A few days ago I saw an interesting youtube video (UPD. 14.05.18 Not available anymore). It is demonstrating the exploitation of the RCE vulnerability in Tenable Nessus Professional 7.0.3. Currently we have very few information about this vulnerability: only youtube video, which is mentioned only on ExploitWareLabs.
While there is no exploit in public access, it’s hard to say how it actually works. It’s also not clear what versions of Nessus are affected. 7.0.3 is the latest version currently. Because of API disabling in Nessus 7 many users are still on 6.11.3. It is not clear whether they are affected or not.
This even can be a fake video. Therefore, I specifically write “potential RCE”. I will update this post when more data is available.
UPD. 14.05.18 In the comments to my post anonymous account Destring Portal posted a comment with the second video of Nessus RCE exploitation and it seems, that it was made by the same author. In this video, the author runs a remote shell on the Nessus host and executes various commands. I will add review of this second video bellow.

UPD. 10.05.18 Renaud Deraison, Co-Founder and CTO of Tenable, commented on my post at Linkedin:
Our research team studied the video and we have several reasons to doubt its authenticity. We’ve conducted a thorough audit over the last 48 hours based the few details that are in the video and didn’t find anything. We reached out the researcher and instead of replying he removed the video*. We’ll communicate if indeed there is a risk.
In general, you are right though – the security of scanners is of paramount importance. This actually is a topic I’ve been extremely worried about ever since the early days of Nessus. We have a number of security mechanisms in place (interpreted language for the detection scripts, ciphered temporary files, very limited runtime environment) which really aim to limit the risk of being exploited but also to mitigate the risk should the scanner be compromised. I actually did a few talks in the past about scanning “rogue hosts” and we continue to treat all input as hostile.
Again, we’re continuing to investigate the matter and will let you know if we find anything.
* currently video is still available on the same address; it could be probably blocked for some time. (UPD. 14.05.18 Not available anymore)
In any case, it’s a good reason to talk about vulnerabilities of such kind, how they appear and how to protect Vulnerability Scanners from attackers.
What do we see on the video?
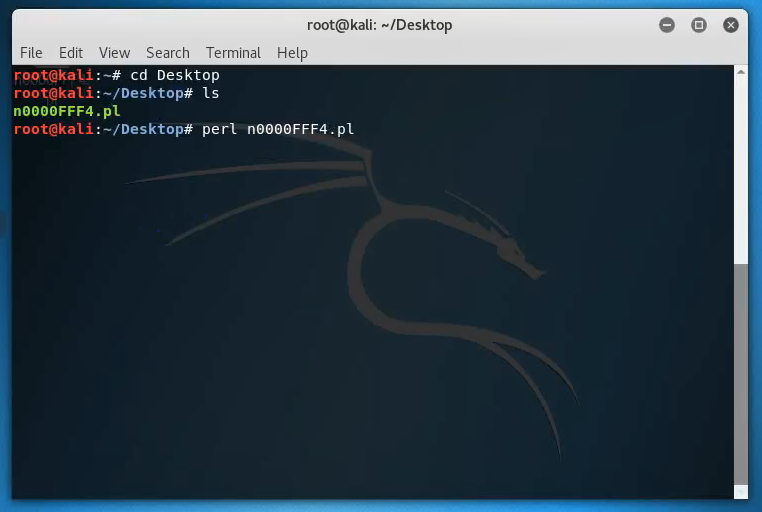
The video lasts 2.5 minutes (UPD. 14.05.18 Not available anymore). We see the Windows OS screen with two active windows. The left window is Firefox web-browser with Nessus7 GUI. Nessus is deployed on the same Windows host.
The right window is VirtualBox with Kali Linux. On the Kali Linux desktop, we see the Perl script n0000FFF4.pl.
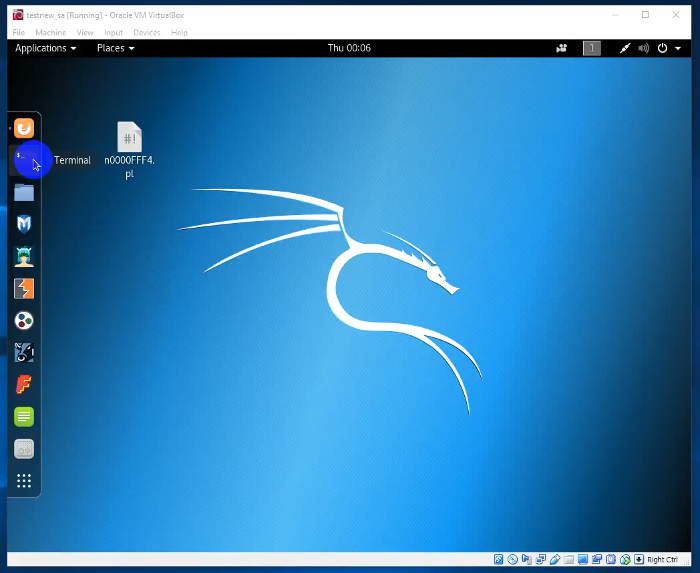
Author of the video shows us IP-address of the virtual machine with Kali Linux: 192.168.88.13
Then it runs the script n0000FFF4.pl:
Author of the video creates a scan in Nessus with standard profile Web Application Tests,
He sets remote Kali virtual machine 192.168.88.13 as a target:
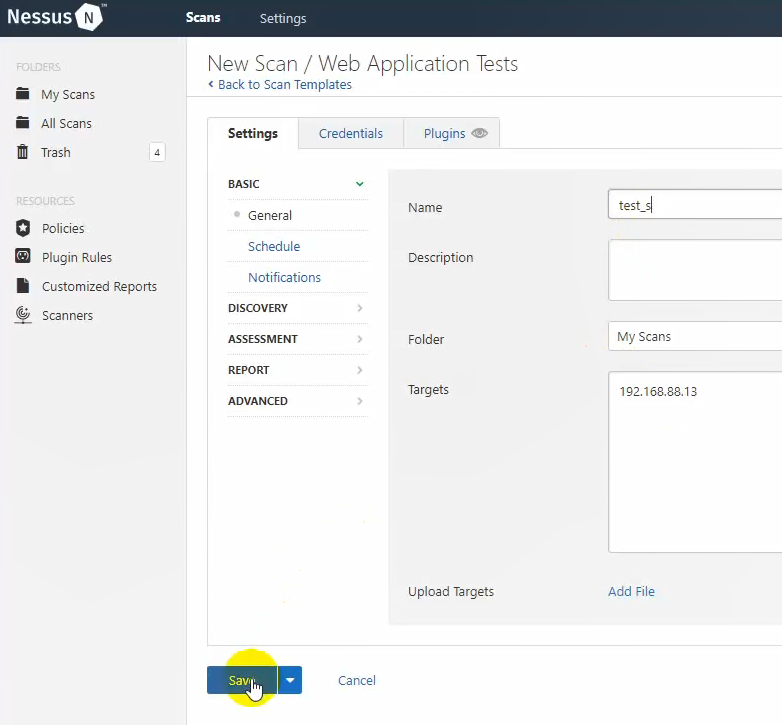
And lauches the scan:
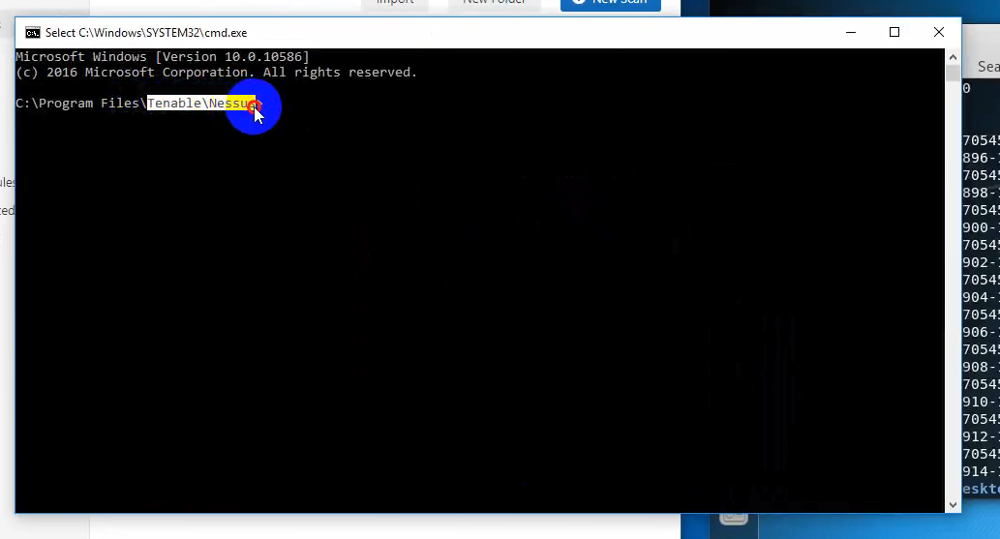
In 5 seconds after the script is launched, Windows shell appears with the active directory C:\Program Files\Nessus. This should indicate that it was possible to execute arbitrary code on the Nessus host.
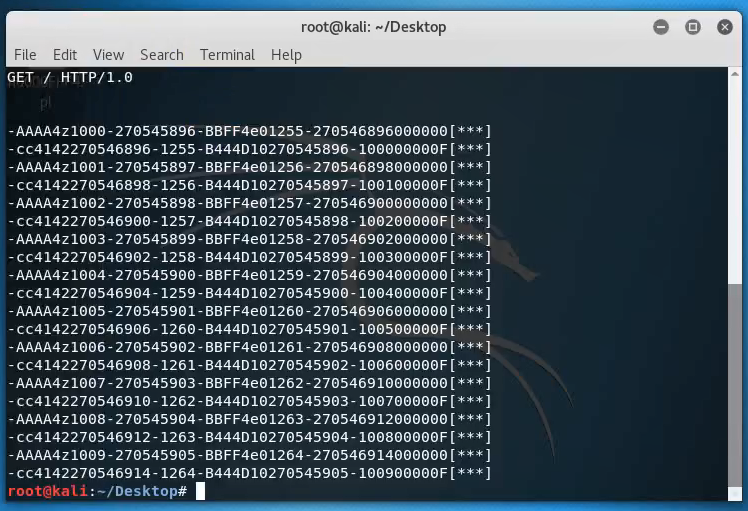
At the same time, in the output of the script in Kali virtual machine, we see:
AAAAz1000-270545896…
Then author of the video stops the scan, restarts the script in Kali, restarts the scan in Nessus and in 5 seconds Windows shell appears once again and we see the same output of the script in Kali. This shows that the script is stable. Then he shows it again, re-creating Nessus scan task.
How this video could be faked?
It can be a fake video and probably it doesn’t proof anything. Such behavior can be easily simulated by the script on Windows machine that checks Nessus scan statuses in Nessus logs. After 5 seconds from the scan launch this script executes Windows shell and terminates script in Kali virtual machine with some mysterious message. =) Or even simpler, author of the video could launch the shell and stop script by pressing keys on keyboard.
But it’s also possible that this is a real and advanced exploit. In this case, this exploit could easily be used privately for several years, before it will finally leak and become public. Like in EternalBlue case.
Second video: remote shell
The second video is called “Tenable Nessus Professional 7.0.3_ RCE demo2_win”, it was published yesterday, at May 13, 2018. Description of the video:
The video is pretty similar to the first one. We see the Nessus scanner window and Kali Linux VirtualBox window. There is a n0000FFF4.pl script in Kali. The exploitation also looks the same: Nessus starts scanning Kali Virtual Machine and an attacker gets control on Nessus Windows host after 5 seconds.
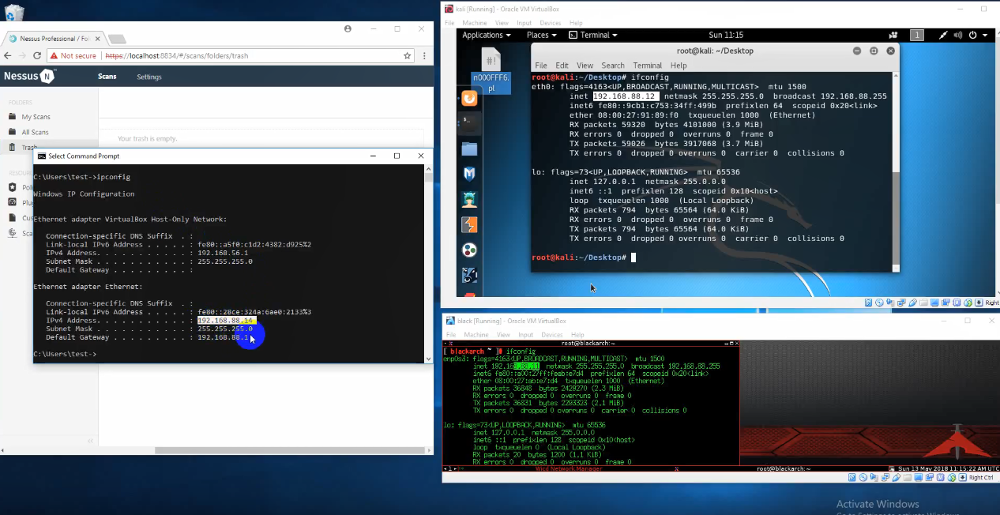
But in this case we see one more Virtual Machine with BlackArch Linux. Note, that we see the time in BlackArch: Sun 13 May 2018 11:15:12 AM UTC. It looks real.
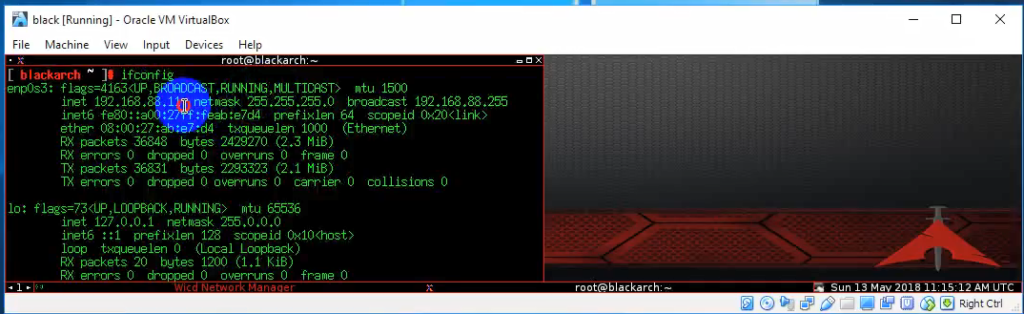
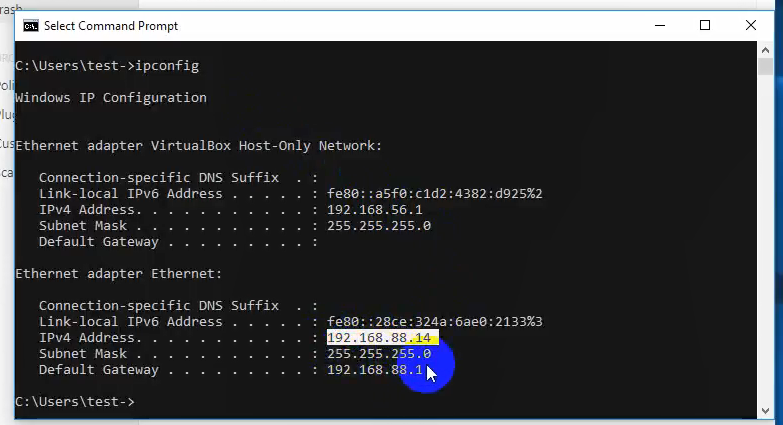
The author of the video shows us the IP address of Nessus Windows host:
And then tries to connect with Ncat to Nessus Windows host on 443 port: `nc 192.168.88.14 443` from BlackArch host.
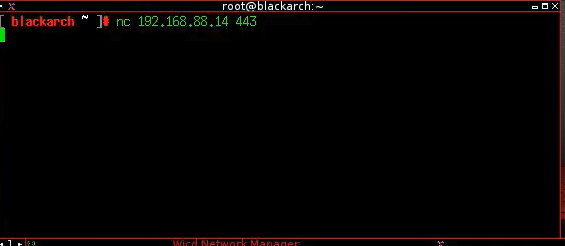
And after he starts scanning Kali Linux host with Nessus, the connection become established:
This should mean that author of the video was able to upload and launch remote shell on the Nessus Windows host during the the Kali scan. Now everyone can connect to 192.168.88.14:443 and execute any commands on Windows host. He shows the output of `ipconfig` with an IP:
Lists Nessus directory:
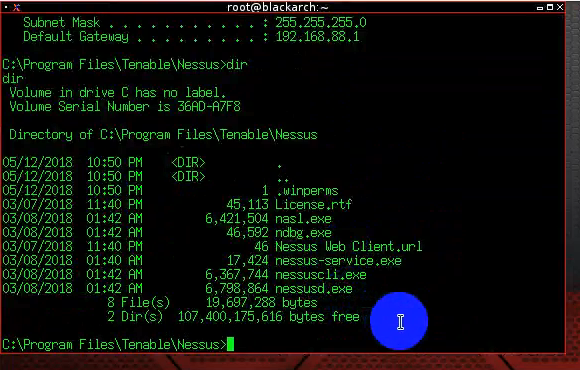
And finally he launches calculator and notepad with `calc` and `notepad`:
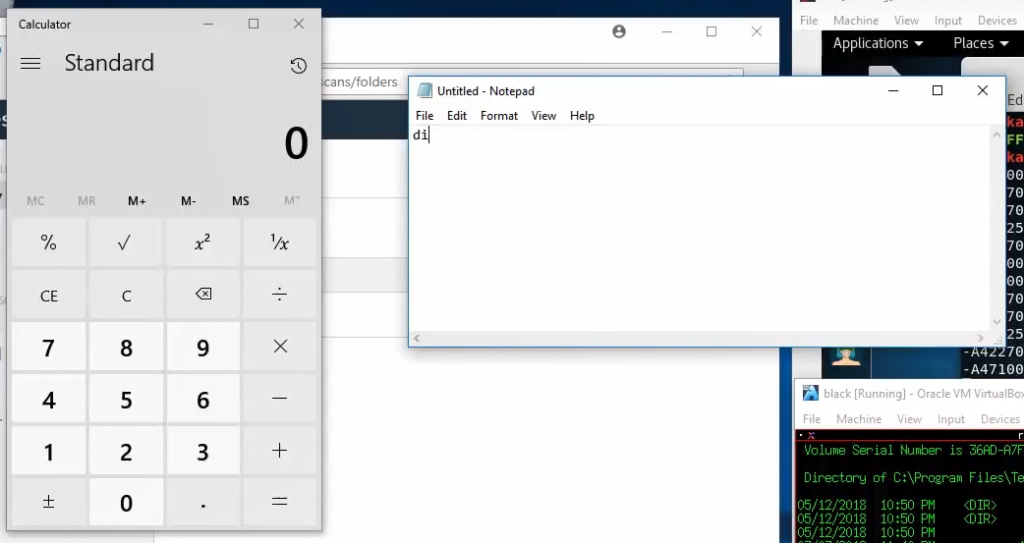
It looks impressive. And still doesn’t proof anything and can be falsified. So, decide for yourself, do you believe it or not.
How is this theoretically possible?
Vulnerability Scanner is quite a complicated tool. It performs various interactions with the remote target host, executes commands, receives data and somehow interprets it. In theory, as well as any other program, Vulnerability Scanner may contain bugs/vulnerabilities related to processing invalid data that was not filtered properly. This is most likely the cause here. Of course if this video is real.
Not only Nessus
A similar vulnerability was found, for example, in the Acunetix 9.5 web application scanner in 2015. It also makes possible remote code execution on the scanner host. The problem was in Microsoft Windows OleAut32.dll.
Exploit code: https://vulners.com/exploitdb/EDB-ID:36516
Demonstration: https://www.youtube.com/watch?v=n1TYHJxQLAM
RCE was also found in Acunetix WVS 10 in 2016, but it required some user interaction.
Exploit code: https://vulners.com/exploitdb/EDB-ID:39755
Demonstration: https://www.youtube.com/watch?v=gWcRlam59Fs
Great target for attack
Vulnerability Scanner is an excellent target for attack because:
- Scanner host must reach each target is scans. If it will be compromised it become ideal base for performing an attack. If scanning solution is licensed by amount of deployed scanners, there will be only a few of them in the infrastructure, may be even one. Such centralization is very convenient for an attacker.
- If the scanner is used for Credentialed Scanning, attacker can try to use these credentials, after getting control on scanner. In the case of Nessus, he can do it easily, for example, by running malicious .audit scripts on remote hosts.
How can we make exploitation of such vulnerabilities harder?
- Scan only the hosts that belong to your organization. Scanning someone else’s hosts can be nearly illegal in some countries.
- Try not to run a Vulnerability Scanner with root privileges.
- Scan your perimeter with the Scanner deployed outside of your network. So, the attacker will not get inside your network in any case.
- Update your Vulnerability Scanner regularly. This will not save you from 0day vulnerabilities. But at the time of active exploitation, you will be already protected.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.