A very good news! Vulners Team is ready to present complete functionality for vulnerability audit. And it’s not just an Audit API that you have to use somehow in your own scripts, but an enterprise ready product, like agent-based vulnerability scanning in Qualys and Tenable.
You can try it for free. Let’s see how to do it. For example we have a CentOS 7 server and we want to see vulnerabilities of this host in Vulners.
We go to the server.
ssh vmuser@192.168.56.102
$ uname -a
Linux localhost.localdomain 3.10.0-514.el7.x86_64 #1 SMP Tue Nov 22 16:42:41 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
Vulners repostory
First of all, we need to add repository with agent:
$ su -
# echo -e "[vulners]\nname=Vulners Agent\nbaseurl=https://repo.vulners.com/redhat/el7/\nenabled=1\ngpgcheck=0" > /etc/yum.repos.d/vulners.repo
So, the vulners.repo file will look like this:
# cat /etc/yum.repos.d/vulners.repo
[vulners]
name=Vulners Agent
baseurl=https://repo.vulners.com/redhat/el7/
enabled=1
gpgcheck=0
Vulners agent
Installation process is trivial. One yum command:
# yum install vulners-agent.noarch
Loaded plugins: fastestmirror
base | 3.6 kB 00:00
extras | 3.4 kB 00:00
updates | 3.4 kB 00:00
vulners | 2.9 kB 00:00
(1/5): base/7/x86_64/group_gz | 155 kB 00:00
(2/5): vulners/7/primary_db | 1.8 kB 00:00
[...]
Resolving Dependencies
--> Running transaction check
---> Package vulners-agent.noarch 0:0.1.21-el7 will be installed
--> Finished Dependency
[...]
Installing:
vulners-agent noarch 0.1.21-el7 vulners 11 k
[...]
Total download size: 11 k
Installed size: 16 k
[...]
Installing : vulners-agent-0.1.21-el7.noarch 1/1
Verifying : vulners-agent-0.1.21-el7.noarch 1/1
Installed:
vulners-agent.noarch 0:0.1.21-el7
Complete!
Look how tiny agent is! Just a few kilobytes!
Getting an API key
Agent will send some information from the host to Vulners.com site. But how will Vulners decide whose host is it? It will be possible because of API key that you can generate an vulners.com web-site.
- Login at vulners.com
- Go to https://vulners.com/userinfo -> API KEYS
- Choose Scope “scan” and press “Generate new key”
You will get key like “HXKM3OMDIYGJLJ60MPM1X51AKC3XTD9Z28J78X12T2OC2MXSTKMMBN70EMMIQUSS”
Configuring the agent
Now when you have a key, you can add it to the config at /opt/vulners/conf/vulners.conf:
# cat /opt/vulners/conf/vulners.conf | sed 's/api_key =.*/api_key = HXKM3OMDIYGJLJ60MPM1X51AKC3XTD9Z28J78X12T2OC2MXSTKMMBN70EMMIQUSS/' > /tmp/vulners.conf; cp /tmp/vulners.conf /opt/vulners/conf/vulners.conf
The file should look like this:
# cat /opt/vulners/conf/vulners.conf
[main]
debug = false
[agent]
api_host =
ipaddr =
fqdn =
agent_id =
api_key = HXKM3OMDIYGJLJ60MPM1X51AKC3XTD9Z28J78X12T2OC2MXSTKMMBN70EMMIQUSS
Running the agent
Durring the installation this cron task will be created for regular scanning every 2 hours:
# cat /etc/cron.d/vulners_cron
#perform agent activity every 2 hours
0 */2 * * * nobody /opt/vulners/agent.py
But of course you can run it manually anytime with /opt/vulners/agent.py
Note, that it is pure python and you can figure out how it works and see what system information will be collected.
If you run this script it won’t make any output, but you can see it in /opt/vulners/logs/vulners.log
For example, execution of bash commands:
2017-06-20 19:14:41,122 DEBUG Executing ssh command - 'cat /etc/os-release'
2017-06-20 19:14:41,123 DEBUG Full ssh command - 'echo cbee7080; cat /etc/os-release; echo a2e63014 || echo 098a2231'
2017-06-20 19:14:41,125 DEBUG SSH Command result - 'cbee7080
NAME="CentOS Linux"
VERSION="7 (Core)"
ID="centos"
ID_LIKE="rhel fedora"
VERSION_ID="7"
PRETTY_NAME="CentOS Linux 7 (Core)"
ANSI_COLOR="0;31"
CPE_NAME="cpe:/o:centos:centos:7"
HOME_URL="https://www.centos.org/"
BUG_REPORT_URL="https://bugs.centos.org/"
CENTOS_MANTISBT_PROJECT="CentOS-7"
CENTOS_MANTISBT_PROJECT_VERSION="7"
REDHAT_SUPPORT_PRODUCT="centos"
REDHAT_SUPPORT_PRODUCT_VERSION="7"
a2e63014
'
Or this API request with information need for vulnerability assessment and and responce with founded vulnerabilities:
2017-06-20 19:14:42,730 DEBUG {"agentId": "SEG1JBGFKVL6QQ1K2KSK3DCWE84LK3BAJJODU2CGKWNUGHWWYJS3U7OF3EKAOZ12", "apiKey": "HXKM3OMDIYGJLJ60MPM1X51AKC3XTD9Z28J78X12T2OC2MXSTKMMBN70EMMIQUSS", "os": "centos", "version": "7", "package": ["NetworkManager-team-1.4.0-12.el7.x86_64", "centos-release-7-3.1611.el7.centos.x86_64", "NetworkManager-wifi-1.4.0-12.el7.x86_64", [...] "rsyslog-7.4.7-16.el7.x86_64", "iprutils-2.4.13.1-1.el7.x86_64kernel-tools-3.10.0-514.el7.x86_64", "kernel-tools-libs-3.10.0-514.el7.x86_64", "kernel-3.10.0-514.el7.x86_64"]}
2017-06-20 19:14:43,079 DEBUG {"id": ["CESA-2016:2972", "CESA-2017:1308", "CESA-2016:2702", "CESA-2017:0294", "CESA-2016:2615", "CESA-2017:0286", "CESA-2017:1481", "CESA-2017:1382", "CESA-2017:1095", "CESA-2016:2824", "CESA-2017:0933", "CESA-2017:0386", "CESA-2016:2674", "CESA-2016:2779", "CESA-2017:0907", "CESA-2017:0086", "CESA-2017:1365", "CESA-2017:0276", "CESA-2017:1100", "CESA-2017:0062", "CESA-2016:2872"]}
During the first agent launch it will register automatically at vulners.com and will add unique agent_id in the config file, as well as fqdn of the host.
# cat /opt/vulners/conf/vulners.conf
[main]
debug = false
[agent]
api_host =
ipaddr =
fqdn = localhost.localdomain
agent_id = SEG1JBGFKVL6QQ1K2KSK3DCWE84LK3BAJJODU2CGKWNUGHWWYJS3U7OF3EKAOZ7I
api_key = HXKM3OMDIYGJLJ60MPM1X51AKC3XTD9Z28J78X12T2OC2MXSTKMMBN70EMMIQUUI
Dashboards at Vulners.com
Now you can go https://vulners.com/audit and see the results:
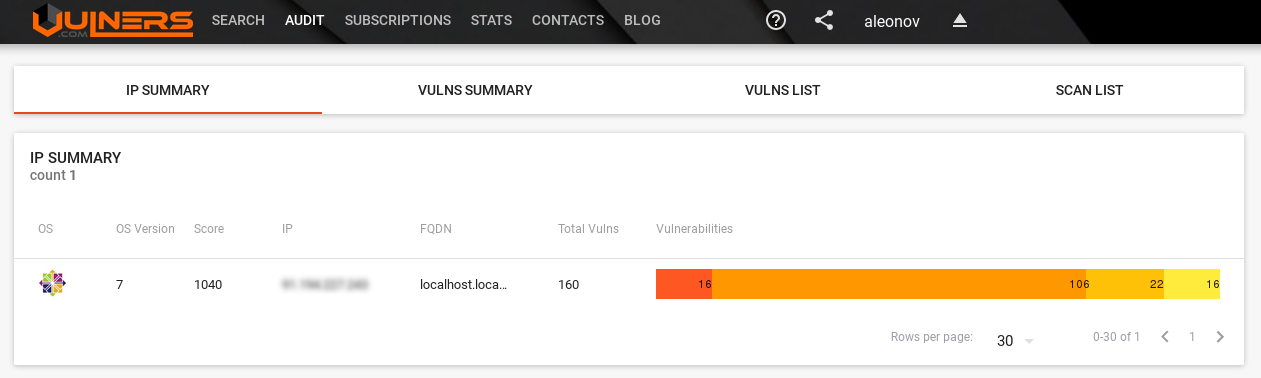
IP Summary tab with vulnerabilities of assets:

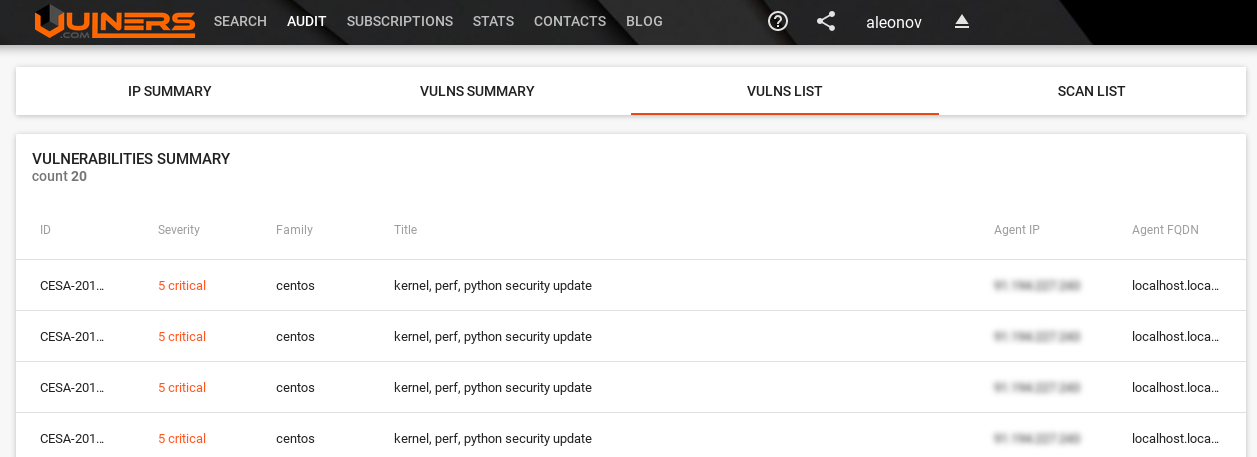
If you click on asset Vulns List will be opened with all vulnerabilities of the host:
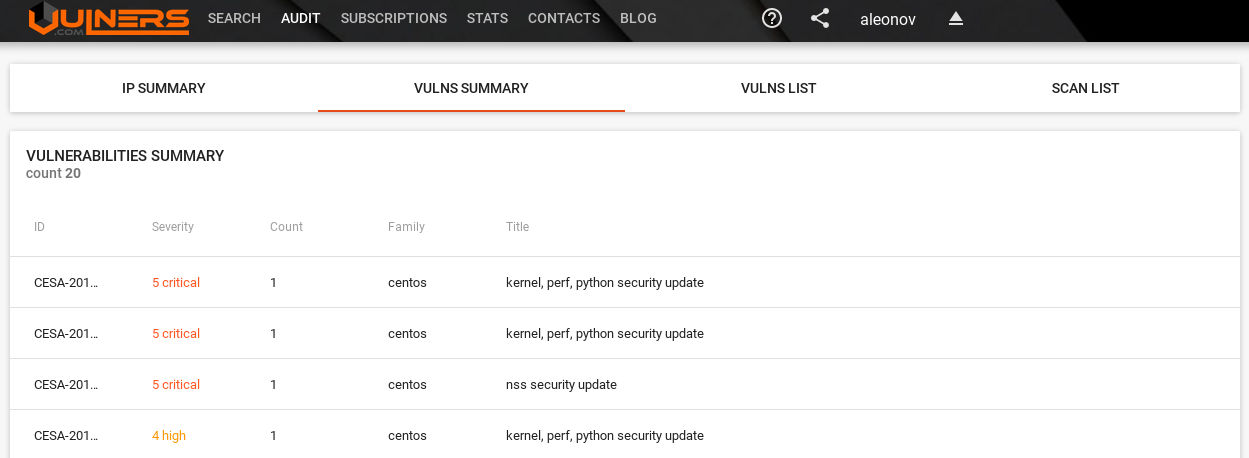
Vulns Summary tab with all vulnerabilities:
You can filter assets and vulnerabilities using special filters in the left part of screen:
If you click on the vulnerability, you will see description:
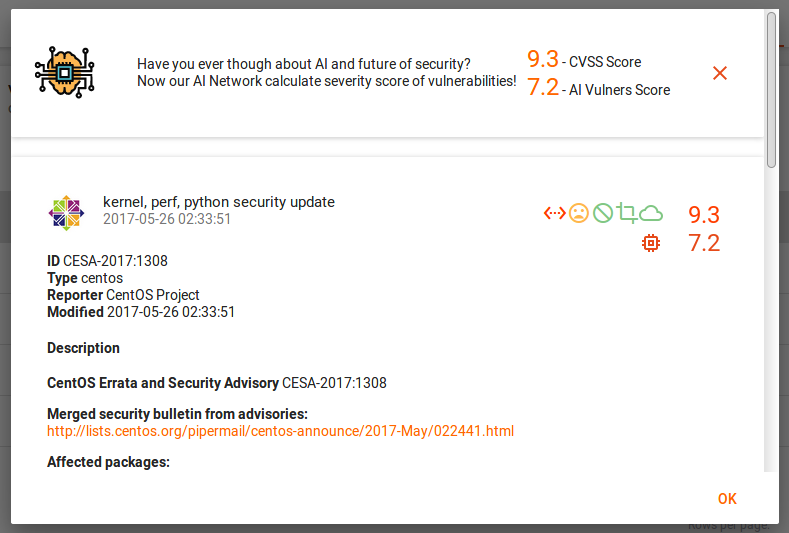
And finally the list of all scans:
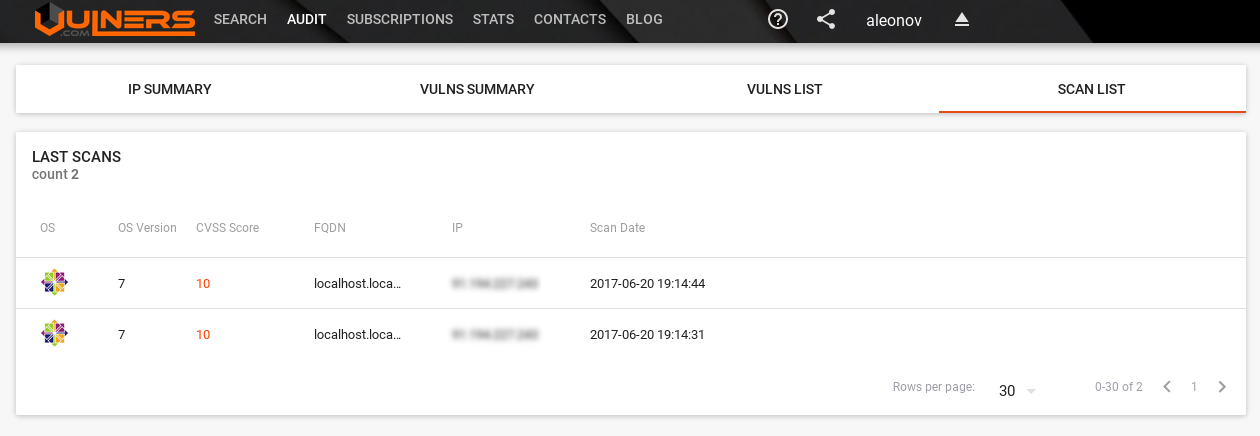
As you can see, the GUI is already quite powerful and will get even better. And if you do not want to store vulnerability scan results in a cloud solution, you can also try Vulners on-premise. If you are interested, please write to isox@vulners.com 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
