A little bit more about IT Asset Inventory of Internal Network, that your IT team can provide. 😉
I have recently worked with NetBox – an open source IP address management (IPAM) and data center infrastructure management (DCIM) solution developed by well-known cloud hosting provider DigitalOcean.

It’s not really about security, not even a CMDB. But, security team still might be interested in NetBox, because it makes possible to track the hosts in some critical subnet without active scanning, providing great visibility of assets. Here I will show a small example of NetBox API usage.
The task
Let’s say we want periodically check what hosts exist in some critical subnet (for example, 10.0.0.0/24) and send them to Splunk for further analysis. Here you can see how the active hosts are shown in the GUI of NetBox.
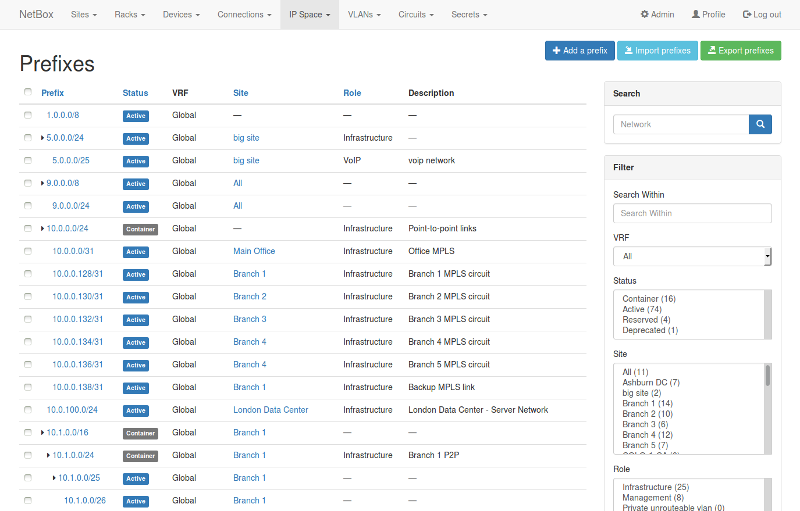
I’ve took this picture from the GitHub page of the project. But note that this thing is highly customizable and you IT team can add, for example a hostname in Description or in some custom field. To understand the API deeply, you can read the manual at readthedocs.io.
Authentication
To start using NetBox API, you will need a token. Go to your user profile:

Choose API Tokens -> Add a token:
And add it:
Request
A great thing about NetBox is that requests in it’s Web-GUI and API have very similar URLs. Dealing with API become very easy. For example, I found out that in GUI I can get the active hosts from 10.0.0.0/24 using this URL:
https://netbox.corporation.com/ipam/ip-addresses/?q=&parent=10.0.0.0/24
I added “api” before “ipam” and got this URL for the API helper page that shows me the results of API request in web browser:
https://netbox.corporation.com/api/ipam/ip-addresses/?q=&parent=10.0.0.0/24
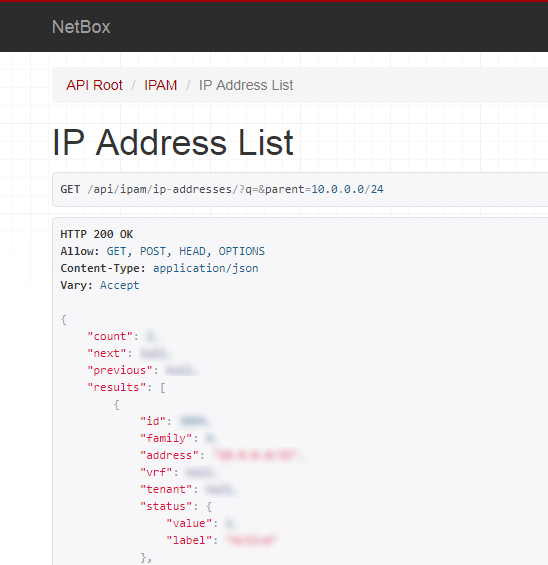
Here is the code for retrieving the ip addresses. It mostly about the dealing with pagination. NetBox will returns only 50 entities in one response. So, I make a first get request and then make the requests of ‘next’ url in the results until it will be null().
import requests
import json
import urllib
headers = {
'Authorization': 'Token 348uafgioh3498u89efjgoi2o0r2930rskjp1039',
}
subnet = "10.0.0.0/24"
response = requests.get('https://netbox.corporation.com:443/api/ipam/ip-addresses/?q=&parent=' + str(urllib.quote_plus(subnet)), headers=headers, verify=False)
all_results = json.loads(response.text)['results']
next_url = json.loads(response.text)['next']
while next_url:
print(next_url)
response = requests.get(next_url, headers=headers, verify=False)
all_results += json.loads(response.text)['results']
next_url = json.loads(response.text)['next']
print(all_results[0])
The script will show the next urls:
https://netbox.corporation.com/api/ipam/ip-addresses/?cf_isSeenLastTime=1&limit=50&offset=50&parent=10.0.0.0%2F24&q=
https://netbox.corporation.com/api/ipam/ip-addresses/?cf_isSeenLastTime=1&limit=50&offset=100&parent=10.0.0.0%2F24&q=
...
And the first ip structure fromall_results:
{u'status': {u'value': 1, u'label': u'Active'}, u'nat_inside': None, u'last_updated': u'2017-07-17T16:07:27.071273Z', u'description': u'important.server.corporation.com', u'family': 2, u'tags': [], u'nat_outside': None, u'created': u'2017-07-17', u'custom_fields': {u'field1': True, u'field2': False}, u'role': None, u'vrf': None, u'address': u'10.0.0.2/32', u'interface': None, u'id': 2027, u'tenant': None}
Then you can send these IPs to Splunk using HTTP Event Collector, track the appearance of new hosts and visualise it on dashboards.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
