.audit-based Compliance Management in Nessus. In this post I will briefly describe how Nessus .audit-based Compliance Management works, why I like it, what could be improved and why I suppose Tenable won’t do it soon. 😉
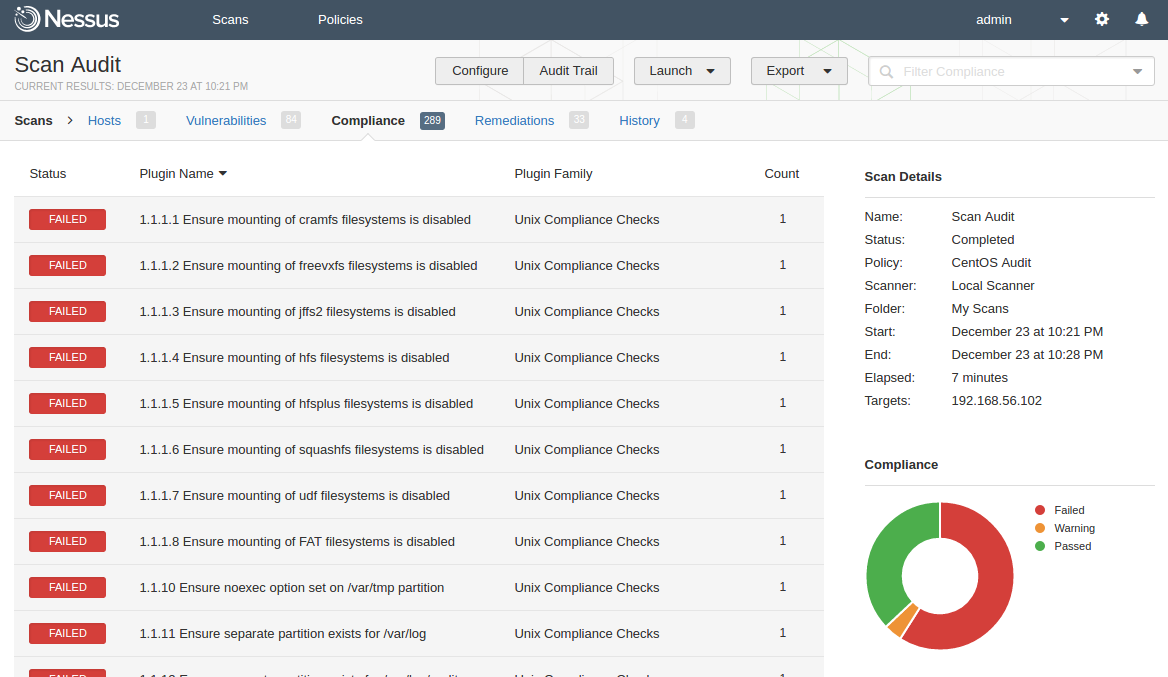
Nessus compliance checks are mainly presented in a form of special .audit scripts. This scripting language is very different from familiar NASL (Nessus Attack Scripting Language).
Basically, it is a collection of universal checks for various objects (e.g. existence of the line or parameter in the file, access permissions of the file, service status, etc.). Of course, nowadays Сompliance Management is not only about Operating System and software (mis)configuration. We have different network devices, databases, cloud services, etc. but originally it was the main case.
By combining the universal checks any requirement of low-level configuration standard (CIS, DISA, etc.) can be implemented. The similar principles are used in OVAL/SCAP content.
