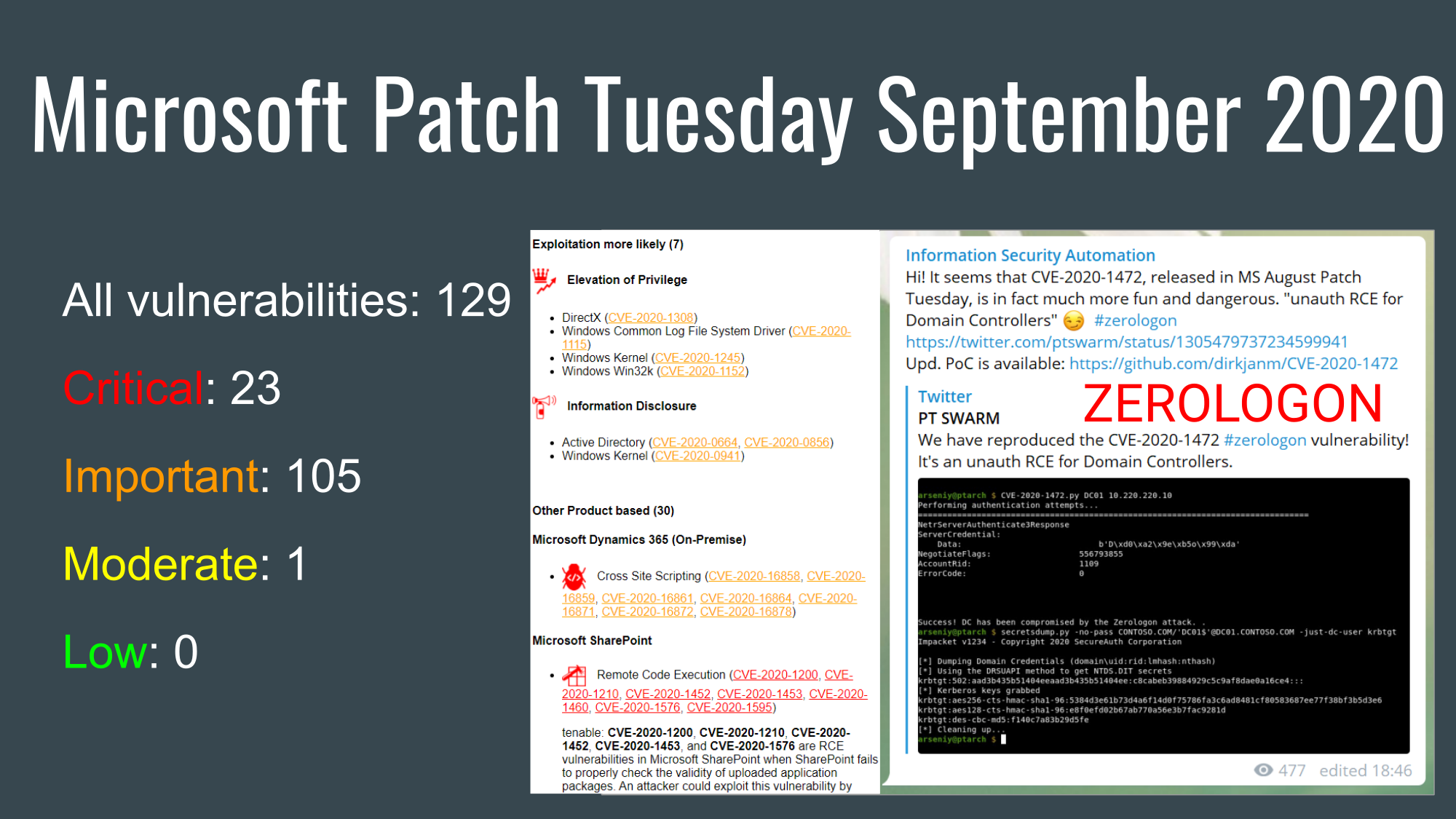
Last Tuesday I was invited to Microsoft business breakfast “Effective protection against targeted and multilevel attacks”. Here I would like to share some of my thoughts on this. Need to mention that the food was delicious and the restaurant of Russian Geographical Society is a very lovely place. 😉 Thanks, Microsoft!
Microsoft as a security vendor? O RLY?
Microsoft products are not actually my topic. To tell you the truth, personally I’d better live in a world without this massive Windows hegemony in desktop operating systems. I use Linux mostly. And even when I have to work in a Windows environment, it’s much easier for me to do all the work in some Linux virtual machine.
But in the real life almost every office network is build on Microsoft solutions. And if you are doing Vulnerability Management in any organization, you should deal with them too. The good news is that many security features are available out of the box in the MS products that you have already purchased. It’s just important to know about these features and use them right.
One more thing, why it’s interesting to learn more about Microsoft information security products. Microsoft developers, obviously, have direct access to Windows source code and know better how their own OS works. Many things are much easier for them to implement than for other security vendors. So, good chances that you will see in Microsoft products some interesting features, that other vendors don’t have (yet).
Drowning in data
The event began with an opening speech by Andrey Ivanov from Microsoft Russia.

I liked his thesis that “we are drowning in security data”:
- Threat Intelligence from different sources that need to be implemented in your infrastructure and somehow validated. A good place to mention Vulners.com vulnerability feeds 😉
- Threat Detection using logs, scanners, various protection tools, etc.
- The overall number of SIEM inputs is growing faster than our resources. New IT system = new problems of SIEM configuration.
So, it would be nice if somebody, for example OS vendor, will provide all this as a service, right? 😉
Detect the undetectable
Then there was the keynote by Zbigniew Kukowski – one of the leading Microsoft information security experts.
Why is it necessary?
Here is what I would like to note from his report. First of all, great arguments why it is necessary. Ok, this is marketing. But the ability to explain (to sell) necessity of information security is important skill for any information security specialist now. It does not matter if you are working in a security vendor, integrator or customer.
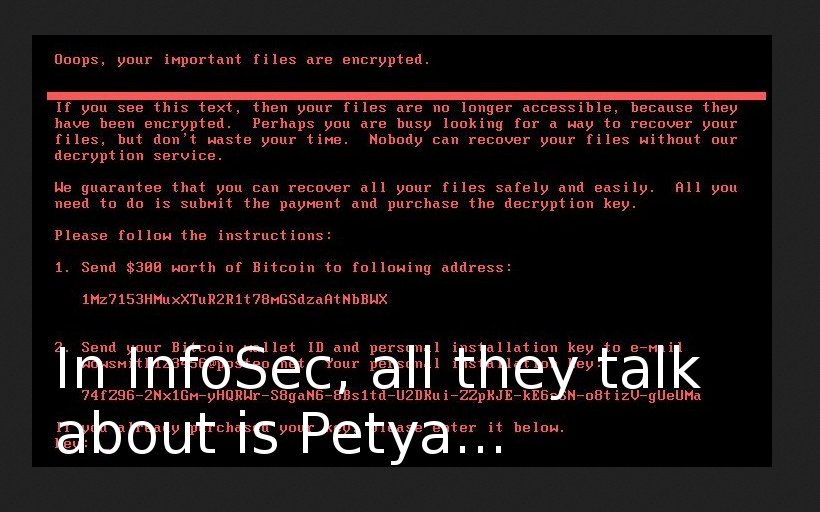
Zbigniew mentioned an interesting case: some Polish company, that lost $ 4.3 million in recent the Petya attack in 4 days. The cost of Information Security measures will be much less than the potential losses of business.
Another argument – attacks are not the entertainment for some individuals any more. Now it’s a well-organized criminal business. Dozens of people are working on popular malware tools, like Petya. That’s why ransomware tools are so popular now – cyber-criminals just want to return their development costs.
Continue reading →