Vulners has added information on exploits. But wasn’t that already available before? After all, Vulristics takes most of its exploit-related data from Vulners! 🤔
That’s true. ✅ But previously an exploit in Vulners was always a Vulners object from a specific collection. For example, an exploit page from ExploitDB. The centralized, collection-based approach works great for sources like vulnerability databases, security bulletins, and exploit packs.
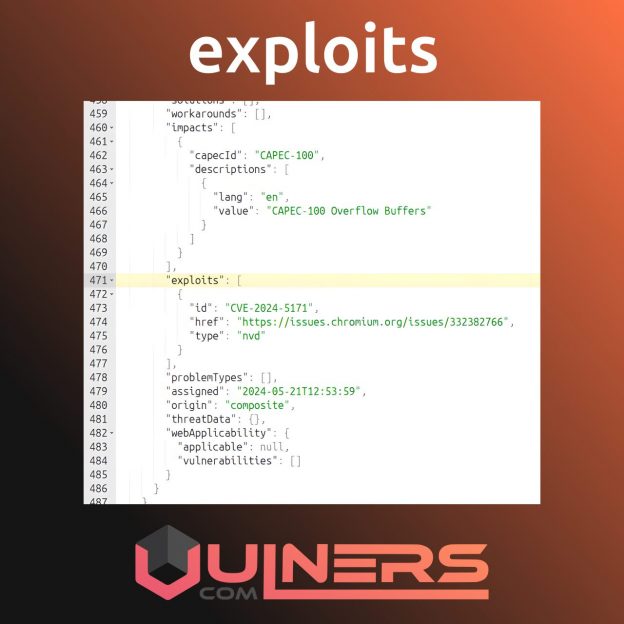
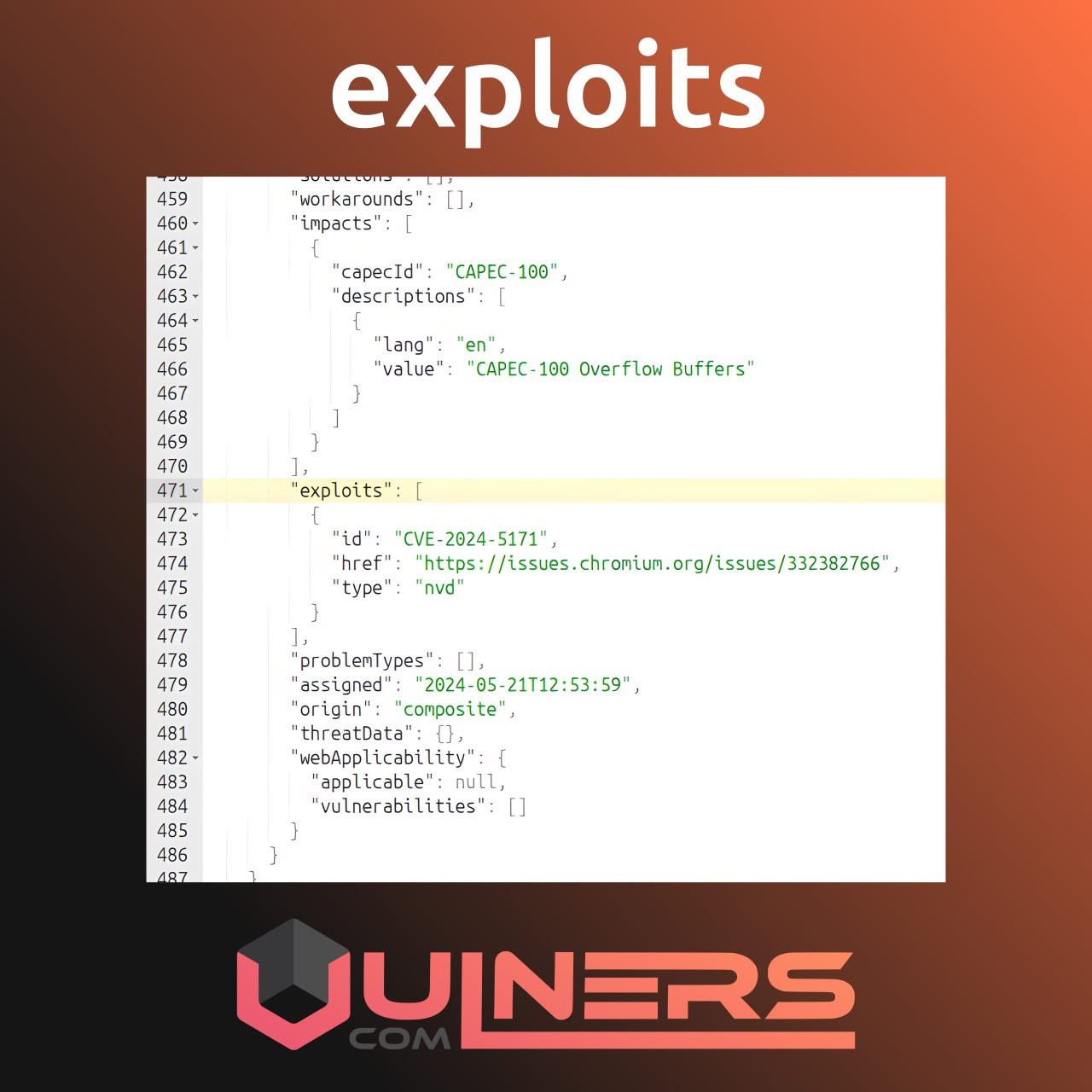
However, quite often an exploit PoC is found in random places – for example, in a researcher’s blog post or on a vendor’s page. For such cases, Vulners now also stores exploits as sets of links in the vulnerability metadata. 🔗🧩 These links are collected from various sources, including NVD, GitHub, and Gitee.
The number of sources will expand, exploit information in Vulners will become more complete, and tools like Vulristics will be able to prioritize vulnerabilities even better based on that. 🧰📈

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.