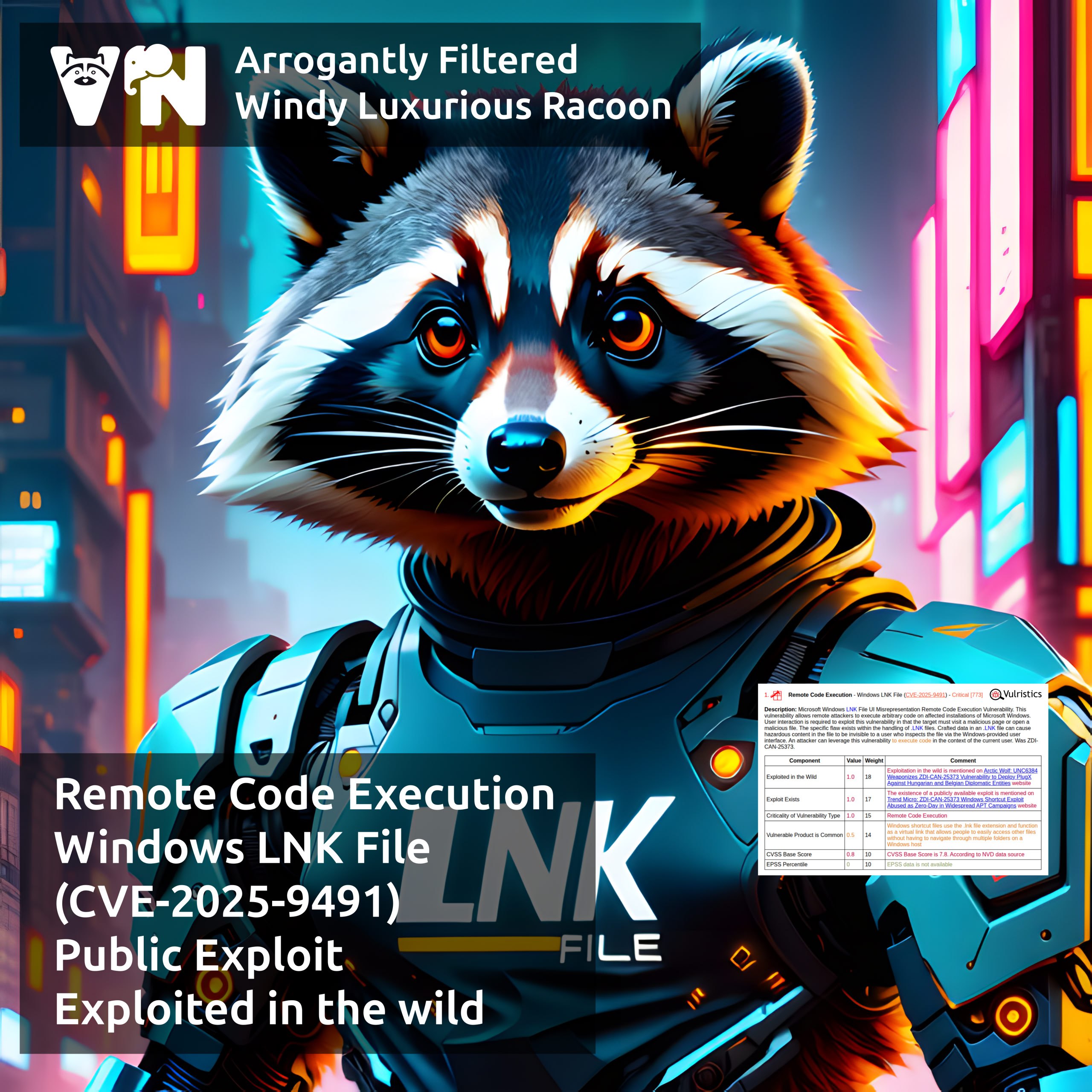
About Remote Code Execution – Windows LNK File (CVE-2025-9491) vulnerability. A vulnerability in the Microsoft Windows shortcut (.LNK) handling mechanism allows malicious command-line arguments to be hidden in the Target field using whitespace characters, making them invisible to standard tools. Opening such an LNK file may lead to arbitrary code execution.
🔻 Peter Girnus, an expert at Trend Micro, notified Microsoft about the vulnerability on September 20, 2024, but they decided not to fix it. 🤷♂️ On August 26, 2025, this 0-day vulnerability (ZDI-CAN-25373) was assigned the identifier CVE-2025-9491.
👾 On March 18, 2025, Trend Micro reported that this vulnerability was exploited in APT attacks, and on October 30, Arctic Wolf Labs confirmed it was used to deploy PlugX malware against Hungarian and Belgian diplomatic missions.
🛠 The method for modifying .LNK files is described in the Trend Micro report.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.