
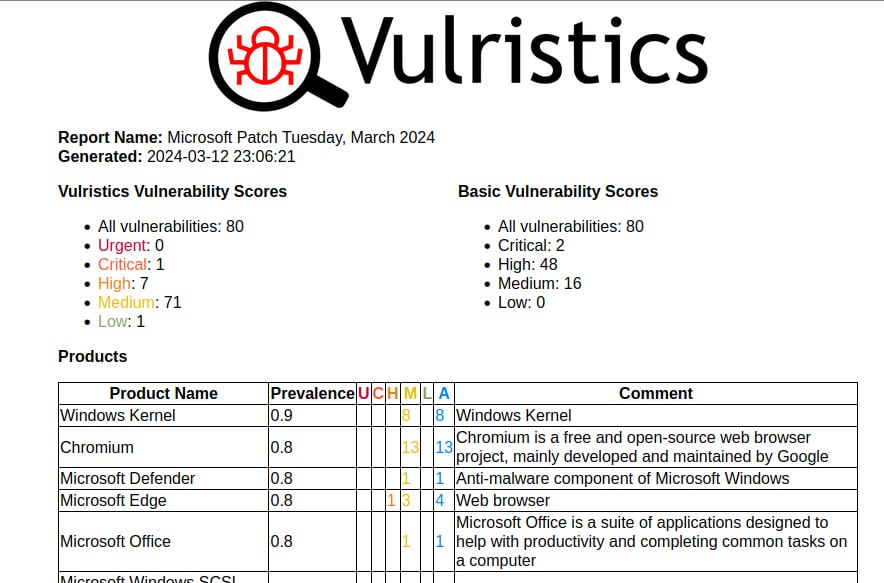
First impressions of the March Microsoft Patch Tuesday. So far I have not seen anything overtly critical. There are 80 vulnerabilities in total, including 20 added between the February and March MSPT.
With PoC there is only one:
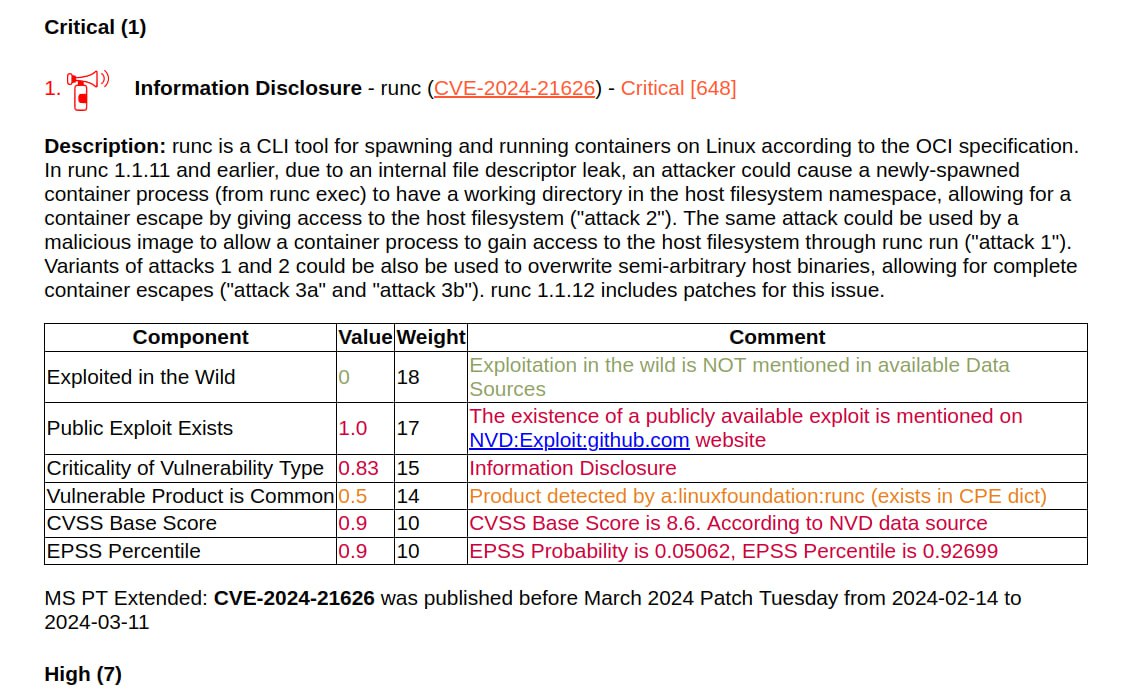
🔻 Information Disclosure – runc (CVE-2024-21626). It allows an attacker to escape from the container. What does Microsoft have to do with it? The vulnerability has been fixed in Azure Kubernetes Service and CBL-Mariner (Microsoft’s internal Linux distribution).
For the rest, there are no signs of active exploitation or the existence of a PoC yet.
We can pay attention to the following:
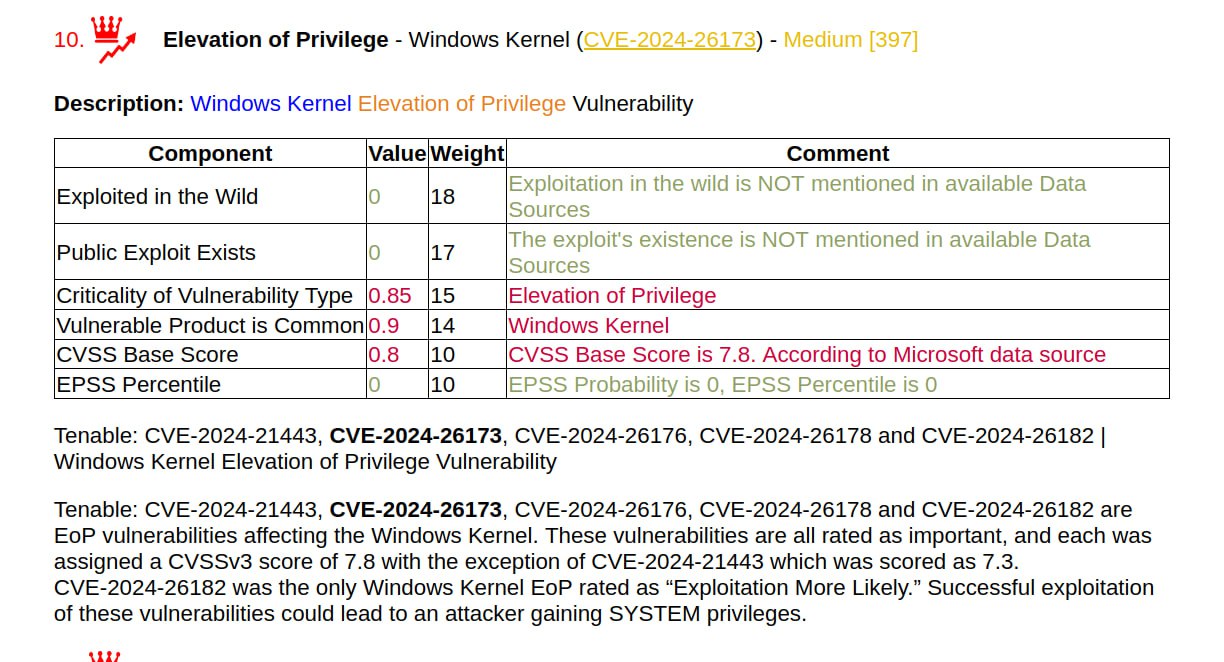
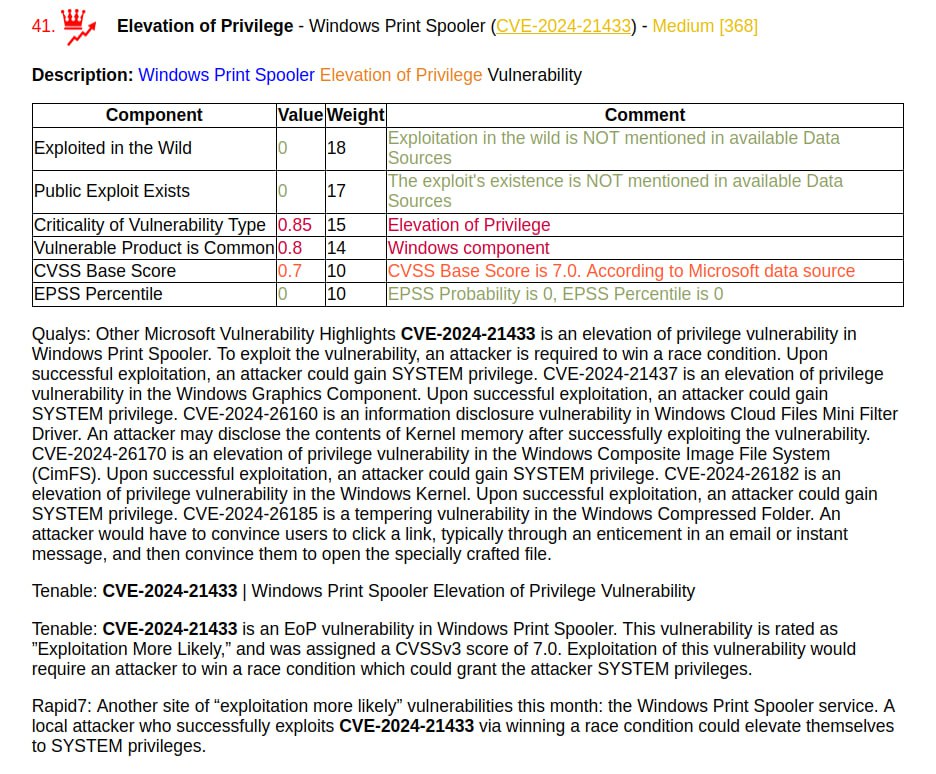
🔸 Elevation of Privilege – Windows Kernel (CVE-2024-21443, CVE-2024-26173, CVE-2024-26176, CVE-2024-26178, CVE-2024-26182). Such vulnerabilities often become exploitable recently. The same applies to Elevation of Privilege – Windows Print Spooler (CVE-2024-21433).
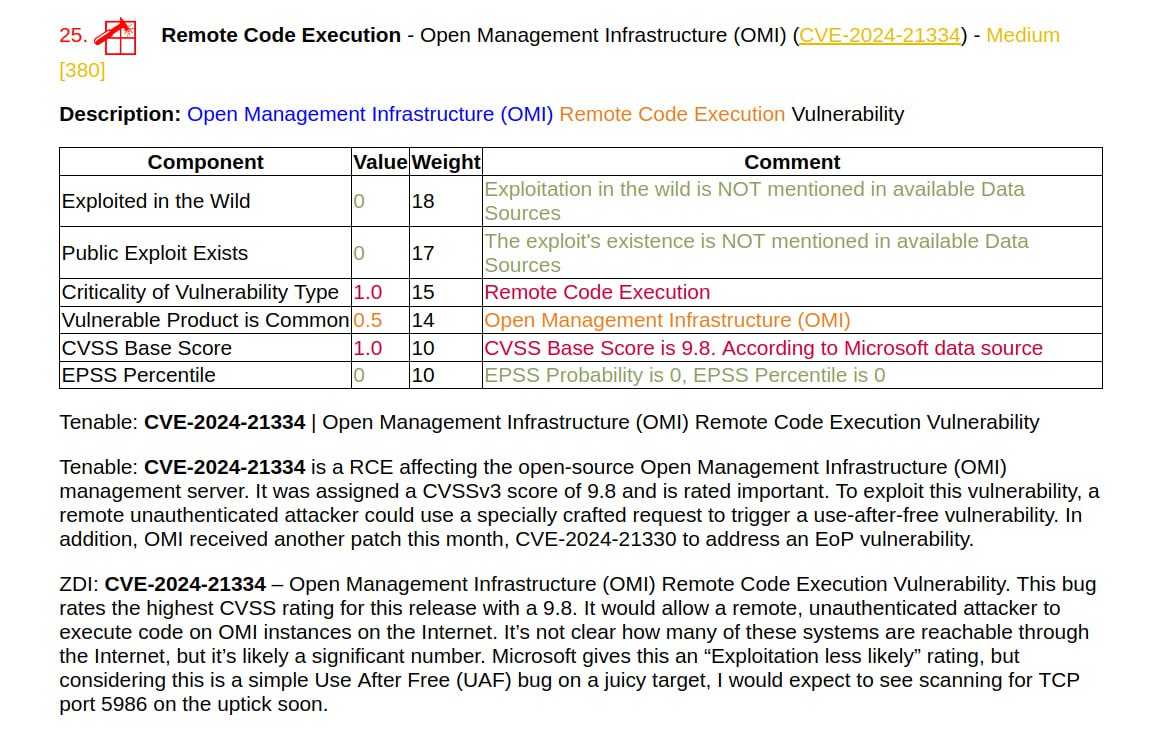
🔸 Remote Code Execution – Open Management Infrastructure (OMI) (CVE-2024-21334). CVSS 9.8 and ZDI write that “it would allow a remote, unauthenticated attacker to execute code on OMI instances on the Internet”. Perhaps such instances are indeed often accessible via the Internet, this requires research. 🤷♂️
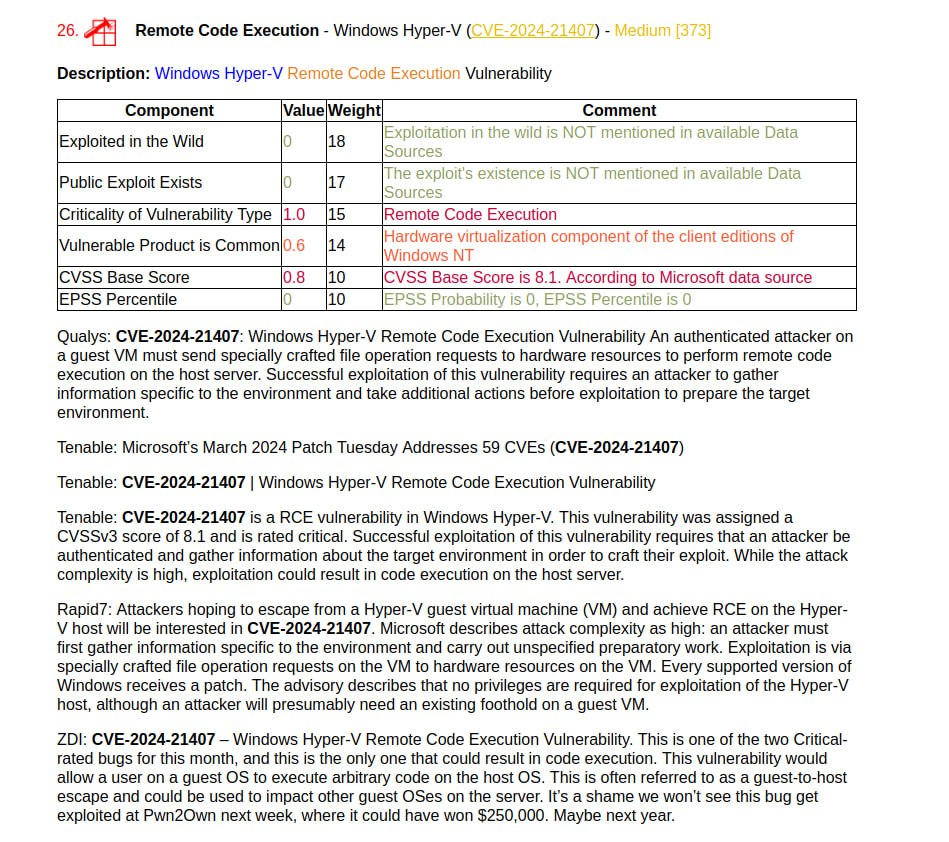
🔸 Remote Code Execution – Windows Hyper-V (CVE-2024-21407). This “guest-to-host escape” vulnerability was highlighted by everyone: Qualys, Tenable, Rapid7, ZDI.
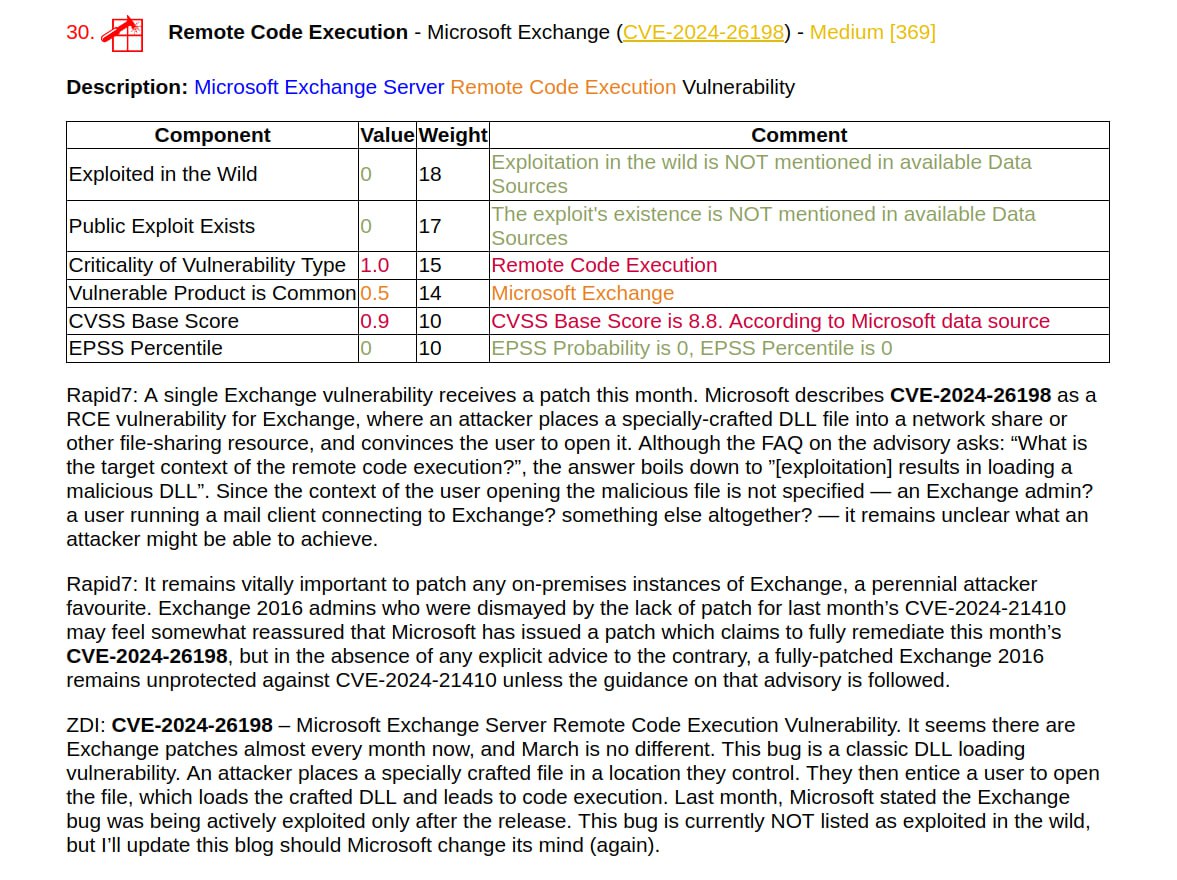
🔸 Remote Code Execution – Microsoft Exchange (CVE-2024-26198). This is a “DLL loading” vulnerability. The details are still unclear, but I wouldn’t be surprised if there will be a detailed write-up on it soon.

