The question is: do we really need an employee in organization that deals with vulnerabilities in infrastructure on a full-time basis? Since this is similar to what I do for living, I would naturally say that yes, it is necessary. But as person, who makes security automation, I can say that there are some options. ?
What can and can’t Vulnerability Assessment (VA) specialist do?
VA specialist makes recommendations to remove vulnerabilities from your infrastructure using some tools: vulnerability scanners, vulnerability feeds, different news sources. In case of network vulnerabilities, he will most often tell your IT administrators: “Do we use A software with version BBB? As I see some security bulletin says that there is a critical vulnerability in it”. That’s it.
VA specialist by himself usually don’t patch the hosts. Moreover, sometimes he can’t detect the vulnerability, even he has an expansive vulnerability scanner, because some vulnerabilities can only be detected locally during authenticated scanning, and this IS specialist may not have permissions to do it.
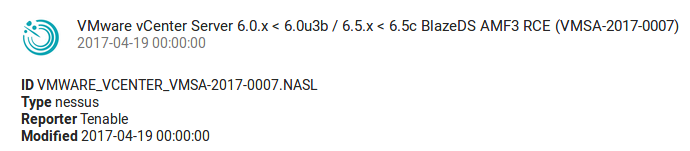
Let’s look at VMware vCenter Server vulnerability CVE-2017-5641 (published 2017-04-13):
VMware vCenter Server contains a remote code execution vulnerability due to the use of BlazeDS to process AMF3 messages. This issue may be exploited to execute arbitrary code when deserializing an untrusted Java object.
How does it look from the VA side?
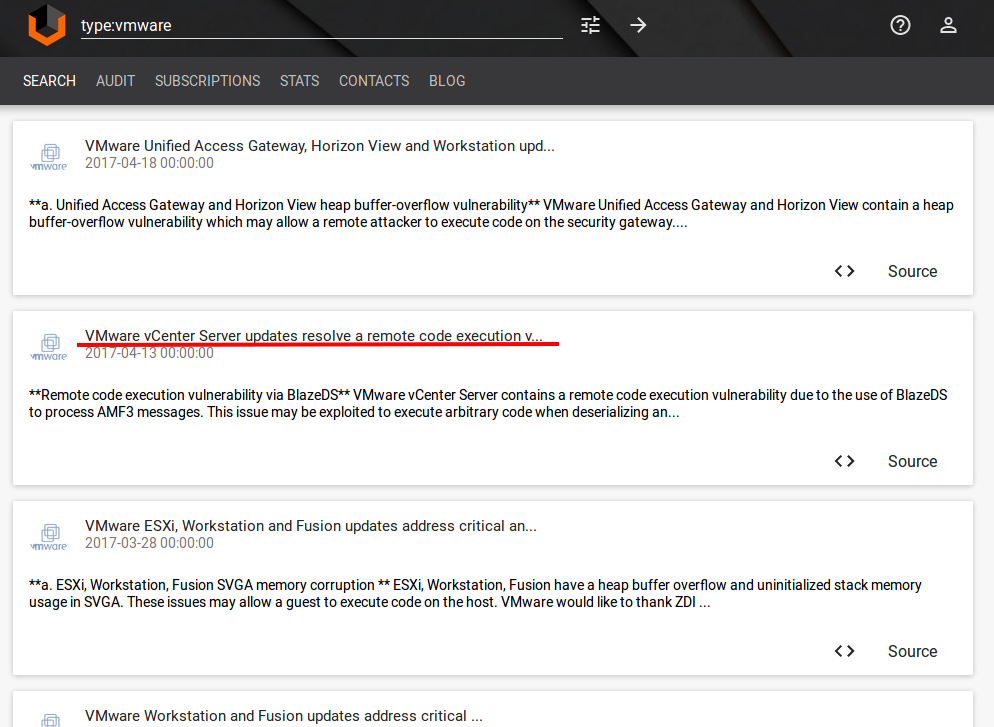
- The scanner vendor creates a vulnerability detection plugin (6 days later).
- VA specialist during regular scanning process (once a week? once a month?) finds out – wherever we have vulnerable VMware vCenter Server and creates a ticket for IT department.
With the same success IT administrator can simply subscribe to VMware vulnerabilities by himself and get information that it’s time to patch it before the VM vendor will even create a detection plugin. Much faster and more reliable!
If there is no difference, why pay more?
In my opinion, for an SMB organization that don’t have an information security role, or have only one IT security specialist who in charge of everything, highly customizable vulnerability feed may give your IT guys necessary information what we need to patch. And is much more cost effective solution than a full-time Vulnerability Assessment specialist.
OK. Vulnerability feed will not tell us if we have vulnerable software installed in our environment. But VA specialist with expensive Vulnerability Scanner in many cases won’t be able to tell you about it either without help of IT. Why pay more?
So, how we can live without VA specialist and traditional vulnerability scanners, but with vulnerability databases and subscriptions. I see this stages of process improvement:
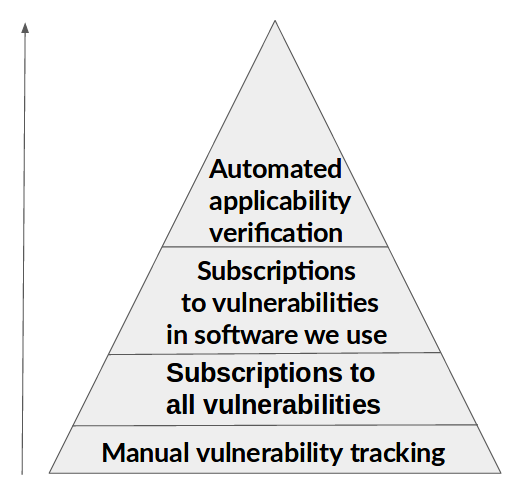
- Manual vulnerability tracking. On the first stage We search for information and patch, only when all IS sites start to write about the vulnerability.
- Subscriptions to all vulnerabilities. On this stage we start to monitoring the common vulnerability flow by subscribing to Valners feed or other service. We start to understand that there are a lot of vulnerabilities and it’s not entirely clear what we should monitor.
- Subscriptions to vulnerabilities of the software we use. We start to make queries for the software we use. We understand that it is difficult to maintain this list of software up-to-date and we come to necessity to collect it automatically, for example, using agents or integrating with IT monitoring tools.
- Automated applicability verification. Knowing the names and versions of software we use, we can validate the vulnerability and greatly minimize the list of what we actually need to patch.
Basically, you can stay for a long on any stage. But going to the next stage increases the efficiency of the process. False-positives are also not so scary. It is better to upgrade without a particular reason than to miss critical and exploitable vulnerability.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: PHDays VII: To Vulnerability Database and beyond | Alexander V. Leonov