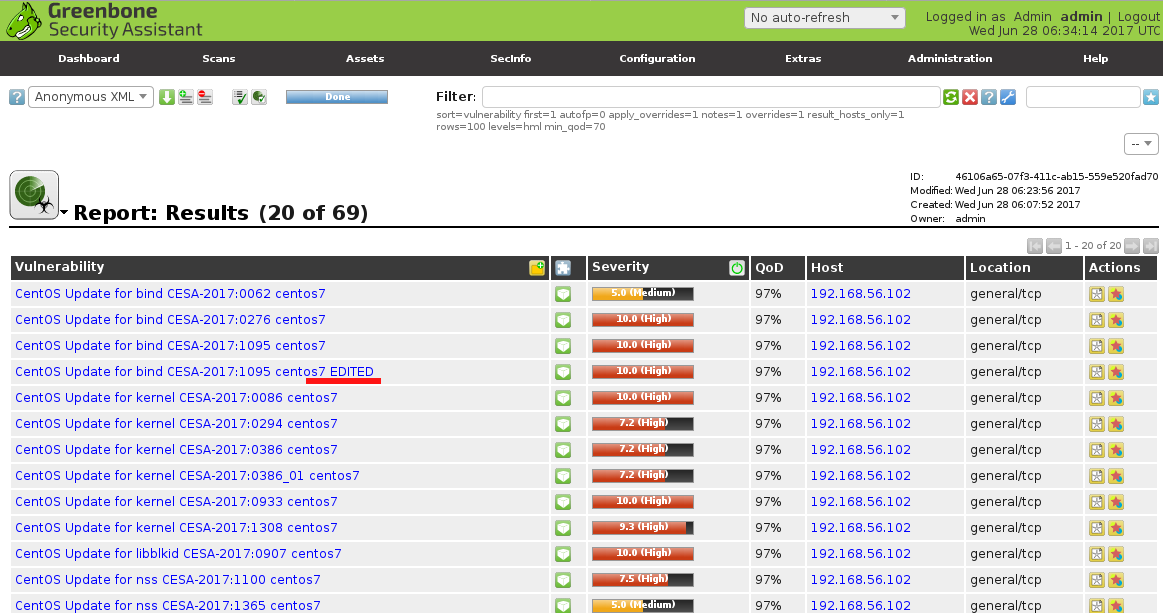
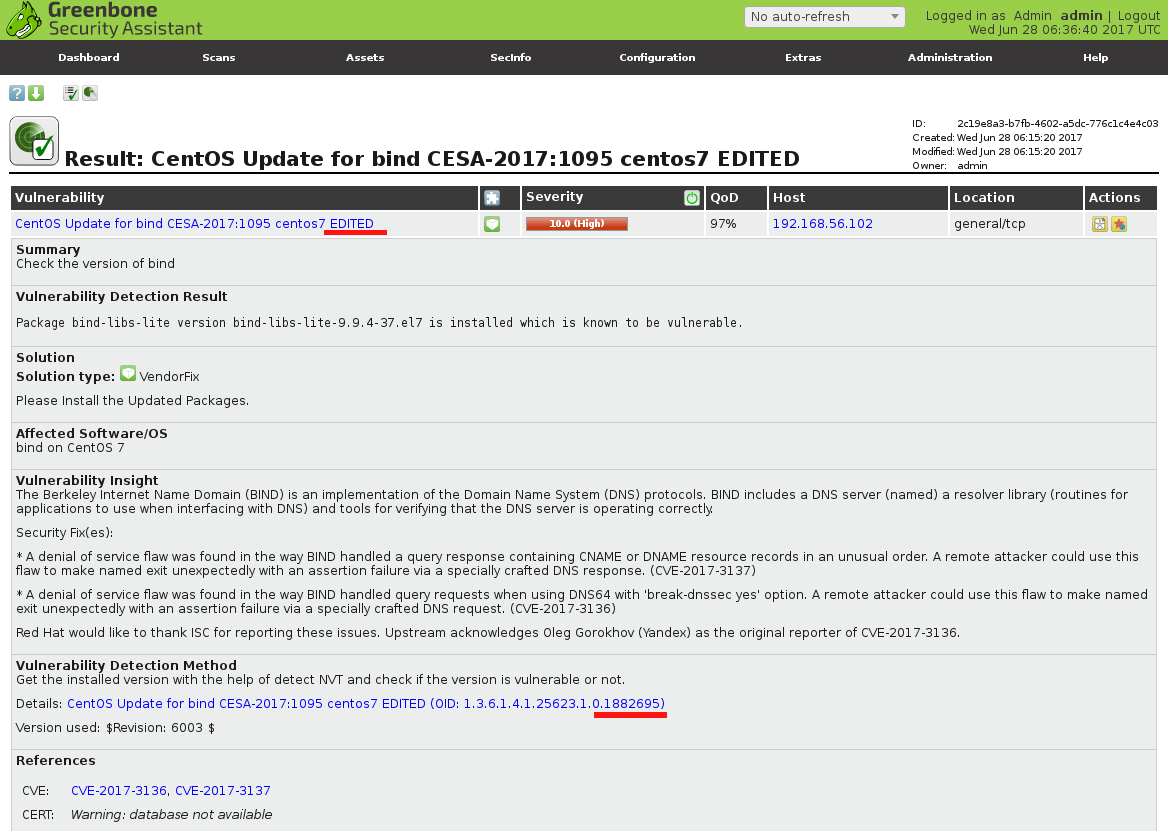
As I already wrote in “Installing OpenVAS 9 from the sources“, since May 2017 OpenVAS 9 is available in a form of free virtual appliance. It is called GSM Community Edition (GCE) and is based on Greenbone commercial product GSM ONE.
What’s the difference between GSM ONE and free GCE? GSM Community Edition uses different Community Feed of NASL plugins, it can’t be updated automatically and does not have some management features. The most important, in my opinion, is that it does not support OpenVAS Management Protocol (OMP), API for managing scanners. Only HTTPS for WebGUI and SSH are available.
Talking about different NASL plugin feeds, I need to mention recent message by Jan-Oliver Wagner in Openvas-announce list.
That seems like Greenbone is rather tired of developing OpenVAS by themselves and watching how other companies use theirs engine and feeds, positioning themselves as an “alternative to Greenbone’s product at a better price”. So, they decided:
- “OpenVAS NVT Feed” will be renamed to “Greenbone Community Feed”
- Public access to the “openvas-nvts” SVN repository will be forbidden, but the license of nasl plugins won’t be changed.
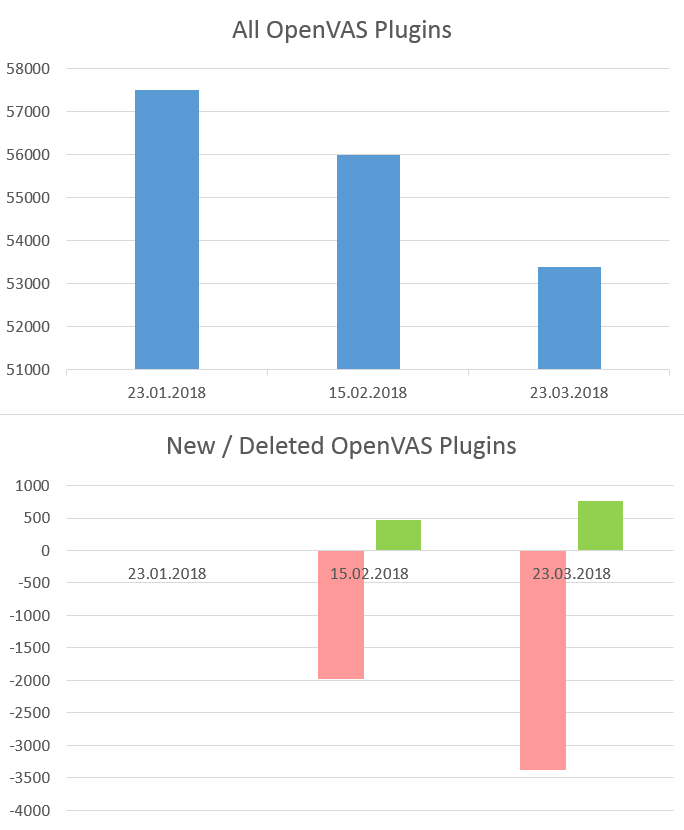
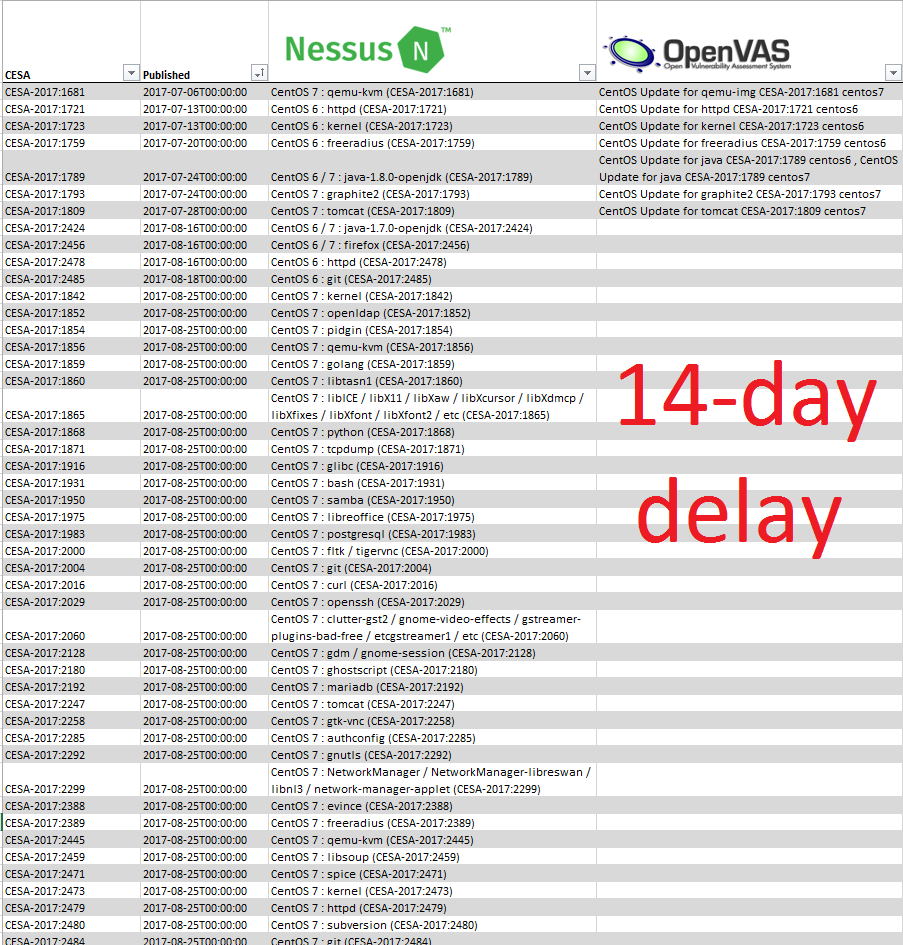
- Now Community Feed lags 14 days from commercial feed, but Greenbone would like to make an actual feed, but without some features for enterprise customers.
I really care about Greenbone and they, of course, do as they think is better for the company and OpenVAS community, but at the same time it reminds me situation with Tenable and Nessus. Maybe not so radical. But definitely in the same direction.
Feed delayed for 2 week can’t be used effectively for obvious reasons. If you see exploitation of critical vulnerability like WannaCry in the wild and will need to wait 2 weeks to check your infrastructure, it’s a nonsense! 🙂 That’s mean that you just can’t rely on OpenVAS anymore. And if you use it, you should think about migration on commercial solution, for example on Greenbone’s GSM, or think about getting actual plugin feed somewhere else.
The good thing, it might show customers once again that knowledge base of Vulnerability Management solution is important and stimulate other security content developers to make own nasl scripts and feeds.
But let’s go back to GSM Community Edition. Detailed description of installation process you can find on official site. I will just describe my own experience.
Continue reading →