Vulristics May 2022 Update: CVSS redefinitions and bulk adding Microsoft products from MS CVE data. Hello everyone! In this episode, I want to talk about the latest updates to my open source vulnerability prioritization project Vulristics.
Alternative video link (for Russia): https://vk.com/video-149273431_456239088
CVSS redefinitions
A fairly common problem: we have a CVE without an available CVSS vector and score. For example, this was the case with CVE-2022-1364 Type Confusion in V8 (Chromium). This vulnerability does not exist in NVD.
The CVSS for this vulnerability is not available on the Microsoft website. Although this vulnerability itself exists for the Edge browser.
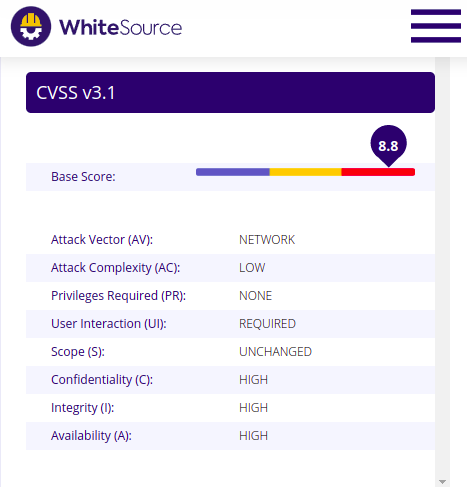
But on the other hand, CVSS can be found on other sites, such as White Source.
Therefore, I decided to add the ability to manually set the CVSS value for some vulnerabilities in data_redefinitions.py. And this value will be used in the report.
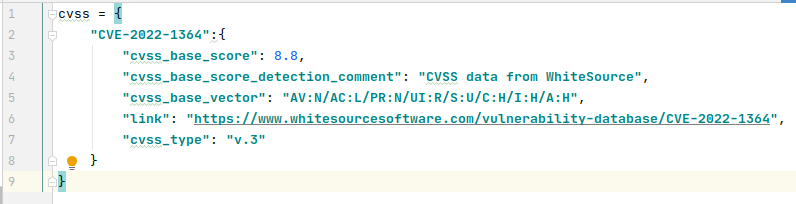
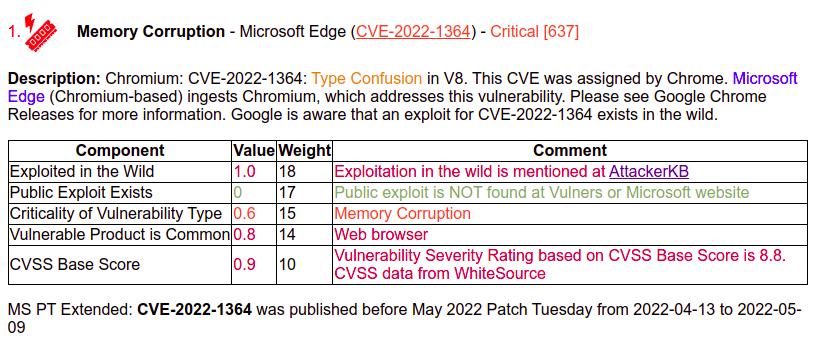
This allows you to correctly assess vulnerabilities even if there are some problems in the main data sources.
Bulk adding Microsoft products from MS CVE data
The second problem is that I still edit the product description file data/classification/products.json manually. This file is used to detect the names of vulnerable products based on the description of the vulnerabilities.
When I do the Microsoft Patch Tuesday reports every month, there are new products that are not covered in the file. They appear in the report as Unknown Products. I have to manually add them to the file.
It’s annoying. In addition, there may be products containing the word “Windows” in their name. If there is no separate detection for them, they will be detected as Windows Kernel. And this is not right.
Therefore, I added functions to automatically edit products.json. I download all Microsoft CVEs from Vulners.com, extract software names from titles, and add new softwares to products.json.
Those products that have the word Windows in their name are added with the comment “Windows component” and a criticality of 0.8. The remaining products are added with an average criticality of 0.5 and without comment.
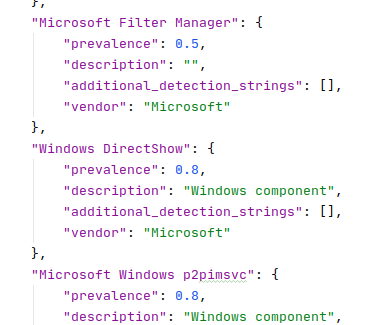
It is expected that they will be edited manually if necessary. For all products, the vendor “Microsoft” is set.
I had 358 manually added products, I received 821 candidates for addition. As a result, I got 861 products in the products.json file. Big progress without much effort. Now it will be enough to run update_products_file_from_vulners_ms_cves() function periodically and this will eliminate problems with manually adding products for MS Patch Tuesday.
In case of duplication, simply add an additional name to additional_detection_strings. Also, of course, you can freely change the prevalence and detection_priority and they will not be overwritten.
New improvements can be evaluated in the next episode about Microsoft Patch Tuesday.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Microsoft Patch Tuesday May 2022: Edge RCE, PetitPotam LSA Spoofing, bad patches | Alexander V. Leonov