Vulnerability Quadrants. Hi everyone! Today I would like talk about software vulnerabilities. How to find really interesting vulnerabilities in the overall CVE flow. And how to do it automatically.
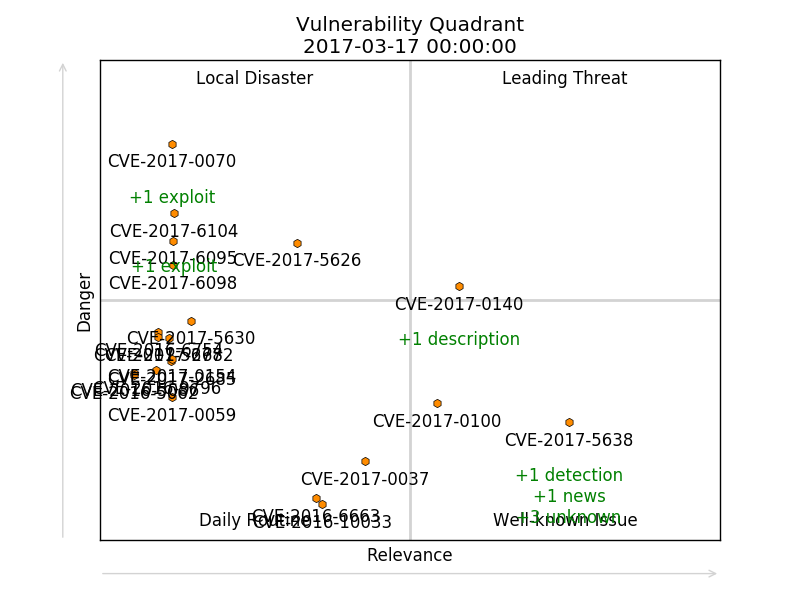
First of all, let’s talk why we may ever need to analyze software vulnerabilities? How people usually do their Vulnerability Management and Vulnerability Intelligence?

- Some people have a Vulnerability scanner, scan infrastructure with it, patch founded vulnerabilities and think that this will be enough.
- Some people pay attention to the vulnerabilities that are widely covered by media.
- Some people use vulnerability databases and search for the most critical vulnerabilities by some criteria.
Each of these ways have some advantages and some disadvantages.
