Hello everyone! Five years ago I wrote a blogpost about OpenSCAP. But it was only about the SCAP Workbench GUI application and how to use it to detect security misconfigurations.
Alternative video link (for Russia): https://vk.com/video-149273431_456239104
This time, I will install the OpenSCAP command line tool on Ubuntu and use it to check for vulnerabilities on my local host.
Installation
First of all, we need to install OpenSCAP. I have Ubuntu 20.04.5 LTS on my host.
$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 20.04.5 LTS
Release: 20.04
Codename: focalAccording to the official OpenSCAP website oscap tool can be installed on Ubuntu with the command apt-get install libopenscap8.
$ sudo apt-get install libopenscap8
[sudo] password for alexander:
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following packages were automatically installed and are no longer required:
libfwupdplugin1 python3-defusedxml python3-pyqt5.qtopengl python3-zmq
Use 'sudo apt autoremove' to remove them.
The following NEW packages will be installed:
libopenscap8
0 upgraded, 1 newly installed, 0 to remove and 31 not upgraded.
Need to get 2,483 kB of archives.
After this operation, 66.2 MB of additional disk space will be used.
Get:1 http://ru.archive.ubuntu.com/ubuntu focal-updates/universe amd64 libopenscap8 amd64 1.2.16-2ubuntu3.2 [2,483 kB]
Fetched 2,483 kB in 0s (5,700 kB/s)
Selecting previously unselected package libopenscap8.
(Reading database ... 290720 files and directories currently installed.)
Preparing to unpack .../libopenscap8_1.2.16-2ubuntu3.2_amd64.deb ...
Unpacking libopenscap8 (1.2.16-2ubuntu3.2) ...
Setting up libopenscap8 (1.2.16-2ubuntu3.2) ...
Processing triggers for man-db (2.9.1-1) ...
Processing triggers for libc-bin (2.31-0ubuntu9.9) ...We can then check that the installation was successful with the command oscap -V
$ oscap -V
OpenSCAP command line tool (oscap) 1.2.16
Copyright 2009--2017 Red Hat Inc., Durham, North Carolina.
==== Supported specifications ====
XCCDF Version: 1.2
OVAL Version: 5.11.1
CPE Version: 2.3
CVSS Version: 2.0
CVE Version: 2.0
Asset Identification Version: 1.1
Asset Reporting Format Version: 1.1
CVRF Version: 1.1
...OVAL Content
Everything looks good and now we need to get the content describing the vulnerability checks. It’s great that Canonical has invested in creating free OVAL content feeds that can be downloaded from https://ubuntu.com/security/oval.
We download the content with wget.
$ wget https://security-metadata.canonical.com/oval/com.ubuntu.$(lsb_release -cs).usn.oval.xml.bz2
--2022-10-01 14:00:00-- https://security-metadata.canonical.com/oval/com.ubuntu.focal.usn.oval.xml.bz2
Resolving security-metadata.canonical.com (security-metadata.canonical.com)... 185.125.190.20, 185.125.190.29, 185.125.190.21, ...
Connecting to security-metadata.canonical.com (security-metadata.canonical.com)|185.125.190.20|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 276068 (270K) [application/x-bzip2]
Saving to: ‘com.ubuntu.focal.usn.oval.xml.bz2’
com.ubuntu.focal.usn.oval.xml.bz2 100%[=======================================================================================================>] 269.60K 1.35MB/s in 0.2s
2022-10-01 14:00:00 (1.35 MB/s) - ‘com.ubuntu.focal.usn.oval.xml.bz2’ saved [276068/276068]Unzip the data using bunzip2 tool:
$ bunzip2 com.ubuntu.$(lsb_release -cs).usn.oval.xml.bz2
$ ls com.ubuntu.*
com.ubuntu.focal.usn.oval.xmlVulnerability report
We can use the oscap tool to create an html vulnerability report. The tool shows the OVAL definition statuses while it is running.
$ oscap oval eval --report report.html com.ubuntu.$(lsb_release -cs).usn.oval.xml
Definition oval:com.ubuntu.focal:def:891000000: false
Definition oval:com.ubuntu.focal:def:871000000: false
Definition oval:com.ubuntu.focal:def:861000000: false
Definition oval:com.ubuntu.focal:def:851000000: false
Definition oval:com.ubuntu.focal:def:841000000: false
...
Definition oval:com.ubuntu.focal:def:43322000000: false
Definition oval:com.ubuntu.focal:def:43302000000: false
Definition oval:com.ubuntu.focal:def:41716000000: false
Definition oval:com.ubuntu.focal:def:100: true
Evaluation done.In this example, oscap has detected a vulnerability in the Firefox web browser.
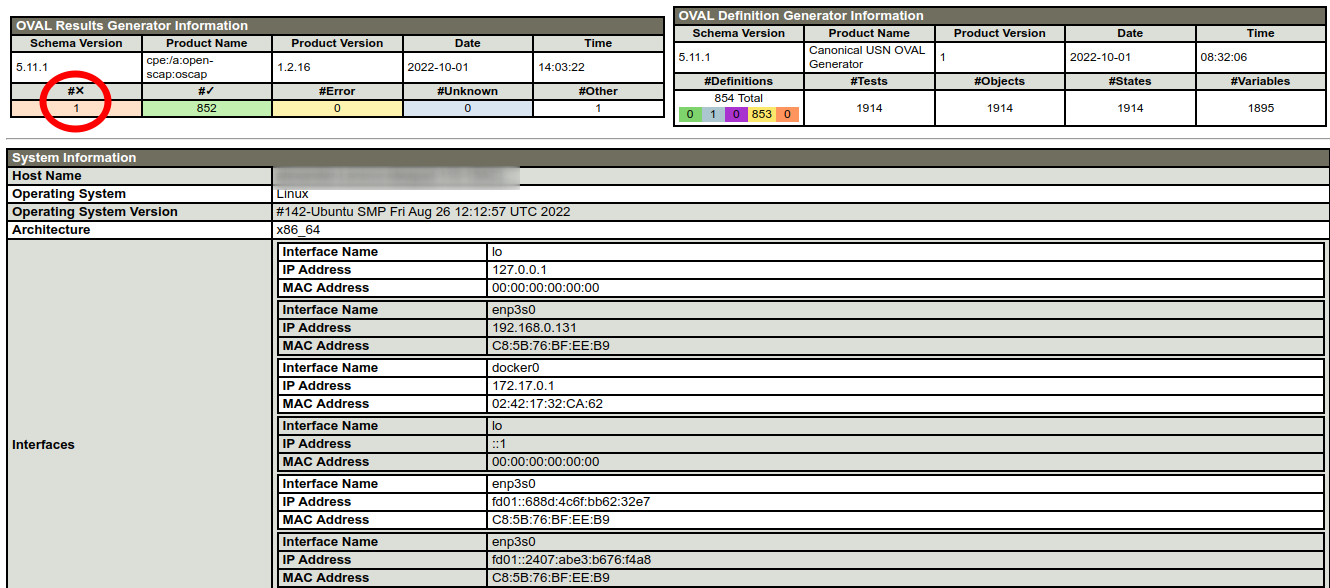
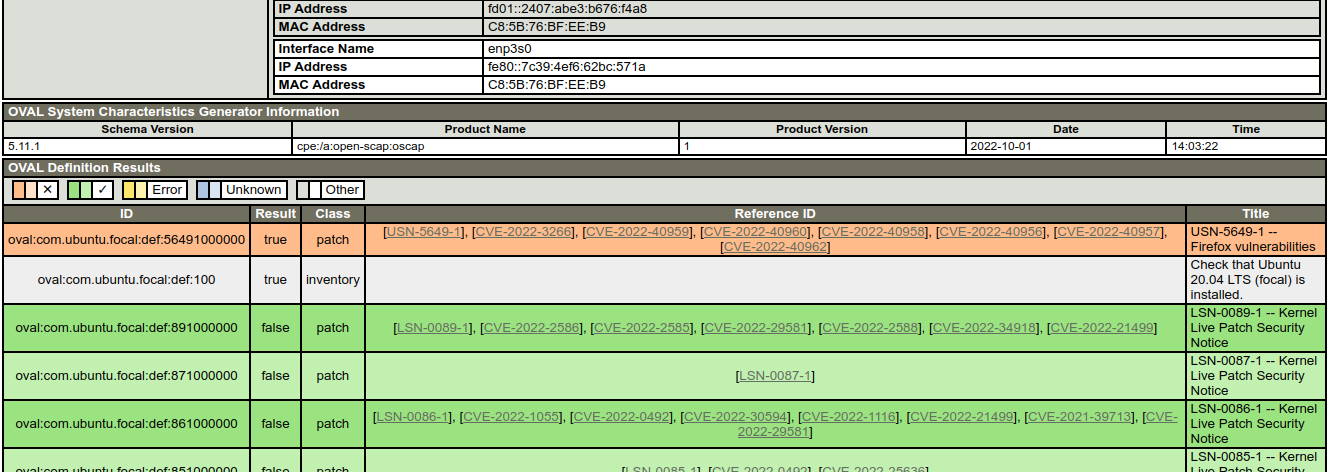
And after updating the Firefox package on the host, this vulnerability disappears.
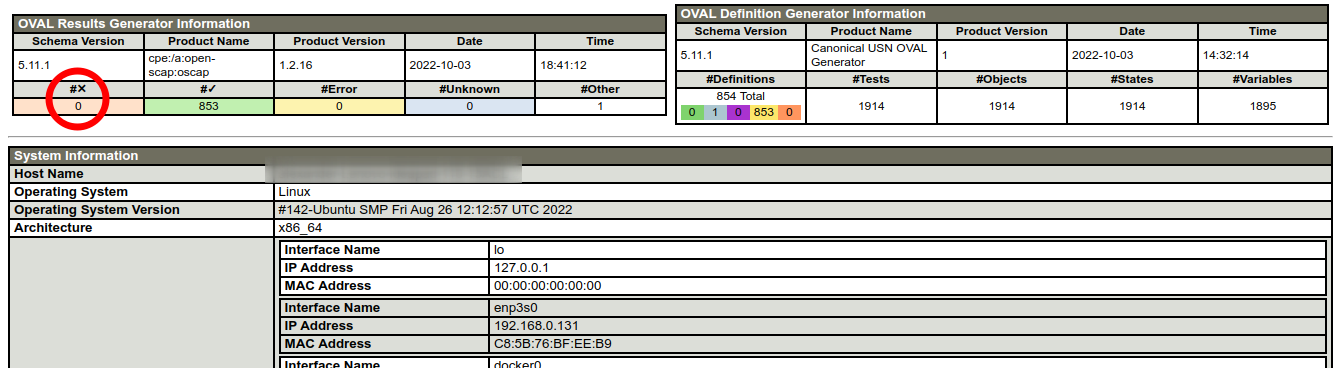
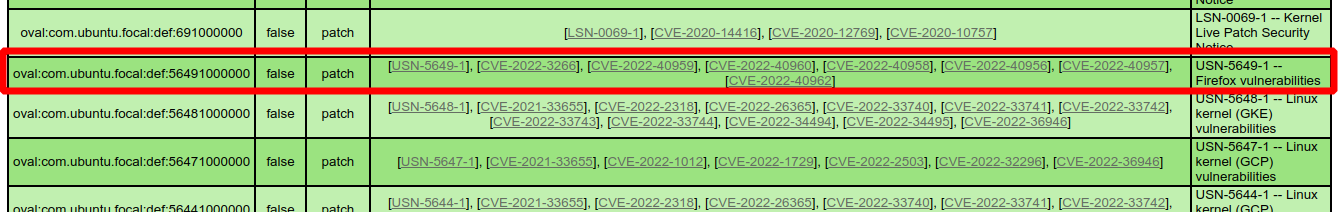
If you want to automatically process scan results, you can export them in XML format.
$ oscap oval eval --results oval-results.xml com.ubuntu.$(lsb_release -cs).usn.oval.xmlSeparating Inventory and Vulnerability Detection: System Characteristics
In most cases, using OpenSCAP looks like this. You install the OpenSCAP package on a target Linux host, copy the OVAL content to the host, and detect vulnerabilities directly on the host. You can then collect these results from the host and put them into some kind of vulnerability storage and prioritization solution.
Can we separate inventory collection from actual vulnerability detection? Yes, it is possible with the OVAL System Characteristics. The idea is that we collect inventory host data in a special XML format and then pass it as a parameter to the oscap tool. How does oscap know which objects to collect? It understands this from the same OVAL definition file.
So, we collect System Characteristics with
$ oscap oval collect --syschar syschar.xml com.ubuntu.$(lsb_release -cs).usn.oval.xml
Collected: "oval:com.ubuntu.focal:obj:8910000001" : does not exist
Collected: "oval:com.ubuntu.focal:obj:8910000000" : does not exist
Collected: "oval:com.ubuntu.focal:obj:8710000001" : does not exist
...
Collected: "oval:com.ubuntu.focal:obj:564910000000" : complete
Collected: "oval:com.ubuntu.focal:obj:564810000010" : complete
Collected: "oval:com.ubuntu.focal:obj:564810000000" : complete
...
Collected: "oval:com.ubuntu.focal:obj:100" : completeAnd then analyse and generate a report from it
$ oscap oval analyse --results oval-results.xml com.ubuntu.$(lsb_release -cs).usn.oval.xml syschar.xml
$ oscap oval generate report oval-results.xml > ssg-scan-oval-report.htmlTherefore, it is theoretically possible to learn how to generate syschar.xml files without using the oscap utility and implement fully agent-less remote scan. But this is one for the future.
System Characteristics Errors
Unfortunately, there were bugs during testing of oscap 1.2.16. The System Characteristics syschar.xml has been created successfully. But attempts to analyze it with oscap led to errors:
$ oscap oval analyse --results oval-results.xml com.ubuntu.$(lsb_release -cs).usn.oval.xml syschar.xml
E: oscap: Error occured when comparing a variable 'oval:com.ubuntu.focal:var:564810000000' value '0:5.4.0-126' with collected item entity = '0:5.15.0-1016'
E: oscap: Error occured when comparing a variable 'oval:com.ubuntu.focal:var:564710000000' value '0:5.4.0-126' with collected item entity = '0:5.4.0-1089'
E: oscap: Error occured when comparing a variable 'oval:com.ubuntu.focal:var:564410000000' value '0:5.4.0-126' with collected item entity = '0:5.15.0-1018'
...
OpenSCAP Error: Invalid type of operation in string evaluation: 6. [../../../../src/OVAL/results/oval_cmp_basic.c:195]At the same time, oval-results.xml was created and it was possible to generate an html report from it. But some of the checks are displayed in the error state.
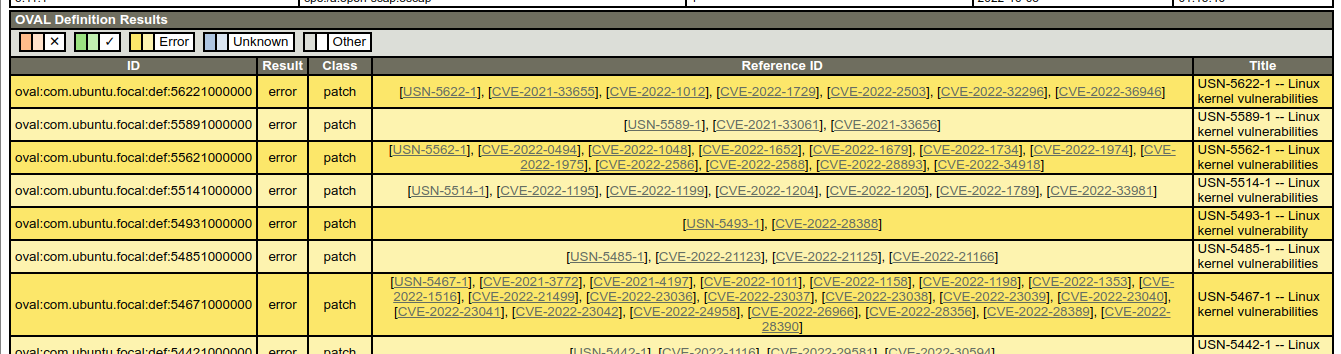
I suspect that the problem is in the current version of oscap in the Ubuntu repository (1.2.16) and in the current actual version 1.3.6 it may work, but this needs to be checked. To do this, OpenSCAP should be installed from source.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Погонял, по случаю, ScanOVAL - бесплатный сканер уязвимостей от ФСТЭК | Александр В. Леонов
Pingback: 13 мая стартует онлайн-хакатон от команды MaxPatrol VM Positive Technologies: получи реальный опыт в разработке правил детектирования уязвимостей на нейтр