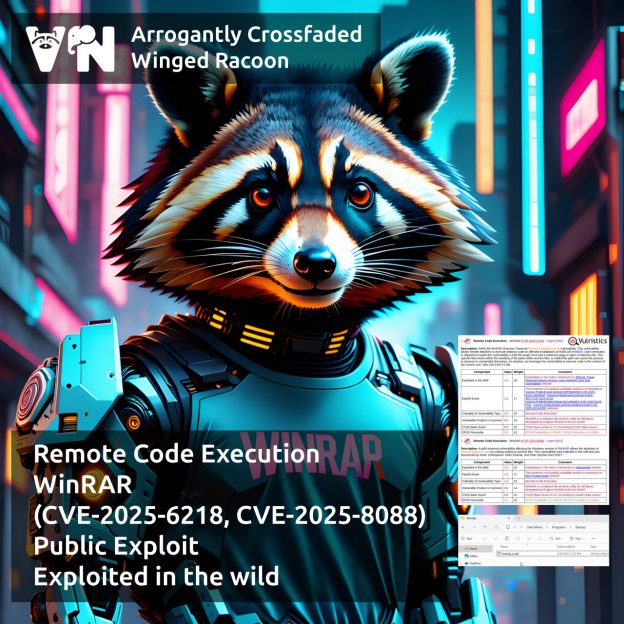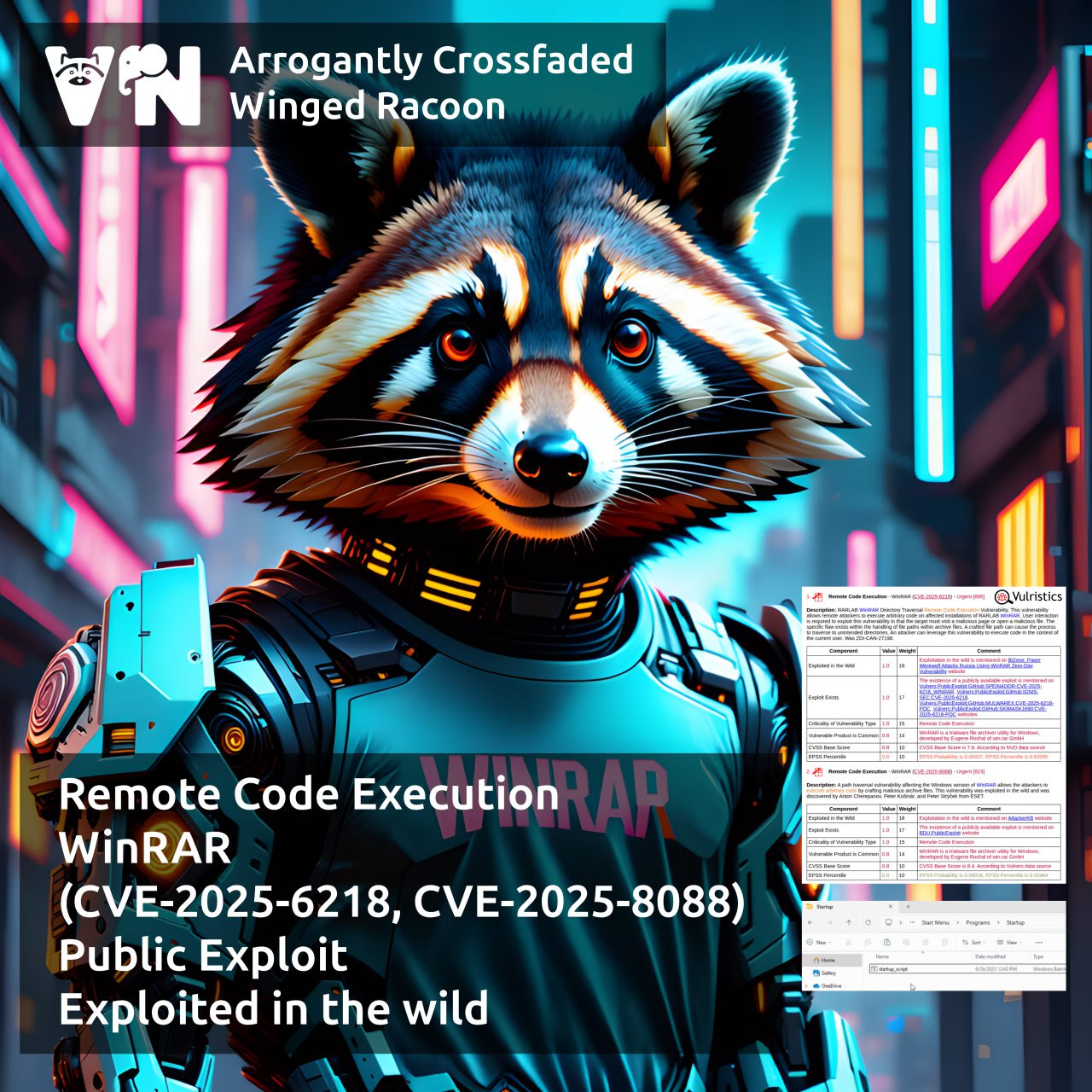
About Remote Code Execution – WinRAR (CVE-2025-6218, CVE-2025-8088) vulnerabilities. A crafted file path inside an archive may cause the extraction process to move into unintended directories (including the Startup directories 😈), which can result in archive extraction leading to the execution of malicious code in the context of the current user.
🩹 Vulnerability CVE-2025-6218 was reported to the vendor on June 5. It was fixed on June 25 in version 7.12. A month later, on July 30, version 7.13 was released, which addressed CVE-2025-8088 with the same description.
🛠 A public exploit for CVE-2025-6218 has been available on GitHub since June 27.
👾 On August 8, BiZone reported phishing attacks against Russian organizations exploiting CVE-2025-6218 and CVE-2025-8088 since early July, linked to the group Paper Werewolf (GOFFEE). ESET also observed attacks exploiting these vulnerabilities to deploy RomCom backdoors.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.