Today I would like to write about Qualys agent-based VM scanning. Agent-based scanning is a relatively new trend among VM vendors. At the beginning of Vulnerability Assessment, there was a prevailing view that the agentless scanning is more convenient for the users: you do not need to install anything on the host, just get credentials and you are ready to scan.

However, time passed and it now appears that installing agents on all hosts, where it is technically possible, may be easier, than managing credentials for authenticated scanning. Don’t forget the fact that almost all agentless scanning solutions require scanning account with root/admin privileges, and it’s not an easy task to minimize permissions of this accounts while keeping all functional capabilities of the scanner.
In recent years almost all major VM vendors who previously were promoting agentless scanning have also proposed agent-based solutions.
The main purposes of these solutions are:
- scan devices that periodically connect to the enterprise network and it’s hard to catch them with traditional active scan (for example, laptop);
- scan business critical hosts for which it is impossible to get scanning credentials.
VM vendors have taken different approaches for agent-based scanning. For example, Tenable agents are technically very similar to Nessus installations without web interface (read more at “Nessus Manager and Agents“), limited to can scan only the localhost. This seems reasonable, because historically Nessus scanner is available for many platforms, including Windows, Linux, MacOS. Qualys chose other way. They made minimalistic agents for data gathering, processing it on the remote servers. This is also fits well in Qualys cloud concept.
As I wrote earlier in “Qualys Vulnerability Management GUI and API“, Qualys working hard to make their web interface easier for beginners. When you go to CA (Cloud Agents) tab, the first thing you see is a user-friendly interface for quick start.
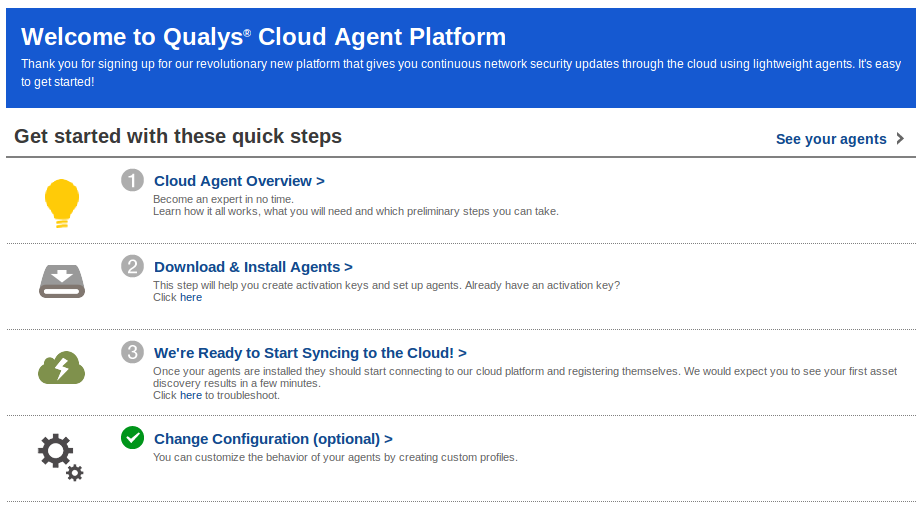
Installation
To install new agents, you need an activation key. Cloud Agent will use this key to authenticate on Qualys server. To create a new key, select CA (Cloud Agents) in the main menu, go to “Activation Keys” tab, and click on “create new” button.
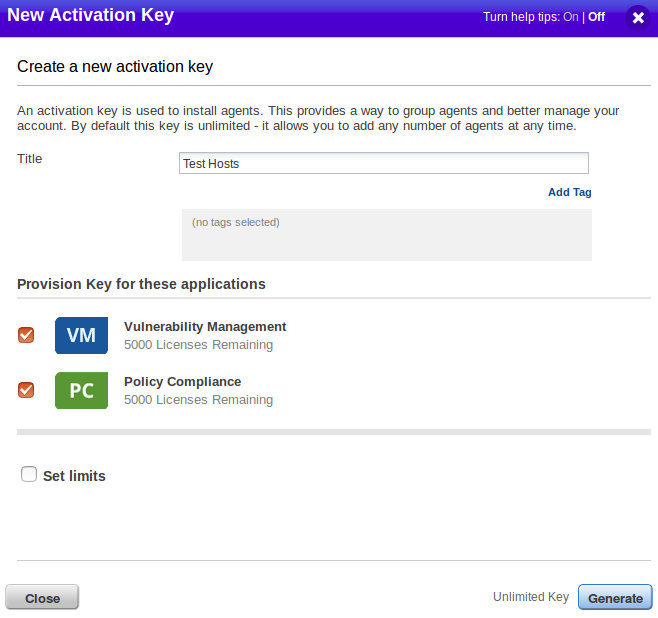
You may set the limits for your activation keys: maximum number of installed agents or date of expiration. In the interface you can see our a new activation key.
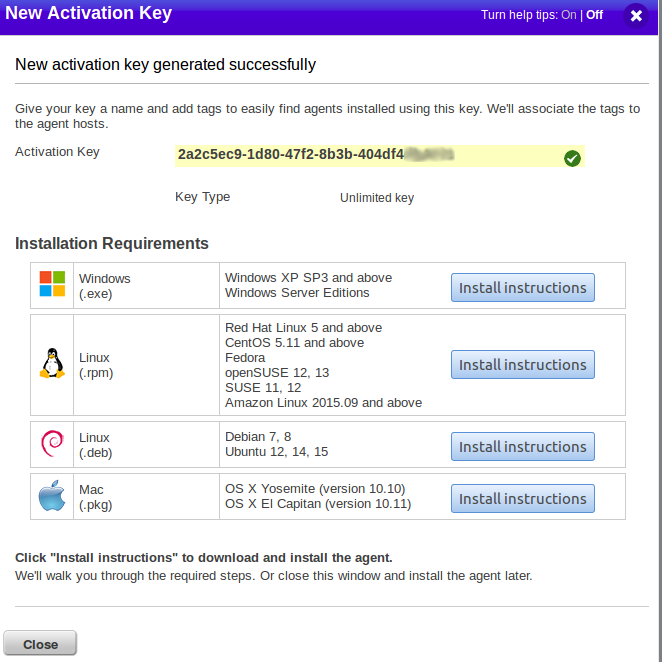
Qualys offers packages for the following platforms.
Windows (.exe):
- Windows XP SP3 and above
- Windows Server Editions
Linux (.rpm):
- Red Hat Linux 5 and above
- CentOS 5.11 and above
- Fedora
- openSUSE 12, 13
- SUSE 11, 12
- Amazon Linux 2015.09 and above
Linux (.deb):
- Debian 7, 8
- Ubuntu 12, 14, 15
Mac (.pkg):
- OS X Yosemite (version 10.10)
- OS X El Capitan (version 10.11)
For each package, there are detailed installation recommendations and link for download. As you can see, there is a command that you need to run on the host.
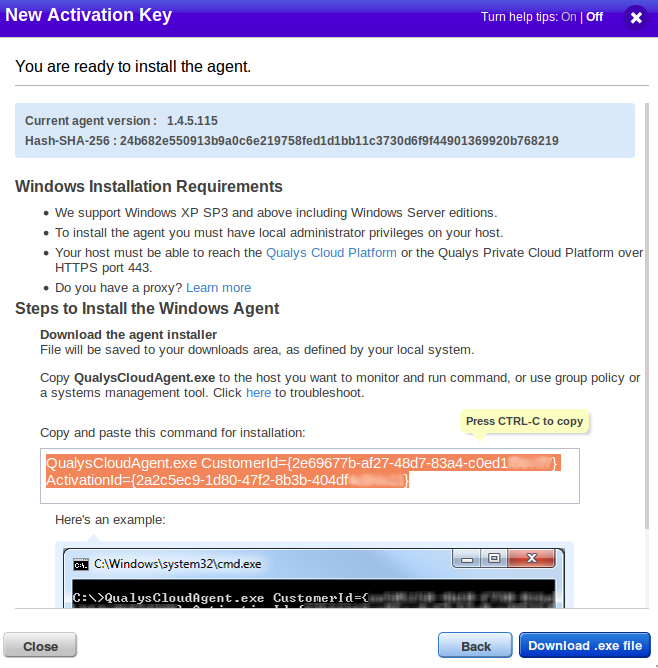
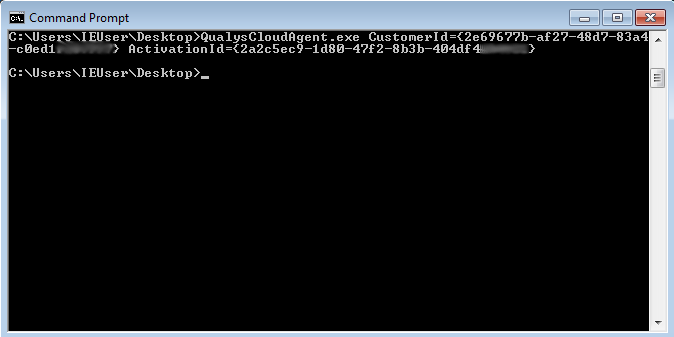
This one is for Windows:
QualysCloudAgent.exe CustomerId={2e69677b-af27-48d7-83a4-c0ed1XXXXXXX} ActivationId={2a2c5ec9-1d80-47f2-8b3b-404df4XXXXXX}
This one is for Linux Cloud Agent:
sudo rpm -ivh qualys-cloud-agent.x86_64.rpm
sudo /usr/local/qualys/cloud-agent/bin/qualys-cloud-agent.sh ActivationId=2a2c5ec9-1d80-47f2-8b3b-404df4XXXXXX CustomerId=2e69677b-af27-48d7-83a4-c0ed1XXXXXXX

I will install agents for Windows and CentOS Linux systems only. Here are installation scripts for other systems:
Linux (deb):
sudo dpkg –install qualys-cloud-agent.x86_64.deb
sudo /usr/local/qualys/cloud-agent/bin/qualys-cloud-agent.sh ActivationId=2a2c5ec9-1d80-47f2-8b3b-404df4XXXXXX CustomerId=2e69677b-af27-48d7-83a4-c0ed1XXXXXXX
Mac:
sudo installer -pkg ./qualys-cloud-agent.x86_64.pkg -target /
sudo bash -c ” if [[ -f /usr/local/qualys/cloud-agent/bin/qualys-cloud-agent.sh ]]; then /usr/local/qualys/cloud-agent/bin/qualys-cloud-agent.sh ActivationId=2a2c5ec9-1d80-47f2-8b3b-404df4XXXXXX CustomerId=2e69677b-af27-48d7-83a4-c0ed1XXXXXXX; else /Applications/QualysCloudAgent.app/Contents/MacOS/qualys-cloud-agent.sh ActivationId=2a2c5ec9-1d80-47f2-8b3b-404df4XXXXXX CustomerId=2e69677b-af27-48d7-83a4-c0ed1XXXXXXX; fi”
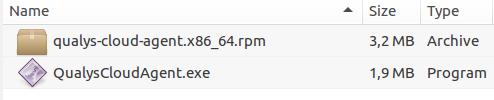
I have downloaded the packages. As you can see, Qualys Agent Packages are very small, less than 2-3 mb:
Everything is ready for installation. At first I installed the agent on a Windows 7 virtual machine:
Installation is very quick. As a result, we can see the process in the list of Qualys Windows processes. Qualys did not try to hide it.
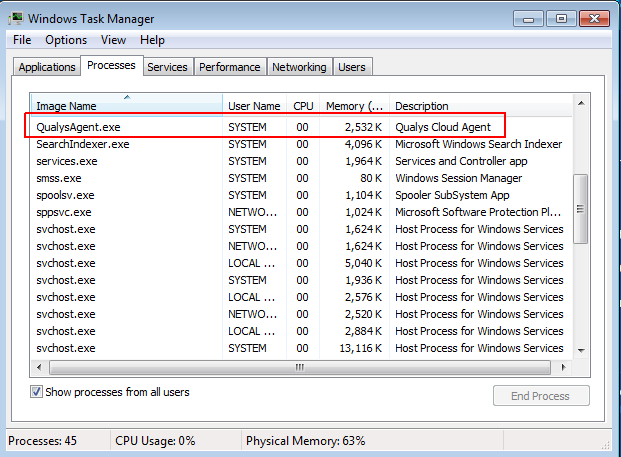
Now it’s time to install the Qualys agent for CentOS:
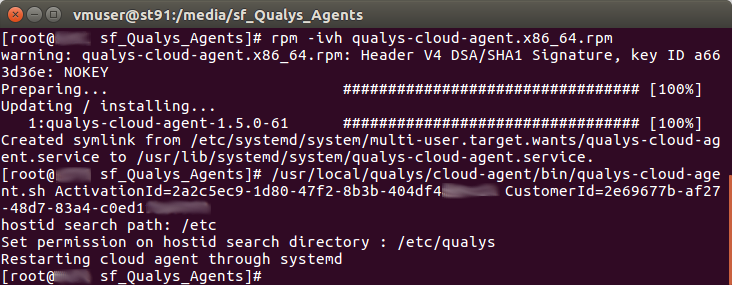
As you can see, the agent process is also visible, and you can easily control that agent is running:
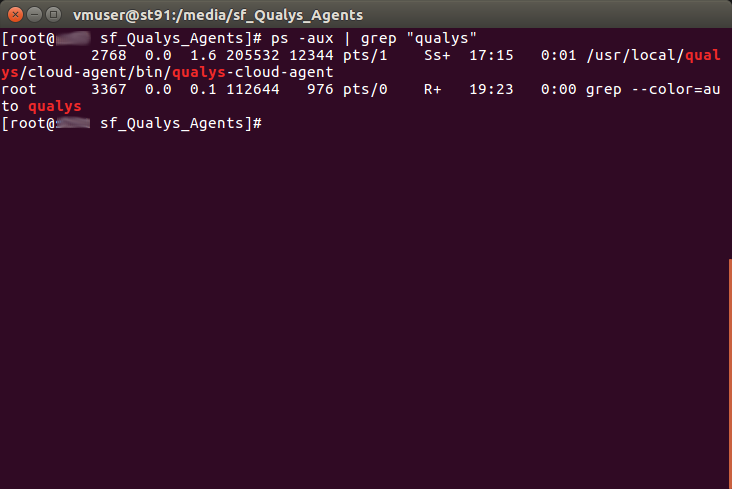
That’s all. Installation is complete. As you can see, everything is very simple and you can easily automate it. Regarding the network settings – make sure that the agent can set connection with Qualys the server.
Results
Almost immediately after installation is finished, we can see our hosts in the list of agents.
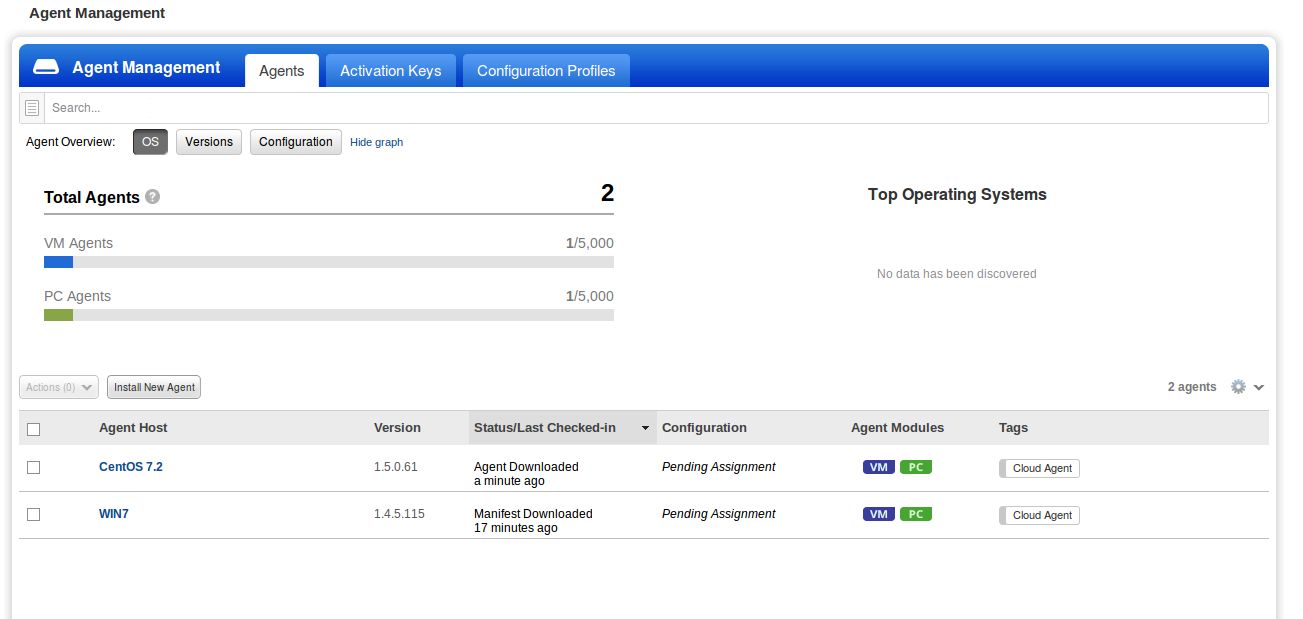
However, information about them will appear gradually and slowly. I do not know if Qualys minimize the load on the host tries, where the agent is installed or in the case of optimization work at Qualys server. The fact that the inventory information is refreshed me 3 hours. A vulnerability added more than 6 hours. This, of course, is unacceptable if we want to get results quickly exploitable.
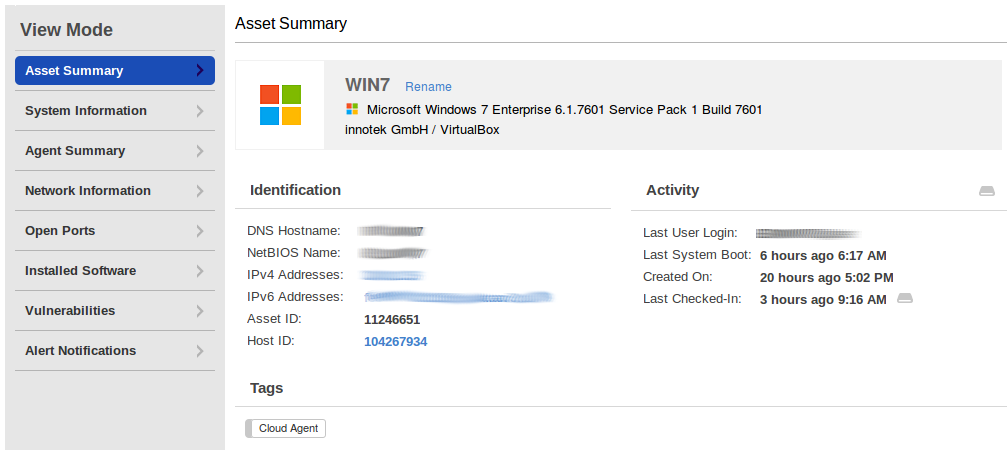
What information is collected about the host? Asset Summary is the hostname and network addresses.
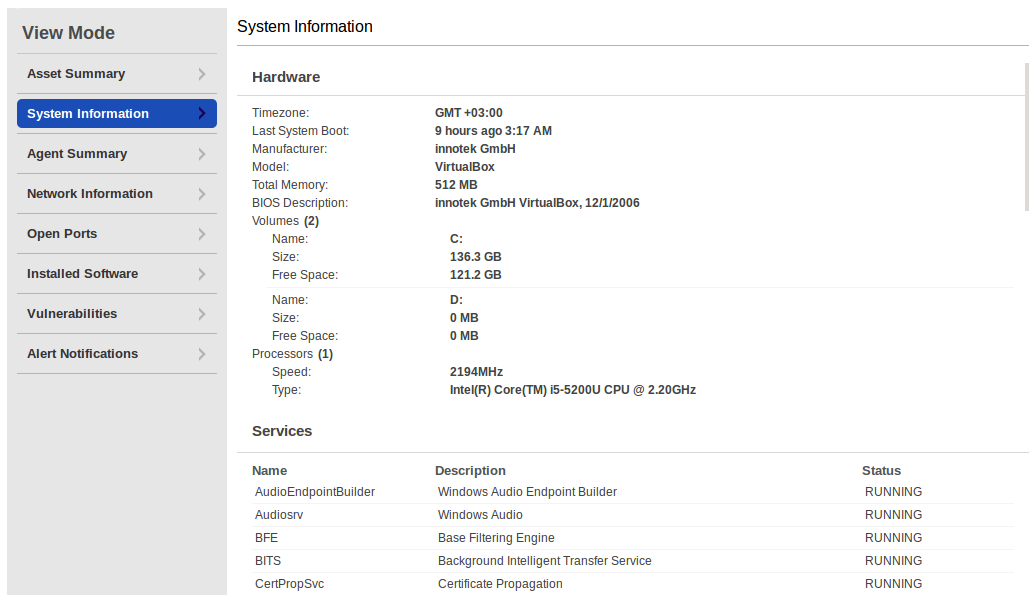
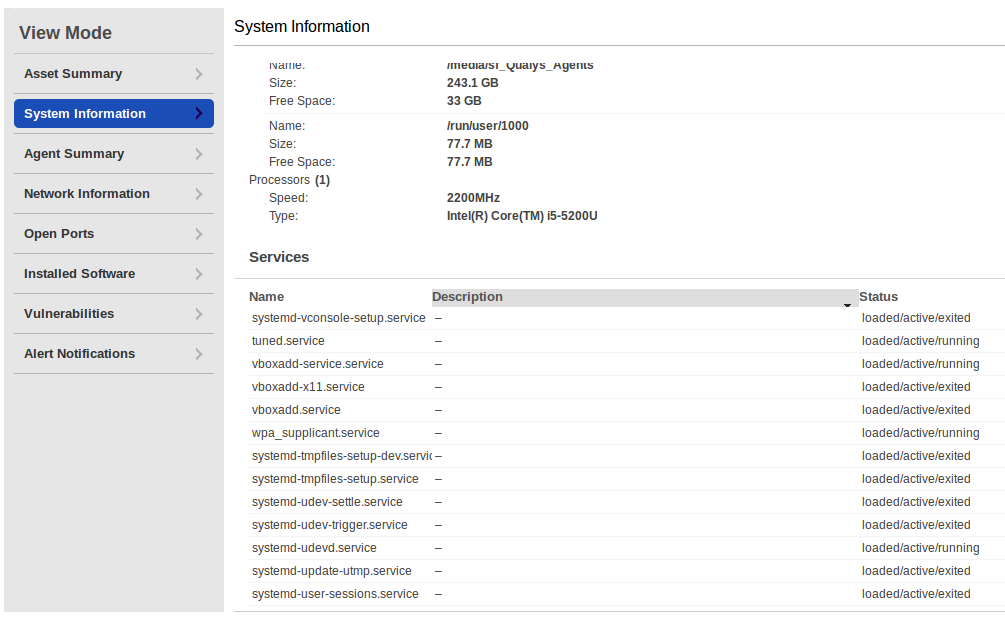
In System Information you can see information about hard drives, processor, and running services.
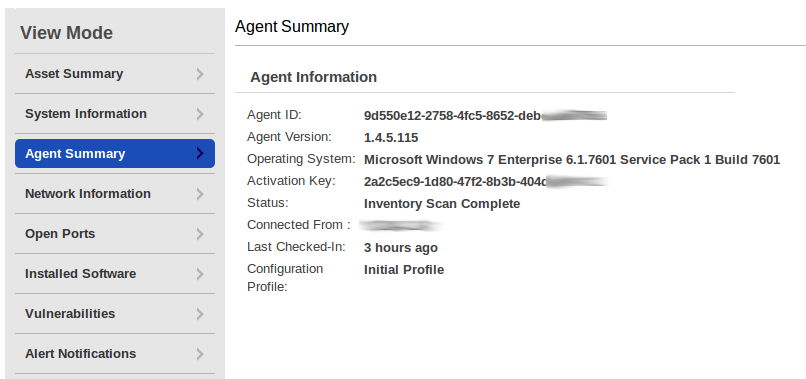
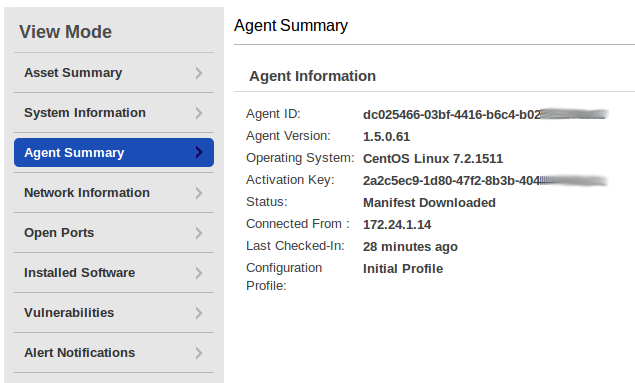
The most interesting in Agent Summary is a full version of the operating system.
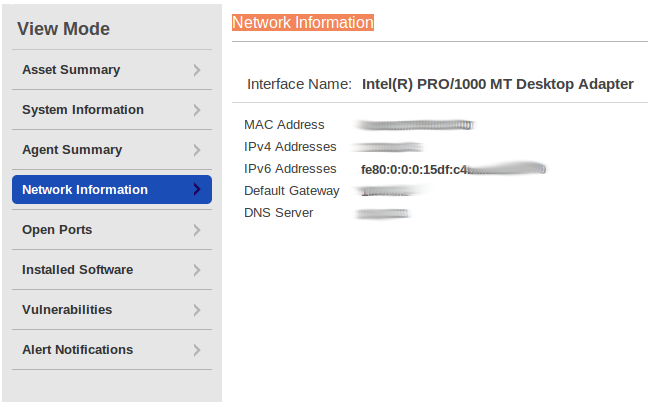
Network Information contains a MAC Address and more detailed network settings.
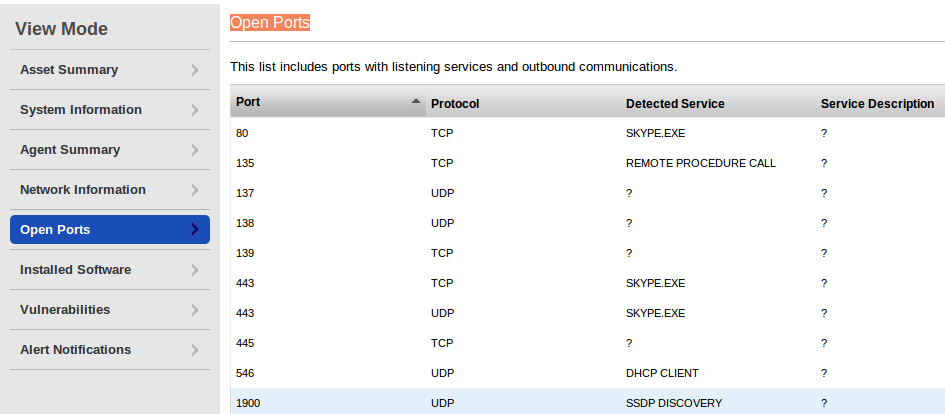
You can see by open ports that I use Skype on this virtual machine.
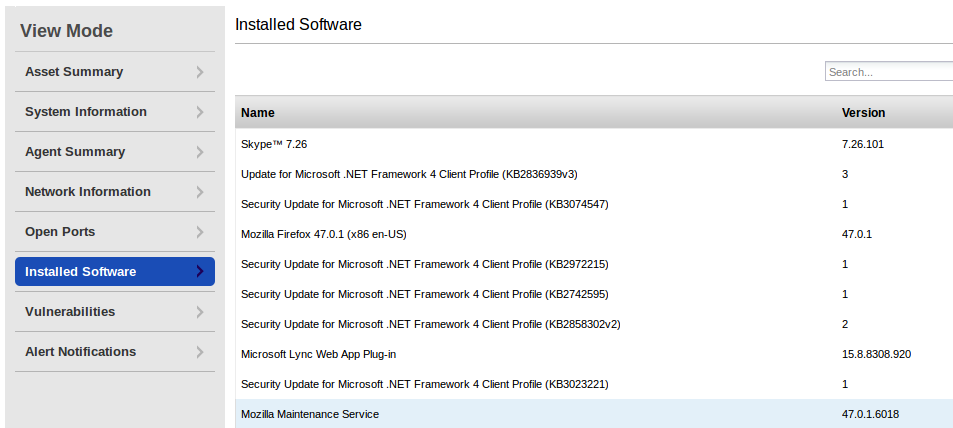
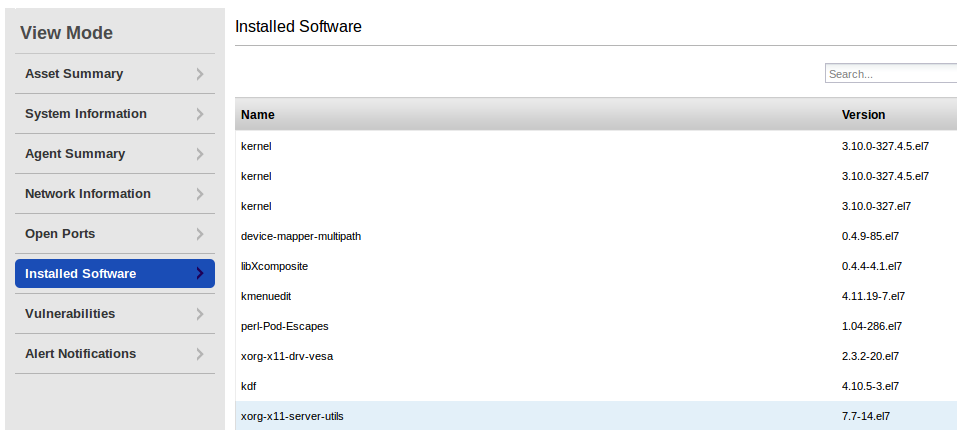
Software list. You can search in this list directly on this page.
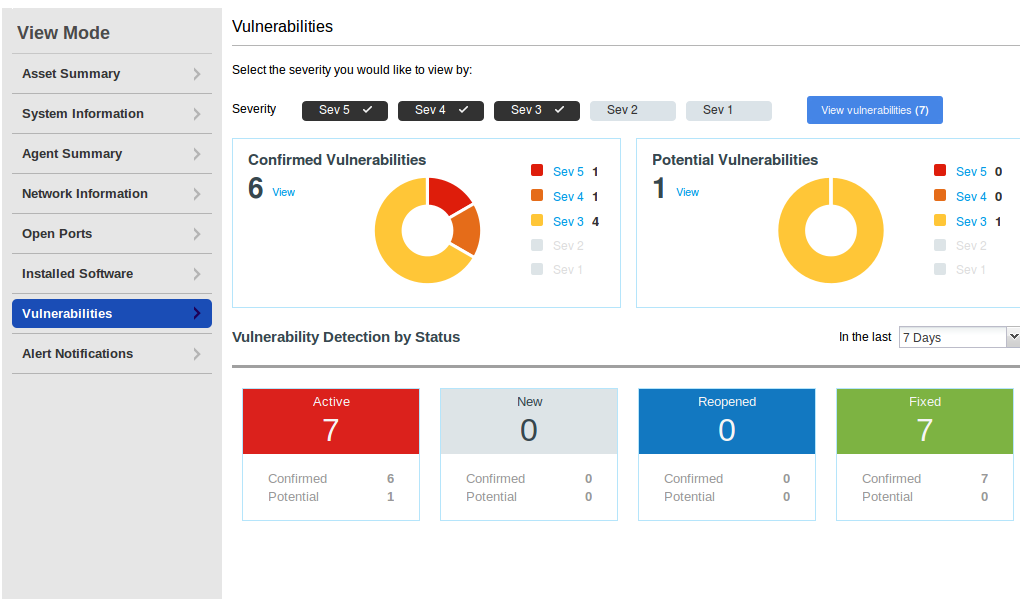
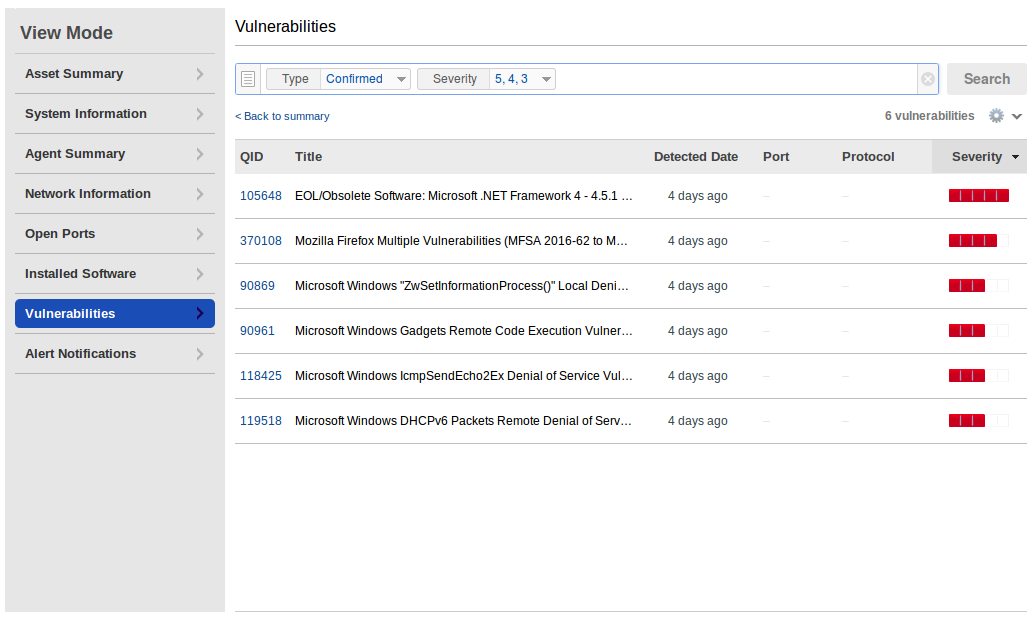
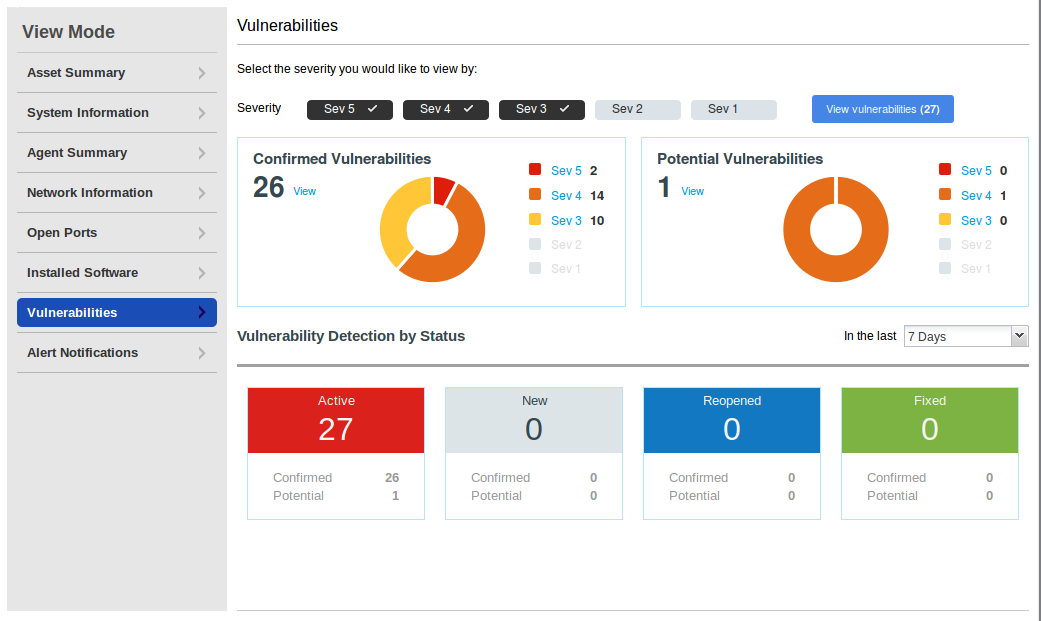
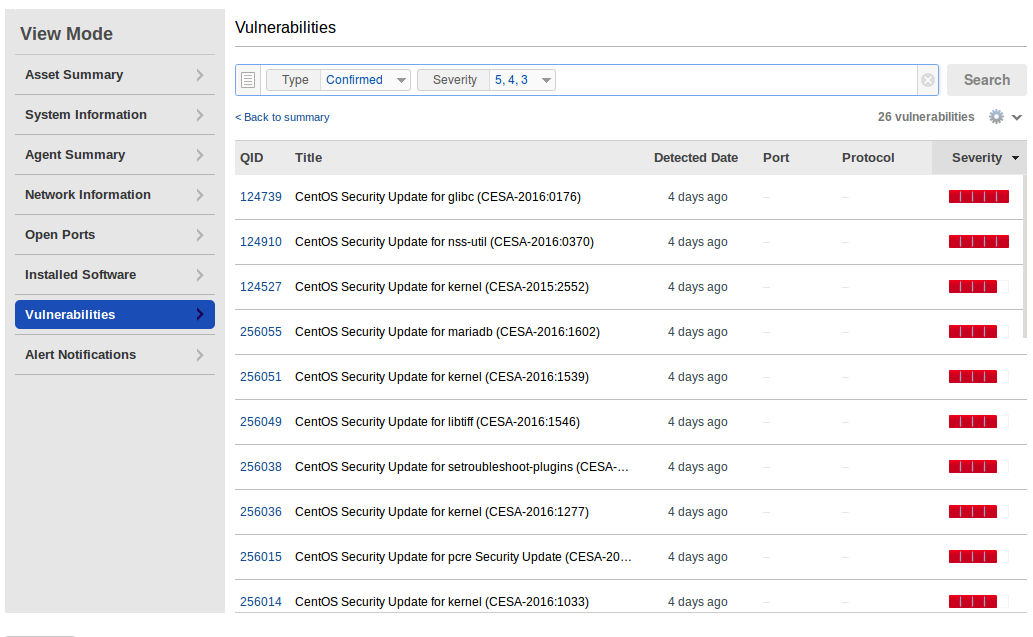
And finally vulnerabilities. As you can see, this host has not been updated for a long time. You can see the full vulnerability list by clicking on “View”.
In Continuous Monitoring module, you can configure notifications and create tickets automatically when agent detects something important on the host.
And what about Linux? Well, of course there will be a penguin picture in Asset Summary.

System Information provides statuses for services:
Full Linux distribution version in Agent Summary.
In Installed Software section you can see the list of installed rpm packages. Unfortunately, this versions does not contain details about architecture. I thought it would be nice to take the data about packages via Qualys API and make vulnerability detection independently (see: “Vulnerability Assessment without Vulnerability Scanner“), but without architectures there will be a lot of false positives.
List of vulnerabilities is displayed the same way, as for Windows:
In conclusion
Qualys Cloud Agents is a very promising technology. Installation process is very convenient and easy to automate. Agented scanning works exactly as it was presented in marketing materials. Unfortunately, Qualys collects useful information from the hosts very-very slowly. It takes hours to see vulnerabilities for the hosts. As an end user, I would like to see vulnerability data immediately after the agent has been installed. It seems that Qualys tries to optimize productivity of their cloud infrastructure this way, and it can be a changed for the better.
A nice thing is that the Qualys Asset Management module AssetView is available free of charge. It uses the same agents for collecting the data. The only difference – you won’t have vulnerability data. But it still can be pretty useful and efficient solution for managing infrastructure.
Theoretically, it is even possible to collect the list of installed programs, and try to calculate vulnerabilities using third-party tools. Unfortunately, you would need Accesses to the API to automate it, and it’s a paid service. I don’t know whether it is possible to buy API access in addition to free AssetView and what would be the final cost.
The main disadvantage of agent-based approach, in my opinion, is that the end-user can’t control agent is doing on the host. In fact, it automatically sends some encrypted data to the Qualys server, updating automatically, etc. Agent-based cloud solutions would cause less questions from cautious customers if vendors will use agents with open code and protocols for agent-server communications (read more at “Vulnerability scanners: a view from the vendor and end user side“).

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: New Vulners.com services for Linux Security Audit and Vulnerability Alerting | Alexander V. Leonov
Pingback: QSC16: from Vulnerability Management to IT Visibility | Alexander V. Leonov
Pingback: Nessus Manager and Agents | Alexander V. Leonov
Pingback: Rapid7 Nexpose in 2017 | Alexander V. Leonov
Pingback: Vulners Cloud Agents for Vulnerability Management | Alexander V. Leonov
Pingback: Carbon Blacking your sensitive data it’s what the agents normally do | Alexander V. Leonov
Pingback: Microsoft security solutions against ransomware and APT | Alexander V. Leonov
Can you tell me the way to trigger “ScanOnDemand” from a cloud agent from the endpoint server please.