upd. 29.09.2018 Unfortunately, the script does not work after Greenbone moved the sources from their internal repository to GitHub. It’s necessary to edit the script. Stay tuned.
In last month Greenbone Networks and OpenVAS development team have finally presented new OpenVAS 9 with new GUI, improved multi-scanner support, improved asset management, etc. We have been waiting for this release for 2 years!
Upd. Please note, that entire procedure for separating scanners onto separate hardware/distributed hardware in different datacenters has changed completely – and that it’s a good idea to get familiar with this new procedure prior to upgrading to OpenVAS 9. 😉
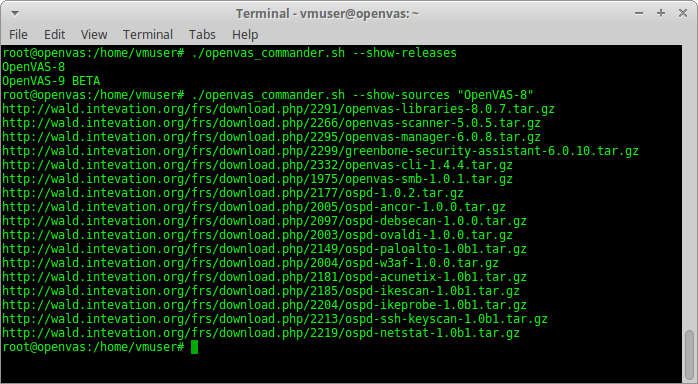
For installing OpenVAS 9 from the sources I used the same script as for OpenVAS 8 installation last year. More details about this script and why you may need it you can read in the post “openvas_commander for OpenVAS installation and management“.
I fixed the script a bit because of these changes in OpenVAS9:
- openvas-nvt-syncwas renamed to greenbone-nvt-sync
- openvas-mkcert and openvas-mkcert-client were replaced by openvas-manage-certs