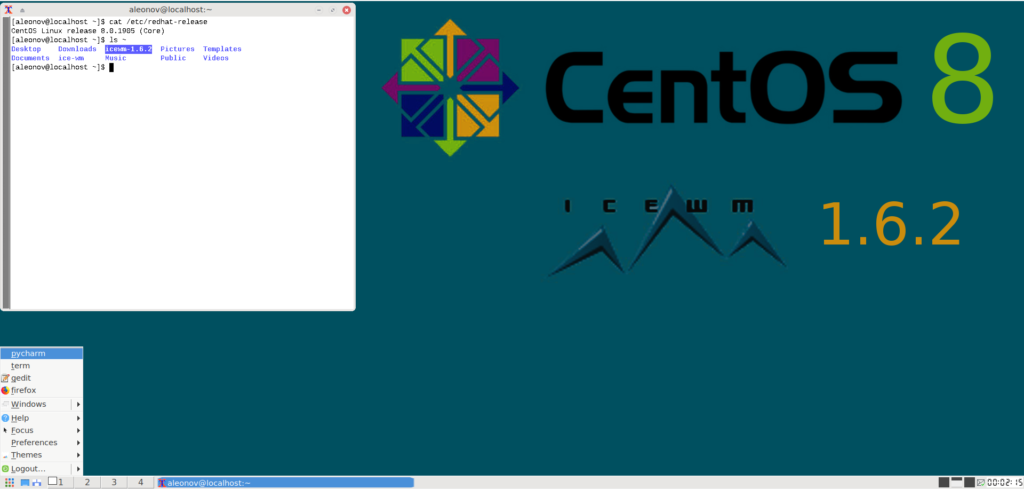
So, I tried CentOS 8 with IceWM (installed it from source) and it worked. IceWM is small, very fast, ascetic, and in some ways quite intuitive. There were some problems with the clipboard (in xTerm and with VBox shared clipboard) and with language switching, but I figured it out and I think that I would probably continue to use it. Below are some notes on how I installed it and resolved the issues.
Continue reading