Tracking changes in CERT bulletins and Nessus plugins using Vulners Time Machine. If you use Vulners.com vulnerability search engine, you probably know that it has a real “Time Machine”.

Each time Vulners sees some changes on a source page it creates a new version of security object. And you can see the full history of changes in a nice GUI:
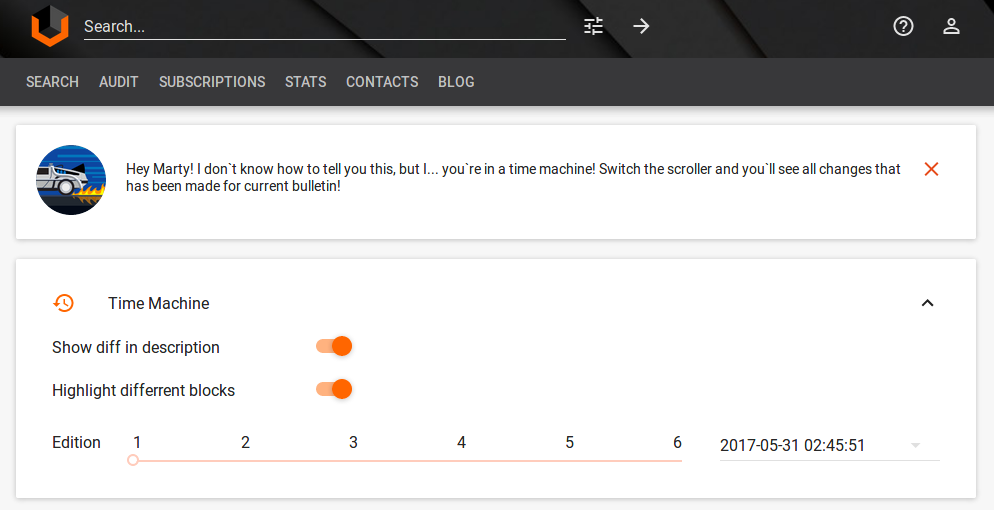
In most cases, the vendor just corrects typos or adds more details. But sometimes the message can change significantly.
CERT.org

For example, in a case of latest Meltdown and Spectre vulnerability. Initial cert.org VU:584653 recommendation was “Replace CPU hardware”. 🙂
It was changed like this:
2018-01-04 08:55:50
Replace CPU hardware. The underlying vulnerability is primarily caused by CPU architecture design choices. Fully removing the vulnerability requires replacing vulnerable CPU hardware.
2018-01-04 17:11:21
Replace CPU hardware. The underlying vulnerability is primarily caused by CPU implementation optimization choices. Fully removing the vulnerability requires replacing vulnerable CPU hardware.
2018-01-04 18:54:16
Apply updates. Operating system and some application updates mitigate these attacks.
Situation is getting much better. 😉 However, joking aside, it was very convenient to use this bulletin at Vulners.com to monitor the situation with released of patches, detection plugins and exploits in real time.
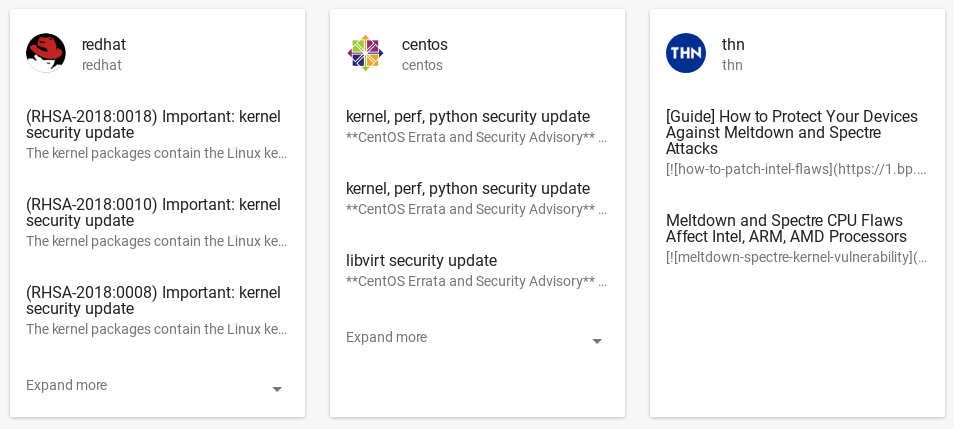
The only thing is that there is no Microsoft MS bulletins and KBs in Vulners. They should be tracked separately. 🙁
Nessus plugins

The second cool case, where you can use Vulners history. Imagine situation: Nessus stopped detecting vulnerability on some hosts, although no mitigation efforts were made. What kind of nonsense is that?
But we have Vulners. Find the plugin “SSL 64-bit Block Size Cipher Suites Supported (SWEET32)“. On the page, you can see that the plugin has been actually changed:
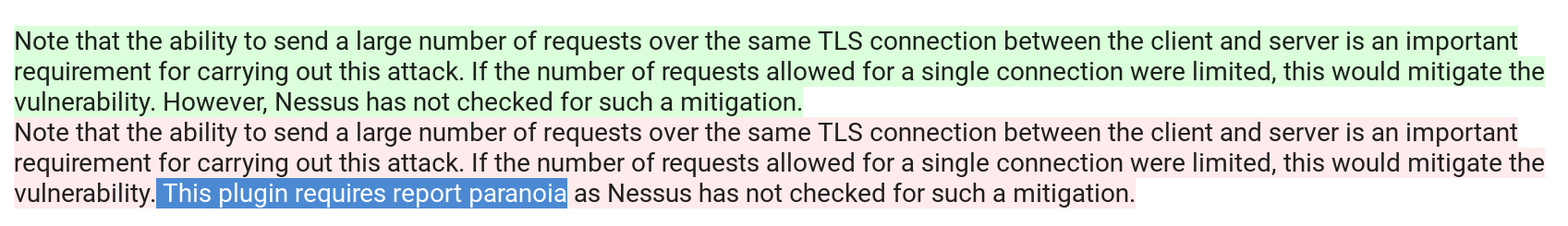
“This plugin requires report paranoia as Nessus has not checked for such a mitigation.” Now the plugin works only in paranoid mode. This is correct, because in practice this vulnerability is very difficult to exploit.
But anyway, Vulners is watching you, Tenable. All moves are recorded. 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
