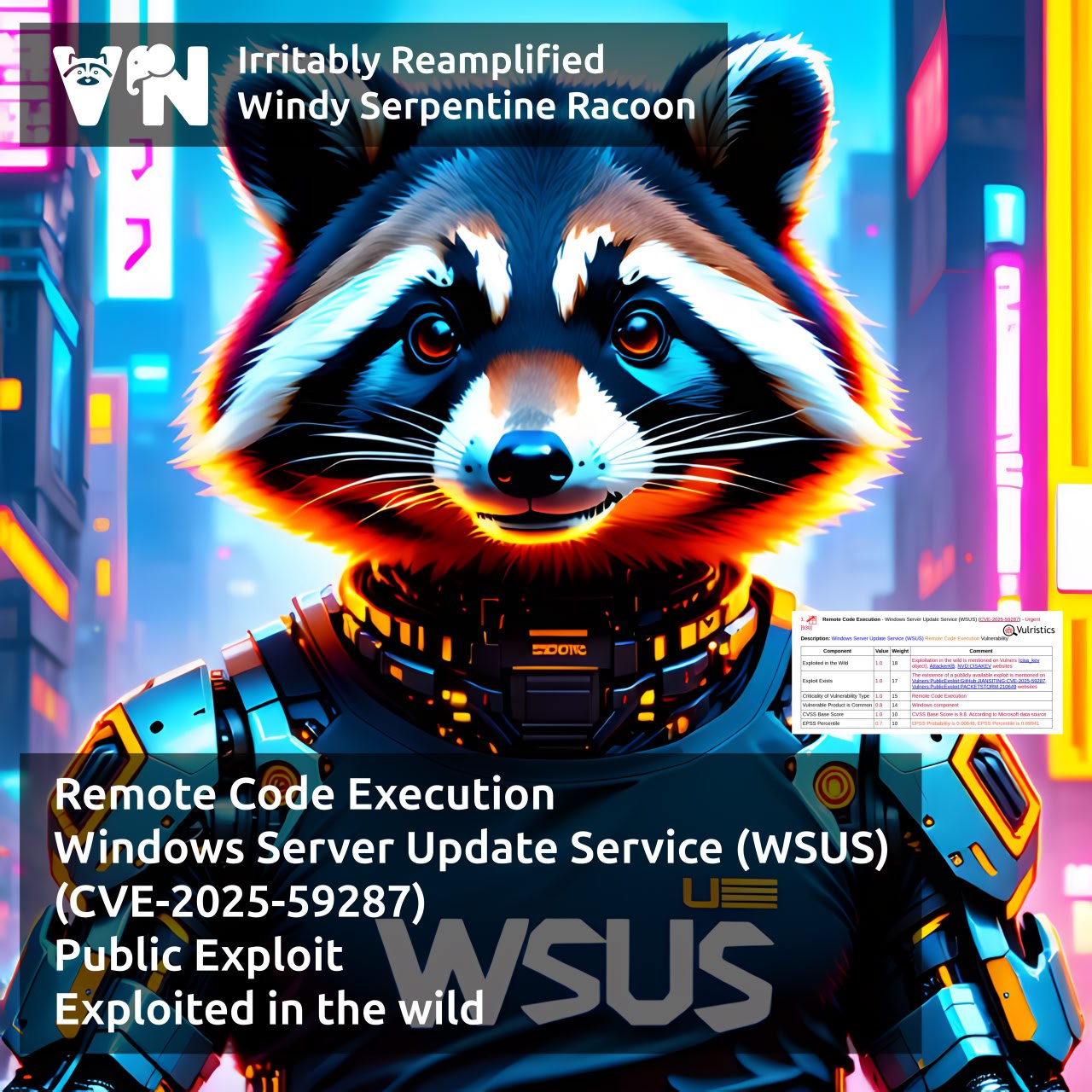
About Remote Code Execution – Windows Server Update Services (WSUS) (CVE-2025-59287) vulnerability. WSUS is a legacy Windows Server component that allows IT administrators to manage the download and installation of Microsoft product updates on computers within a local network. Vulnerability summary: An unauthenticated remote attacker can execute code with SYSTEM privileges on a Windows server with the WSUS Server Role enabled (it is disabled by default) by sending specially crafted POST requests. This is possible due to a flaw in deserializing untrusted data.
⚙️ Initial patches were released on October 14 as part of Microsoft’s October Patch Tuesday.
🛠 A public exploit has been available on GitHub since October 18.
⚙️ On October 24, Microsoft released additional patches to fully address the vulnerability (server reboot is required).
👾 On October 24, the vulnerability was added to the CISA KEV, and there are reports of observed exploitation attempts.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.