Today I spoke at SOC Forum 2017 in Moscow. It was a great large-scale event about Security Operation Centers. 2,700 people registered. Lots of people in suits 😉 . And lots of my good fellows.

The event was held in Radisson Royal Congress Park. There were three large halls for presentations and a huge space for exhibition/networking.
I would like to mention а stand of Positive Technologies. They have shown today their new PT Security Intelligence Portal with dashboards for executives and joint service with Solar Security for providing GosSOPKA functionality. Some stands were dedicated to Russian government Information Security initiatives: GosSOPKA, BDU FSTEC vulnerability database and FinCERT of the Central Bank of Russia.
During my presentation, I was talking how massive malware (ransomware) attacks can be useful for an organization. Quite a provocative topic, right? 😉 I meant it in the sense that all the hype around malware attack can help Information Security team to do the the following things:
- Establish useful policies, like mandatory Windows host reboot after patch installation
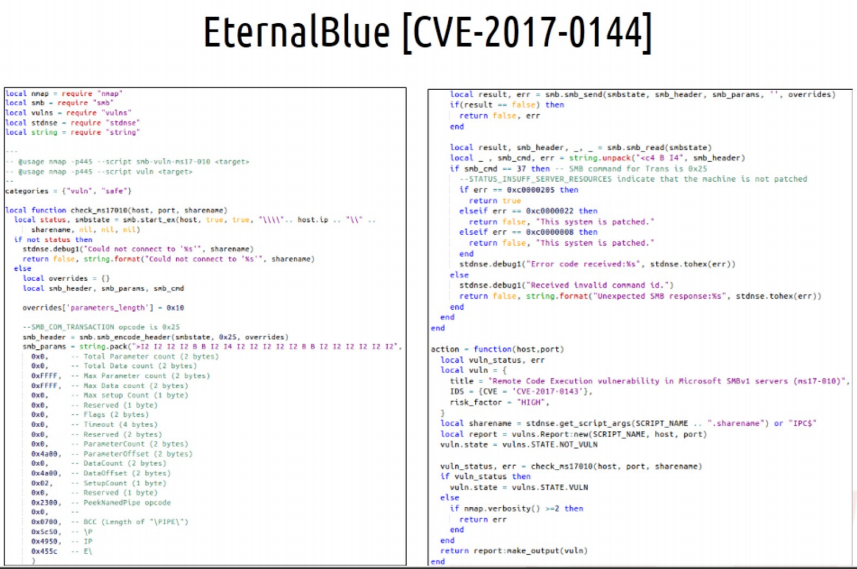
- Ban some convenient, but dangerous functionality, like smb file sharing between workstations
- Implement useful processes, like system hardening (e.g. against mimikatz) or continuous processing of CERT (FinCERT) bulletins
All this actions may cause a highly negative reaction among employees. But when you have a fresh example of company highly damaged recently by some ransomware attack it will be much easier deal with all such reactions. But you should act fast, hype won’t last long. 😉
However it’s a very bad practice to use the attacks for justifying a purchase of expensive “silver bullet” solution. There is no solution that will make your processes better.
I mentioned all three main ransomware attacks that happened this year and described why they are not very interesting from Vulnerability Management point of view. I also talked about problems of patching. You can read more about this in “WannaCry about Vulnerability Management“, “Petya the Great and why *they* don’t patch vulnerabilities” and “Vulnerability Management vendors and massive Malware attacks (following the Bad Rabbit)“.
I also used two slides from my “ISACA Moscow Vulnerability Management Meetup 2017” presentation about the kinds of relationships Information Security (Vulnerability Analysts) and IT can have, and how it can influence on effectiveness of Vulnerability Management program.
I would like to mention a great presentation by Mona Arkhipova “Measuring SOC efficiency: The devil is in the detail“. Also a very interesting presentation that I unfortunately was unable to see, because it was hold at the same time as mine: Yuriy Bosov from Acribia “How can the analyst of SOC in 20 minutes determine which of the clients are in danger of a newly published vulnerability?” (rus). It was about pretty original way for vulnerability detection based on exploit analysis and Nmap NSE script generation.
It was a nice event. Thanks to the organizers! Hope to visit SOC Forum 2018 next year.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Potential RCE in Nessus 7 and attacks on Vulnerability Scanners | Alexander V. Leonov