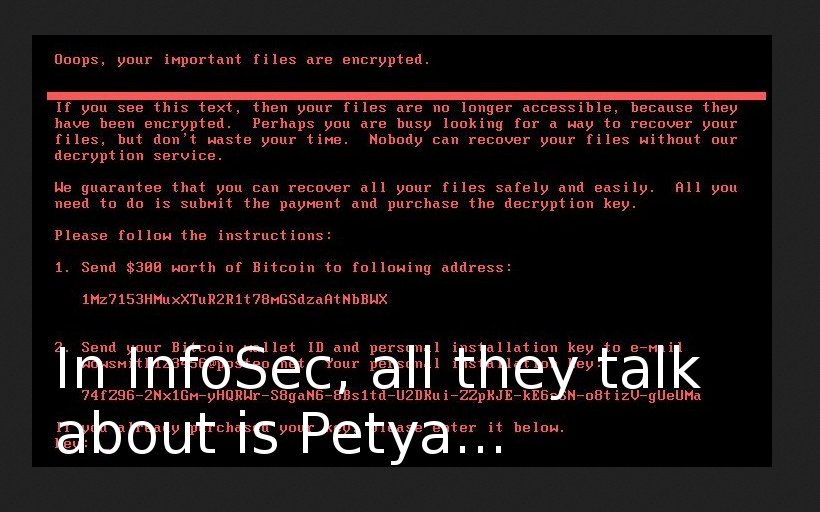
This post I will publish in the API section of my blog. However, it is about the situation when there application has no API. Let’s suppose that we have to use in our work some graphical application or web-service. And unfortunately we need constantly repeat some very routine and annoying operations in it. This often happens if the application developers have not thought enough about the real-life cases their end-users will deal with. What can we do in such scenario?
- First of all, look maybe there is an open and documented API
- If there is no API, and it is an installed application, maybe you can use it in a console mode
- If it is a web-service, maybe you can figure out how it works and how to automate it using tools like Firebug
But sometimes it is impossible to do anything at all. And it is even more sad, if this routine task is really elementary and you can easily explain the logic: what menu to choose, what button to push, where you should enter text and so on.
At this point, you just spit on all and use your last resort – SikuliX.
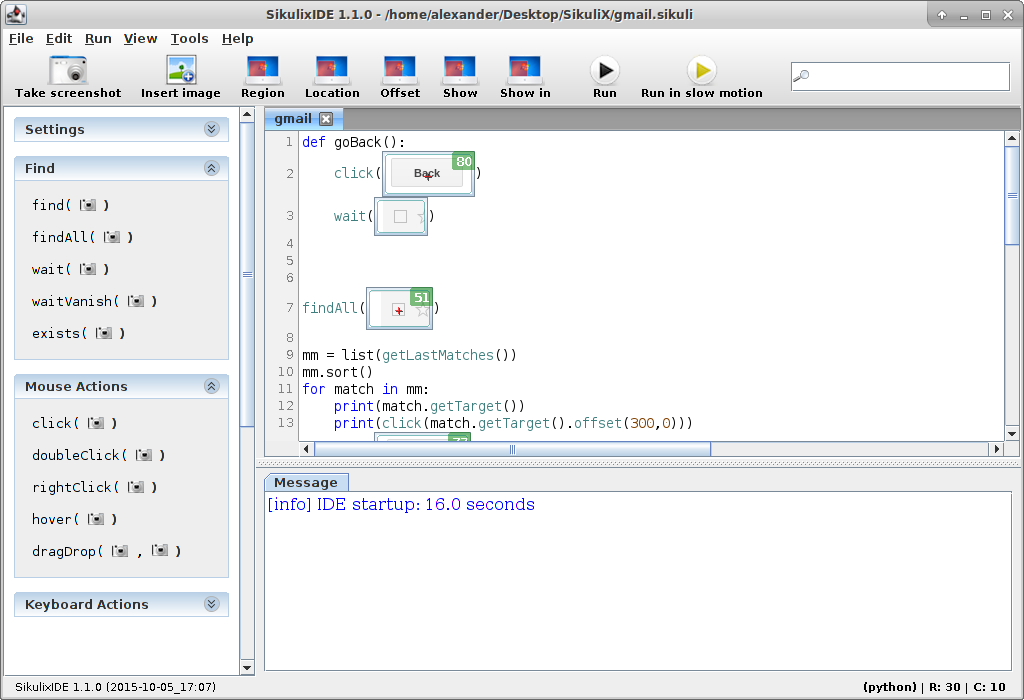
With this tool, you can automate everything. It doesn’t matter if it is a web-service or a GUI application, what operating system it uses and so on. That’s all because SikuliX is working at the highest level. In fact, it just makes screenshots, analyses them as images, trying to find graphical elements that it should somehow use.
Continue reading →