Recently I had a chance to work with OpenSCAP. It’s a set of free and open-source tools for Linux Configuration Assessment and a collection security content in SCAP (Security Content Automation Protocol) format.
In this post I will write about SCAP Workbench. It is a GUI application that can check the configuration of your local Linux host (or the remote host via ssh; note that agent installation is required), and show the settings that are not comply with some security standard, for example PCI DSS or DISA STIG.
Moreover, you can generate the script for automated remediation. You can also create your own scan profiles based on existing SCAP content.
Installation
Installation is quite trivial. For CentOS 7 run:
# yum install scap-workbench ... Dependencies Resolved ================================================================================ Package Arch Version Repository Size ================================================================================ Installing: scap-workbench x86_64 1.1.6-1.el7 base 1.8 M Installing for dependencies: dwz x86_64 0.11-3.el7 base 99 k openscap x86_64 1.2.16-8.el7_5 updates 3.8 M openscap-containers noarch 1.2.16-8.el7_5 updates 27 k openscap-scanner x86_64 1.2.16-8.el7_5 updates 61 k openscap-utils x86_64 1.2.16-8.el7_5 updates 27 k perl-Thread-Queue noarch 3.02-2.el7 base 17 k perl-srpm-macros noarch 1-8.el7 base 4.6 k redhat-rpm-config noarch 9.1.0-80.el7.centos base 79 k rpm-build x86_64 4.11.3-32.el7 base 147 k rpmdevtools noarch 8.3-5.el7 base 97 k scap-security-guide noarch 0.1.36-9.el7.centos updates 4.4 M Transaction Summary ================================================================================ Install 1 Package (+11 Dependent packages) Total download size: 11 M Installed size: 167 M
For other Linux distributions check this official page.
Content
If you runscap-workbench command, the application will invite you to use some existing security content from SCAP Security Guide repository.

You can choose here content to load. Basically, security content is available for RHEL/CentOS and for Firefox and JRE installed on Linux:
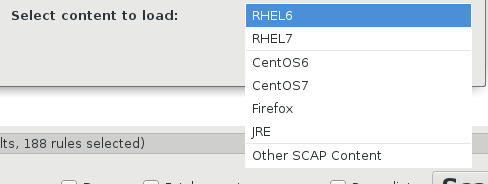
And select a profile that contains configuration requirements for some security standard:
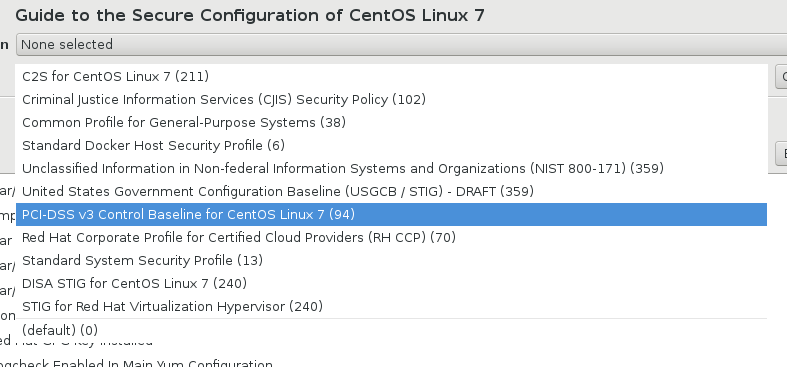
For CentOS Linux 7 the following profiles are available:
- C2S (U.S. Government Commercial Cloud Services) for CentOS Linux 7
- Criminal Justice Information Services (CJIS) Security Policy
- Common Profile for General-Purpose Systems
- Standard Docker Host Security Profile
- Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171)
- United States Government Configuration Baseline (USGCB / STIG) – DRAFT
- PCI-DSS v3 Control Baseline for CentOS Linux 7
- Red Hat Corporate Profile for Certified Cloud Providers (RH CCP)
- Standard System Security Profile
- DISA STIG for CentOS Linux 7
- STIG for Red Hat Virtualization Hypervisor
All the content is stored in /usr/share/xml/scap/ssg/content/:
$ ls /usr/share/xml/scap/ssg/content/ ssg-centos6-ds.xml ssg-jre-oval.xml ssg-centos6-xccdf.xml ssg-jre-xccdf.xml ssg-centos7-ds.xml ssg-rhel6-cpe-dictionary.xml ssg-centos7-xccdf.xml ssg-rhel6-cpe-oval.xml ssg-firefox-cpe-dictionary.xml ssg-rhel6-ds.xml ssg-firefox-cpe-oval.xml ssg-rhel6-ocil.xml ssg-firefox-ds.xml ssg-rhel6-oval.xml ssg-firefox-ocil.xml ssg-rhel6-xccdf.xml ssg-firefox-oval.xml ssg-rhel7-cpe-dictionary.xml ssg-firefox-xccdf.xml ssg-rhel7-cpe-oval.xml ssg-jre-cpe-dictionary.xml ssg-rhel7-ds.xml ssg-jre-cpe-oval.xml ssg-rhel7-ocil.xml ssg-jre-ds.xml ssg-rhel7-oval.xml ssg-jre-ocil.xml ssg-rhel7-xccdf.xml
Scanning local machine
I chose existing PCI DSS v.3 profile to scan my localhost with CentOS 7:
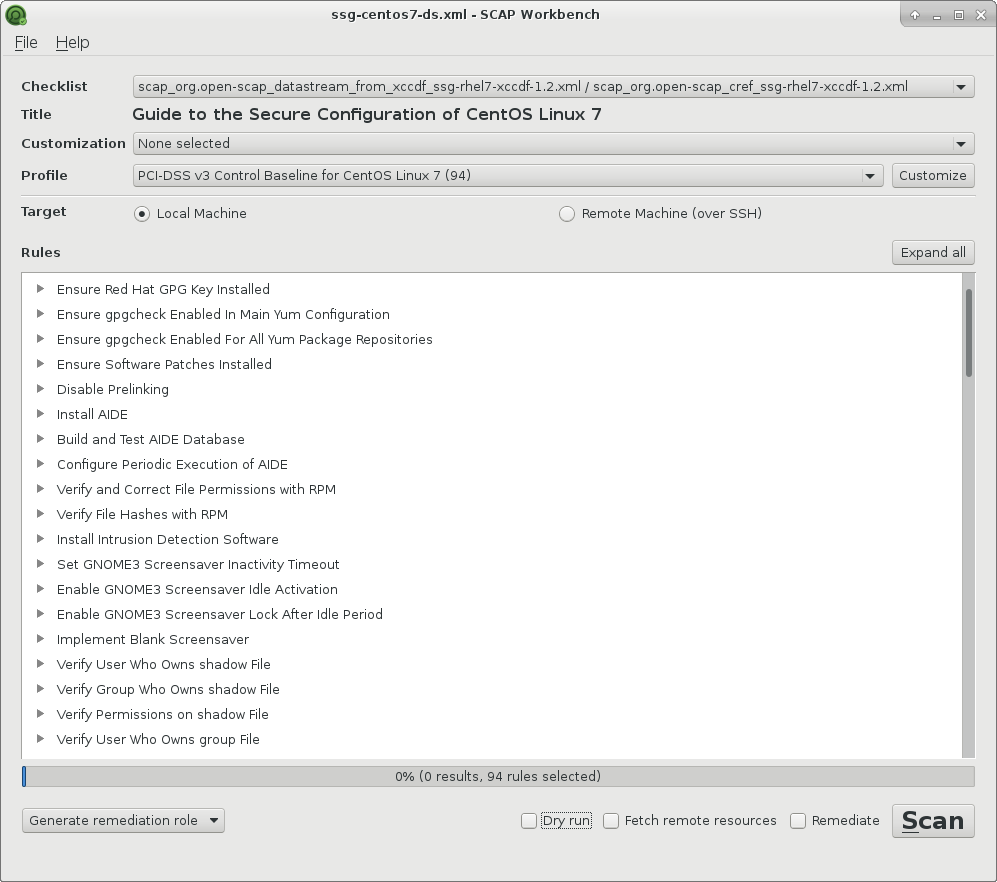
And pressed the Scan button:
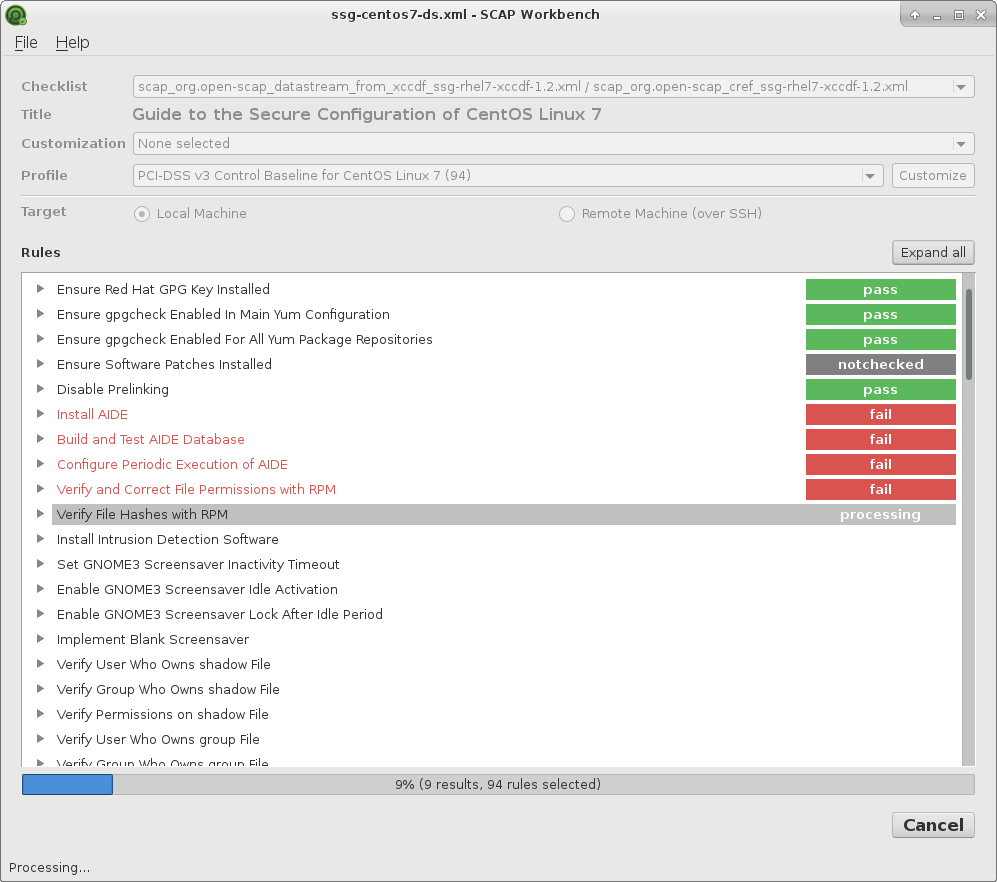
Scan results
When scan is finished you can get the results in HTML, ARF (Asset Reporting Format) or XCCDF Result format.
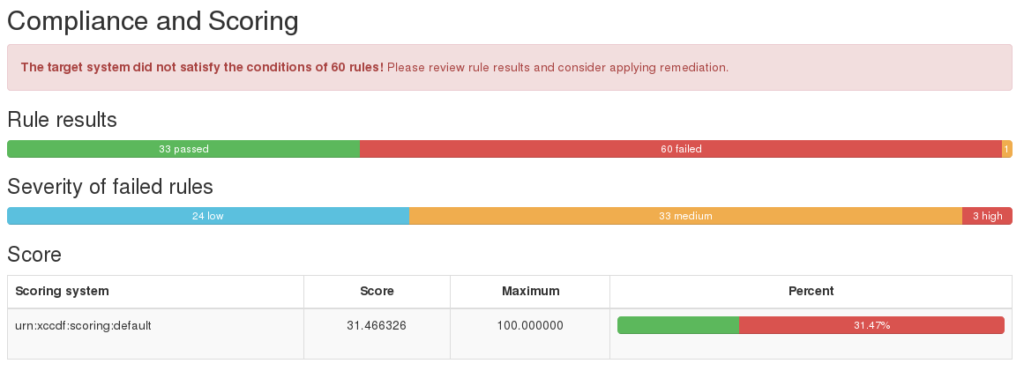
HTML report looks very cute:
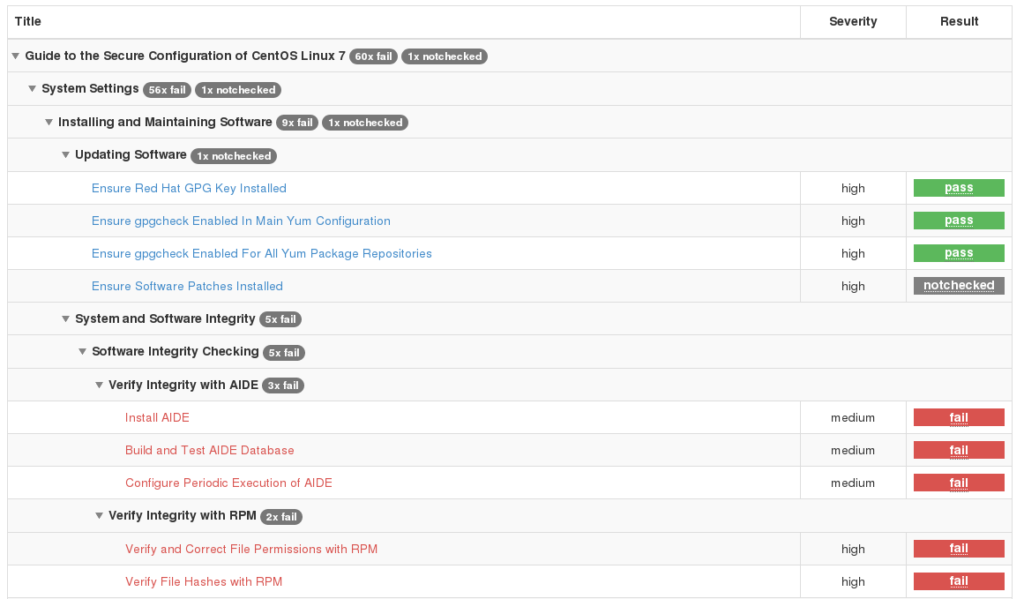
But even more interesting is that you can generate a remediation file: bash script, ansible or puppet. So, in theory, you can reconfigure the server automatically.
Scanning remote host
To launch the remote scan you specify username, host and SSH port:
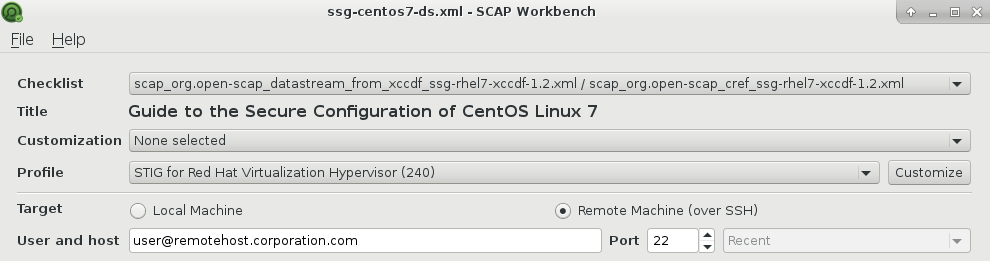
Note, that openscap-daemon should be installed on remote host, or you will get an error:
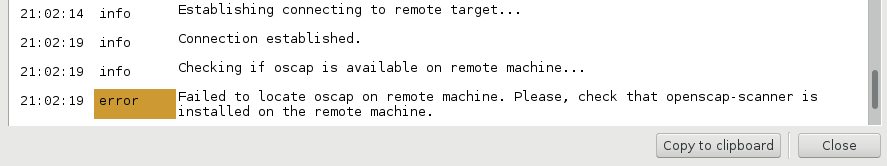
You can install it on remote server like this:
# yum install openscap-daemon
Then click Scan button, input the password:
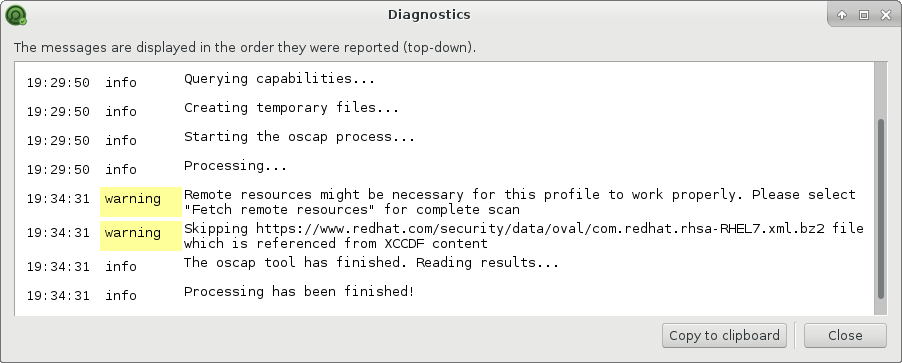
A few minutes after the scan will be completed:
Customizing the content
If you click on Profile -> Customize you can choose the checks:
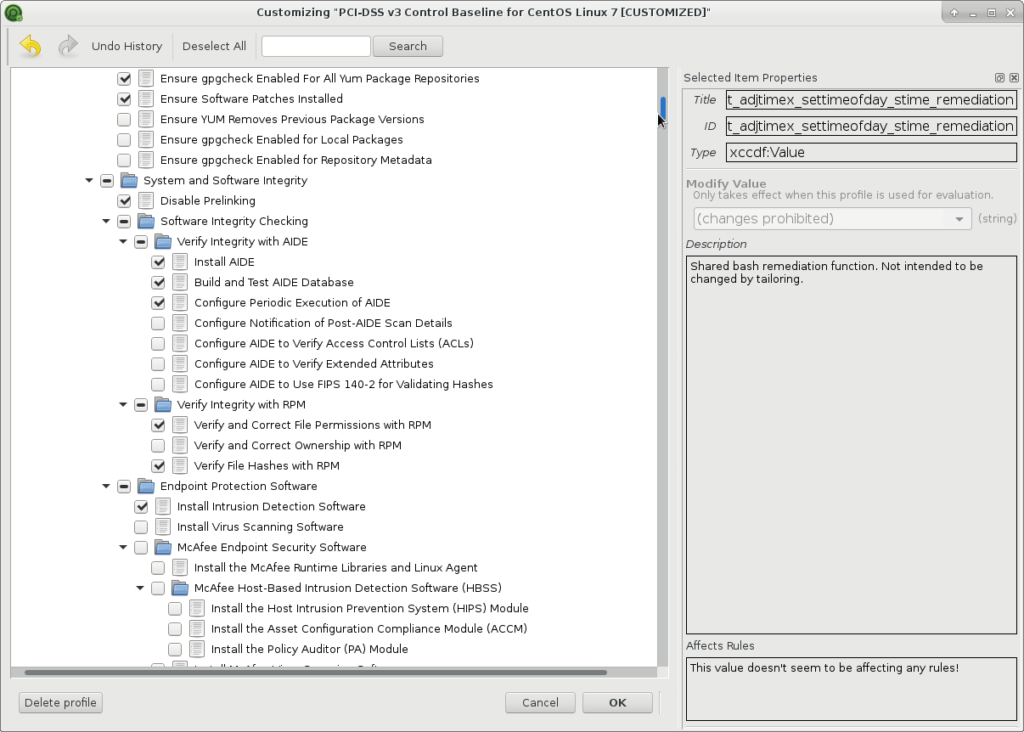
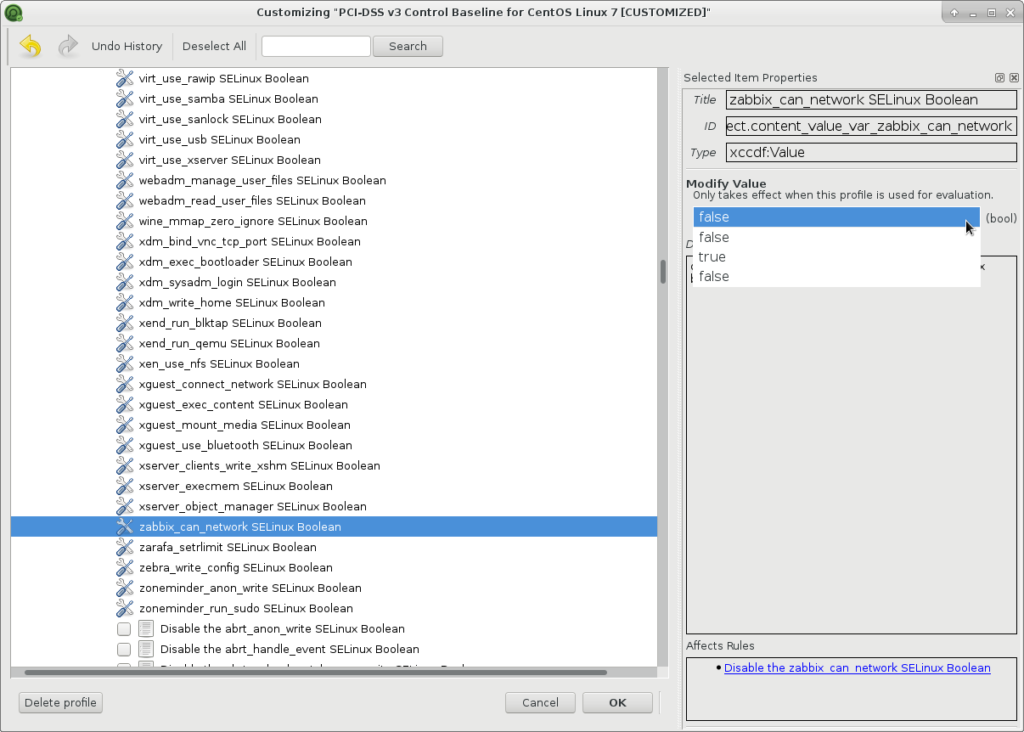
And set the values for global variables:
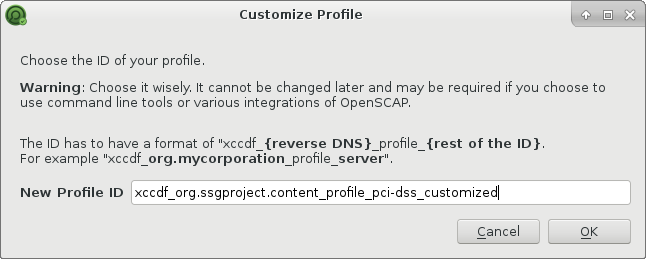
You can save the changes as a new profile:
And export data in DS and tailoring XCCDF:
$ ls ssg-centos7-ds.xml tailoring-xccdf.xml
In conclusion
- SCAP Workbench is a great choice if you need to make a fast assessment of your local host or several remote hosts in the network and generate remediation scripts.
- If you want to make an automated assessment process, you should use command line tools
oscapandoscap-ssh, but this is for another topic. 😉 - You can use SCAP Workbench to make your own standard based on existing profiles, but if you need to add own checks, you will need something more advanced.
- Unfortunately, SCAP Workbench can’t work with raw OVAL data, for example with the CIS OVAL vulnerability data. This data can be probably converted to some format SCAP Workbench understands, but I haven’t seen existing tools for this.
upd. On the official website there is a description how you can do it for RHEL. You need to download:
XCCDF: http://www.redhat.com/security/data/metrics/com.redhat.rhsa-all.xccdf.xml
OVAL: http://www.redhat.com/security/data/oval/com.redhat.rhsa-all.xml
And open this content with Scap Workbench:
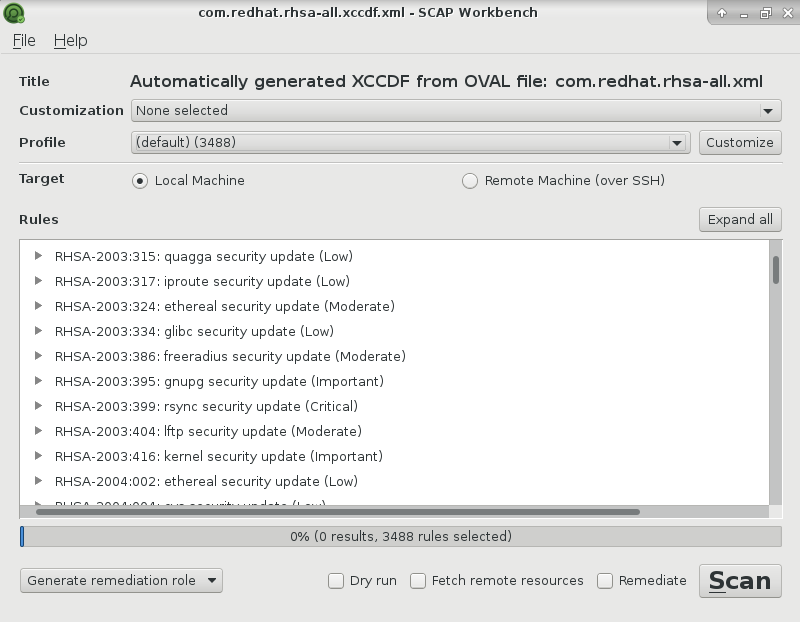
This is available only for Red Hat Enterprise Linux, but it’s a good example how this can be done.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: How to Perform a Free Ubuntu Vulnerability Scan with OpenSCAP and Canonical’s Official OVAL Content | Alexander V. Leonov