Last Tuesday I was invited to Microsoft business breakfast “Effective protection against targeted and multilevel attacks”. Here I would like to share some of my thoughts on this. Need to mention that the food was delicious and the restaurant of Russian Geographical Society is a very lovely place. 😉 Thanks, Microsoft!
Microsoft as a security vendor? O RLY?
Microsoft products are not actually my topic. To tell you the truth, personally I’d better live in a world without this massive Windows hegemony in desktop operating systems. I use Linux mostly. And even when I have to work in a Windows environment, it’s much easier for me to do all the work in some Linux virtual machine.
But in the real life almost every office network is build on Microsoft solutions. And if you are doing Vulnerability Management in any organization, you should deal with them too. The good news is that many security features are available out of the box in the MS products that you have already purchased. It’s just important to know about these features and use them right.
One more thing, why it’s interesting to learn more about Microsoft information security products. Microsoft developers, obviously, have direct access to Windows source code and know better how their own OS works. Many things are much easier for them to implement than for other security vendors. So, good chances that you will see in Microsoft products some interesting features, that other vendors don’t have (yet).
Drowning in data
The event began with an opening speech by Andrey Ivanov from Microsoft Russia.

I liked his thesis that “we are drowning in security data”:
- Threat Intelligence from different sources that need to be implemented in your infrastructure and somehow validated. A good place to mention Vulners.com vulnerability feeds 😉
- Threat Detection using logs, scanners, various protection tools, etc.
- The overall number of SIEM inputs is growing faster than our resources. New IT system = new problems of SIEM configuration.
So, it would be nice if somebody, for example OS vendor, will provide all this as a service, right? 😉
Detect the undetectable
Then there was the keynote by Zbigniew Kukowski – one of the leading Microsoft information security experts.
Why is it necessary?
Here is what I would like to note from his report. First of all, great arguments why it is necessary. Ok, this is marketing. But the ability to explain (to sell) necessity of information security is important skill for any information security specialist now. It does not matter if you are working in a security vendor, integrator or customer.
Zbigniew mentioned an interesting case: some Polish company, that lost $ 4.3 million in recent the Petya attack in 4 days. The cost of Information Security measures will be much less than the potential losses of business.
Another argument – attacks are not the entertainment for some individuals any more. Now it’s a well-organized criminal business. Dozens of people are working on popular malware tools, like Petya. That’s why ransomware tools are so popular now – cyber-criminals just want to return their development costs.
Anti-ransomware features of Windows 10
At the same time, Microsoft increases the level of security in their products. Windows becomes more secure, even for average home users. For example, this security features of Windows 10 complicate the life of cyber criminals greatly:
-
- Controlled Folder Access allows the user to restrict the access to chosen folders in order to protect their contents from malicious software such as ransomware. Even if malicious software will be launched, it won’t be able to damage the most valuable information – the user’s documents.
- Windows Defender Credential Guard uses virtualization-based security to isolate secrets so that only privileged system software can access them. This can help to protect host from mimikatz and similar utilities.
- LAPS “Local Administrator Password Solution” (LAPS) provides a centralized storage of secrets/passwords in Active Directory (AD) – without additional computers. It greatly simplifies the work for system administrators (use LAPS or change passwords for all local administrators manually) and complicates the Lateral Movement stage for the attackers.
Perimeter and phishing
Microsoft is paying special attention to the post-breach solutions for instant response and mitigation. No matter how good your perimeter is, attacker can always get inside using a well-planned phishing attack. And antivirus will not help here. Attackers use virustotal-like services in deepweb to ensure that current versions of antivirus programs will not detect the malware.
Microsoft uses interesting techniques in Office 365 against phishing:
- Detonations of urls. Proxy server makes url substitution, so hackers won’t change harmless content to malicious one after all security checks will be performed.
- Detonation chamber. Suspicious attachments will be stored for analysis, but the message itself will be delivered.
This approach will be nice to see in all email web services.
What if the malware was executed on the host?
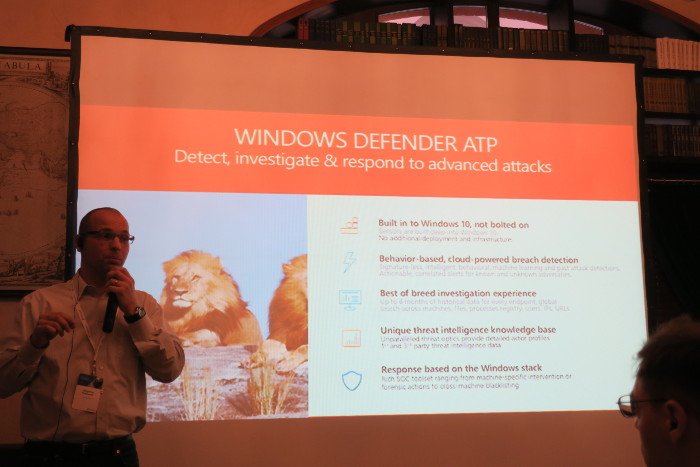
In this case SIEM-like Windows Defender ATP (Defender Advanced Threat Protection) may help. Note that it is a cloud-based solution that will not work in isolated infrastructure.
Microsoft does not like the traditional concept of SIEM. Most of the collected logs are useless. And what about the applications that do not send logs at all? Their approach is to collect useful data using “agents”. It’s somehow similar to Qualys Cloud Agents, Tenable and Rapid7 agents from the Vulnerability Management world. But in the case of Microsoft, the agents are already embedded in the Operating System. Cause they can 😉
All connected Windows hosts will be constantly sending data to the Microsoft cloud. This data will be analyzed in various ways. In case of an incident, you will be able to see the entire history of compromisation on cause effect diagrams: malicious file execution, privilege elevation, malicious processes, spreading attempts, etc.
It is possible to make a forensic investigation and detect where compromised credentials were used. Then you can take action: to isolate or semi-isolate the host. Data is stored for 6 months to detect even a very smart and secretive attacks.
Since this is a cloud, Microsoft can identify similar patterns of attacks on different customers and block malware quickly and efficiently. For example, BadRabbit was stopped in 14 minutes.
Live demonstration was quite interesting. IMHO, it’s a very good example of agent-based anti-APT solution with email service integration. You can see some screenshots of GUI here.
Microsoft ATP can work with:
- Windows 10
- Windows servers 2016 and 2012 – there are agents for them.
- Office 365
- Microsoft ATA (on premises solution for traffic analysis, you can control hosts with other versions of Windows).
- Agents for third party OS: Linux, macOS, etc. You should purchase them at Microsoft partners.
More products – more optics. There are integration with popular SIEMs, “to configure email-alerts”. 😉
In conclusion
I liked Microsoft ATP functionality. But there are significant limitations:
- It’s quite a hard task to update all Windows hosts to Windows 10 and the latest version of Windows Server.
- It will be a difficult decision to store this critical data in Microsoft cloud. Even with Microsoft’s guarantees that all the data is stored securely and they touch it with AI only.
The event was held in a pleasant atmosphere. The Q&A section was very informative. There was even a question about last week RCE in Malware Protection Engine. The reaction was predictable: “it’s happens. We have a kb” 🙂 Thanks, Microsoft Russia, for the invitation! It was a great event!

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Vulnerability Management news and publications #2 | Alexander V. Leonov
Pingback: И тут было бы справедливо спросить: "А не ты ли, Александр, совсем недавно топил за эти самые облачные ИБ сервисы Microsoft, а теперь получаетс