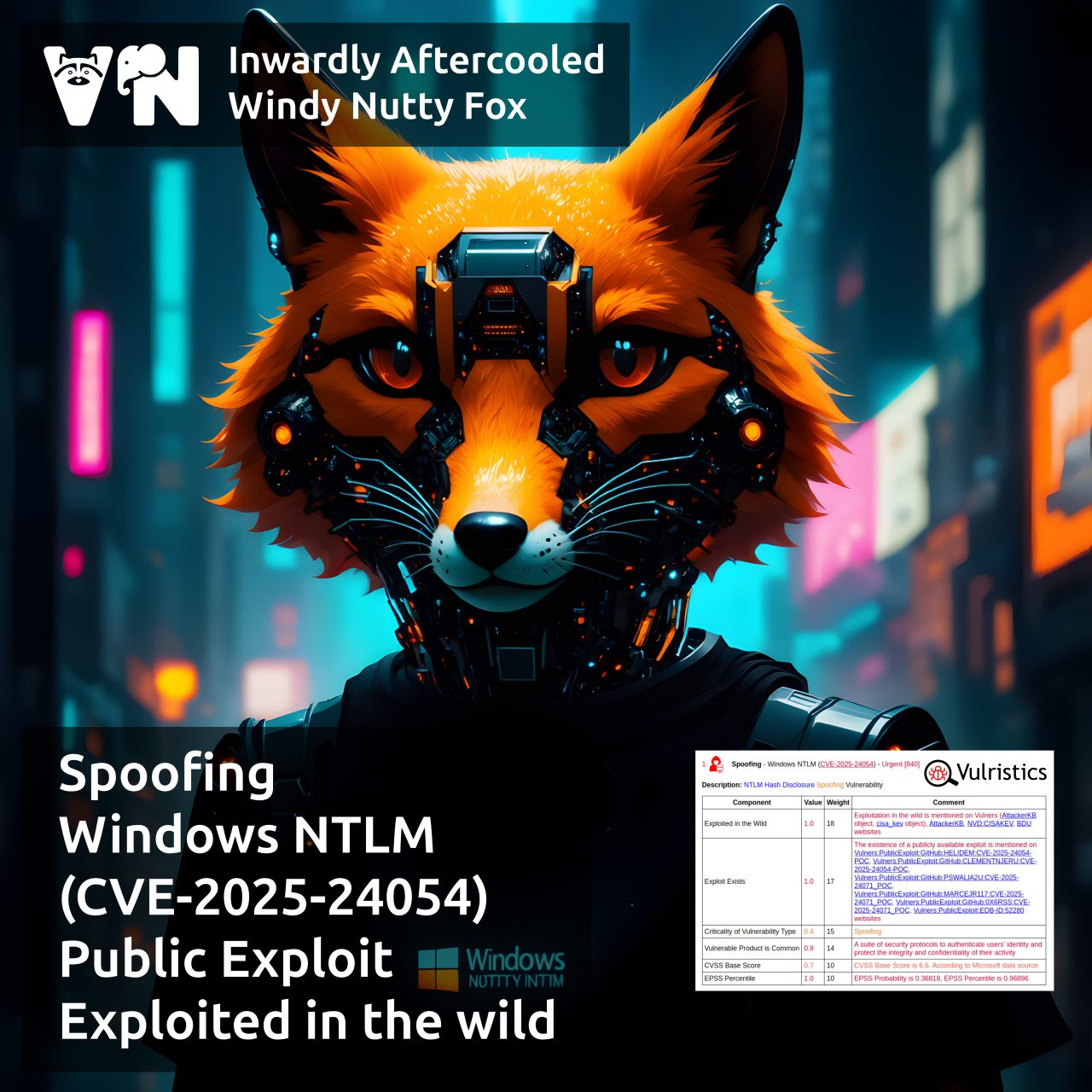
About Spoofing – Windows NTLM (CVE-2025-24054) vulnerability. It was patched in the March Microsoft Patch Tuesday. VM vendors didn’t mention this vulnerability in their reviews; it was only known to be exploited via user interaction with a malicious file.
A month later, on April 16, Check Point published a blog post with technical details, revealing that the vulnerability is exploited using specially crafted files…
✋ Wait a minute — there was a trending vulnerability in March MSPT: CVE-2025-24071, related to the same files. 🤔 Turns out, it’s THE SAME vulnerability. 🤪 Check Point reports: “Microsoft had initially assigned the vulnerability the CVE identifier CVE-2025-24071, but it has since been updated to CVE-2025-24054“. What a mess. 🤷♂️ Technical details in the previous post.
👾 Since March 19, Check Point has tracked about 11 campaigns exploiting this vulnerability to collect NTLMv2-SSP hashes.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: May “In the Trend of VM” (#15): vulnerabilities in Microsoft Windows and the Erlang/OTP framework | Alexander V. Leonov