Hello everyone! In this episode I want to highlight the latest changes in my Vulristics project. For those who don’t know, this is a utility for prioritizing CVE vulnerabilities based on data from various sources.. Currently Microsoft, NVD, Vulners, AttackerKB.
Command Line Interface
I started working on the CLI for Vulristics. Of course, it is not normal to edit scripts every time to release a report.
CVE lists
If you have a list of CVEs that you want to analyze, you can run Vulristics this way
python3.8 vulristics.py --report-type "cve_list" --cve-project-name "New Project" --cve-list-path "analyze_cve_list.txt" --cve-data-sources "ms,nvd,vulners,attackerkb" --rewrite-flag "True"In analyze_cve_list.txt I have one CVE
CVE-2021-42284
The output:
Reading existing Patch Tuesday profile...
Exclude CVEs: 0
No specified products to analyze set in profile, reporting everything
All CVEs: 1
Counting CVE scores...
Collecting MS CVE data...
Collecting NVD CVE data...
Collecting AttackerKB CVE data...
Collecting Vulners CVE data...
Counting CVE scores...
Making vulnerability reports for each reports config...
Report config: with_comments_ext_img
Report generated: reports/new_project_report_with_comments_ext_img.htmlAnd in the reports/new_project_report_with_comments_ext_img.html file we can see a block for this CVE
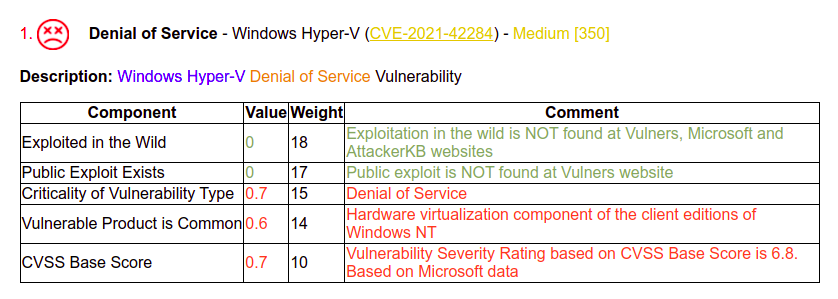
I can add a file with comments as well. This can be useful if you are analyzing scan results for multiple hosts and you have such data:
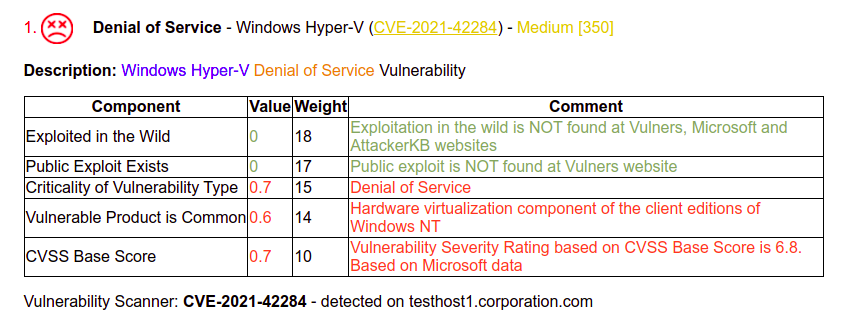
Vulnerability Scanner|CVE-2021-42284 - detected on testhost1.corporation.comYou add a key --cve-comments-path "analyze_cve_comments.txt"
python3.8 vulristics.py --report-type "cve_list" --cve-project-name "New Project" --cve-list-path "analyze_cve_list.txt" --cve-comments-path "analyze_cve_comments.txt" --cve-data-sources "ms,nvd,vulners,attackerkb" --rewrite-flag "True"And you see this comment under the vulnerability block. Quite convenient.
Microsoft Patch Truesdays
You can also make a Microsoft Patch Tuesday report simply by
python3.8 vulristics.py --report-type "ms_patch_tuesday" --mspt-year 2021 --mspt-month "November" --rewrite-flag "True"And get a reports/ms_patch_tuesday_november2021_report_with_comments_ext_img.html
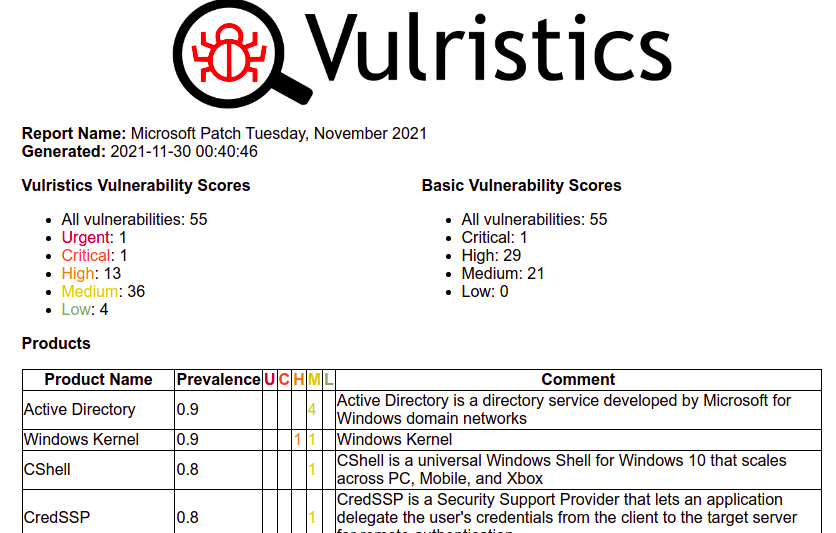
But before discussing the November Patch Tuesday report, of course if someone is still interested in it in the last day of November, I want to talk about the product and vulnerability type detections.
Improved Product & Vuln. Type Detection
I heavily reworked the part about product and vulnerability type detection. I have simplified and unified the connectors for the sources. Sources now provide text strings for detection. Detection occurs at the time of generation of the report, through the analysis of all available descriptions of vulnerabilities.
All product detection rules are in data/classification/products.json
You can also manage the priority of software detection. In simple terms, the word “Windows” can indicate that the vulnerability is in the Windows kernel. But only if nothing more specific and rare was detected. For example “Skype for Windows”. We can achieve this by setting detection_priority = -1 for Windows kernel.

The strings for Vulnerability Type and Product are now highlighted in the vulnerability description with blue and orange.
Microsoft Patch Tuesday November 2021
Just a few words. It was a calm Patch Tuesday. There are 55 vulnerabilities in total. One Urgent level and one Critical level.
Security Feature Bypass – Microsoft Excel (CVE-2021-42292)
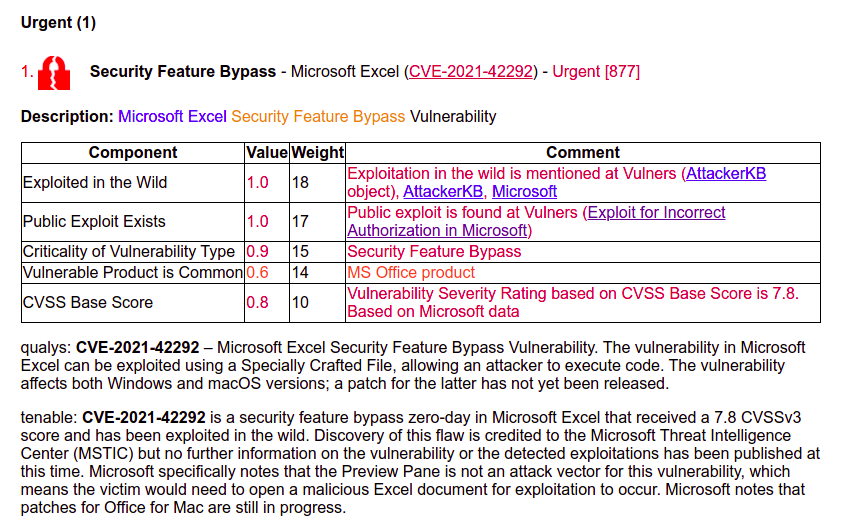
it was featured as an Urgent because of exploitation in the wild. And besides, because of a Github exloit on Vulners. However, this is false positive. This is not an exploit, but a detection rule. This happens.
Remote Code Execution – Microsoft Exchange (CVE-2021-42321) – Critical [718]
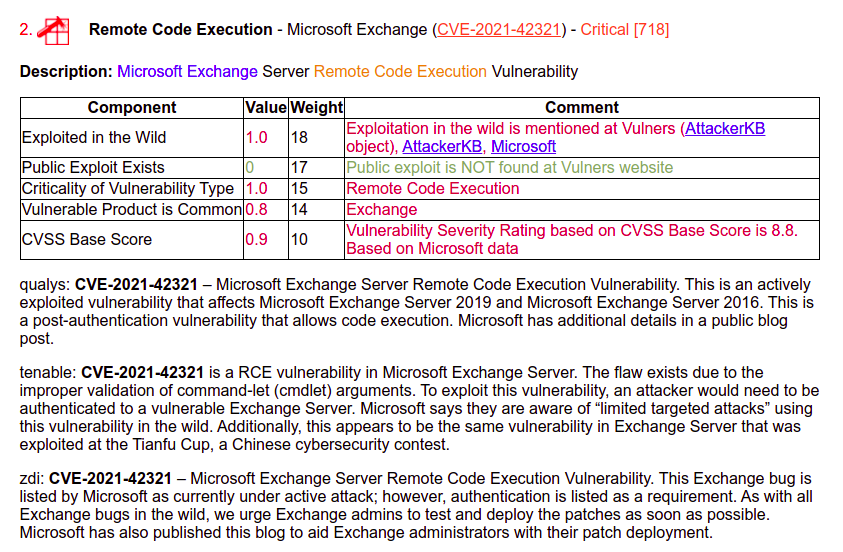
“This is an actively exploited vulnerability that affects Microsoft Exchange Server 2019 and Microsoft Exchange Server 2016. This is a post-authentication vulnerability that allows code execution.”
For those interested, there is a link to the entire report.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
