I really like this. Just imagine. Quiet, routine, everyday Vulnerability Management process in organizations: scanning-patching, scanning-patching, scanning-patching… And then. Suddenly! PEEETYYA!!!
And at very same moment everything changes. People from different companies start to communicate with each other actively, reverse this new malware, share the data, write and share tools for detection and recovery. Security professional is a friend, a brother and a source of useful information for security professional. Real movement! Real community! =)
For example, my friends from Vulners.com created pretty popular gist about Petya (petrWrap, notPetya, GoldenEye) and updated in real time for several hours.
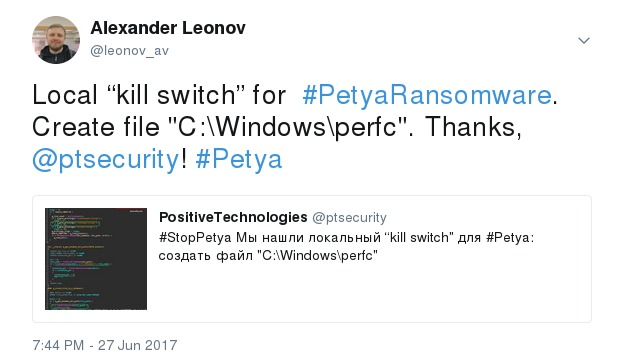
My former colleagues from Positive Technologies released detailed technical review of this ransomware (in Russian) few hours since the outbreak started, at 01:00 am . They also found a local kill switch, and probably were the first one. Simultaneously with Amit Serper from Cybereason.
 ‘
‘
Of course, for many people and organizations it’s nothing but business: good opportunity to show competence in analysis, detection, protecting, remediation and maybe the way to find new customers and to impress current customers. I do not think that it is bad until they don’t sell inefficient and overpriced products.
From the Vulnerability Management point of view there is nothing new in Petya. As far as we know now it uses all the known issues:
- CVE-2017-0199 – arbitrary code execution via crafted MS Office document. Patched by “Security Update for Microsoft Office Products (April 2017)”
- CVE-2017-0144 (ETERNALBLUE) – Windows SMB remote code execution. Patched by MS17-010 at 14 March 2017
- mimikatz – open-source tool for extracting plaintext passwords, hashes, PIN codes and kerberos tickets from memory. Read article “Defending Against Mimikatz“. Current version of the tool is in public since last summer.
You can detect this vulnerabilities, with Nessus authenticated scan or using any other vulnerability scanner.
As you can see, without any expensive 0day vulnerabilities attackers successfully infected Banks, Telecom, Businesses and Power Companies, mainly in Ukraine and Russia. Last time, when I wrote about WannaCry, I made a pretty obvious conclusion, that affected organisations have problems with Patch and Vulnerability Management. =) This time I want to put on my IT administrator hat and to give some reasons why vulnerabilities in that organisations were not patched, even after WannaCry.
Vulnerability patching is an endless, time-consuming and expensive process. Especially when you are dealing with thousands of hosts.
- For Windows and MS products there are standard updating tools. But, updating other really exploitable software: web-browsers, Adobe products, Java, etc. is a real pain. It requires either manual work or expensive patching solutions.
- You need to check every patch before updating. And you always need to choose between hypothetical ransomware attack and paralysing the work in your organisation after unsuccessfully patch installation.

- Updating mechanisms can break, and updates, for some reason, won’t be installed. To detect this, you need a separate Vulnerability Management process, that also has his own difficulties.
- Various legacy issues:
- Critical vulnerable software that is strongly needed for work and can’t be updated, because it requires paying extra money and investing in staff retraining
- Critical software, that requires outdated vulnerable libraries. It mostly about Java
- Legacy operating systems that only can run some critical software
- Users who do not want to reboot their desktops for installing updates, users who want local admin rights and install any software. They do not care about the security in the organization, they only think about their own convenience. Arguing with them also takes time and nerves.
- Windows systems are important for an organization, but there are also network devices, virtualization, Linux and MacOS X hosts and in all this there are vulnerabilities. Moreover, IT administrators can perform many other tasks besides patching.
Large amount of work and a lack of human resources slows the whole process. That’s why full patching of some critical vulnerability in organisation may take months.
The only way to intensify this process (read: to get more people and money on Vulnerability and Patch Management solutions), is to show that threat is real, to count possible damage from a successful attack and the costs of necessary countermeasures for the systems, where regular patching is not an option, including reliable backups.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Petya, M.E.Doc and the problem of trust | Alexander V. Leonov
Pingback: Dealing with cybersquatting, typosquatting and phishing | Alexander V. Leonov
Pingback: Vulnerability Management vendors and massive Malware attacks (following the BadRabbit) | Alexander V. Leonov
Pingback: SOC Forum 2017: How I Learned to Stop Worrying and Love Massive Malware Attacks | Alexander V. Leonov
Pingback: Microsoft security solutions against ransomware and APT | Alexander V. Leonov
Pingback: MIPT/PhysTech guest lecture: Vulnerabilities, Money and People | Alexander V. Leonov
Pingback: Code IB 2019: Vulnerability Management Masterclass | Alexander V. Leonov
Pingback: CyberCentral Summit 2018 in Prague | Alexander V. Leonov