Microsoft Patch Tuesday July 2023: Vulristics improvements, Office RCE, SFB SmartScreen and Outlook, EoP MSHTML and ERS, other RCEs. Hello everyone! This episode will be about Microsoft Patch Tuesday for July 2023, including vulnerabilities that were added between June and July Patch Tuesdays.
Alternative video link (for Russia): https://vk.com/video-149273431_456239131
As usual, I use my open source Vulristics project to analyse and prioritize vulnerabilities.
Vulristics improvements
I optimized the detection of the vulnerable product and the type of vulnerability based on the description. Now processing already downloaded data (with option --rewrite-flag "False") takes a few seconds. For example, only ~3 seconds for 100 MS Patch Tuesday vulnerabilities . It used to take a few minutes.
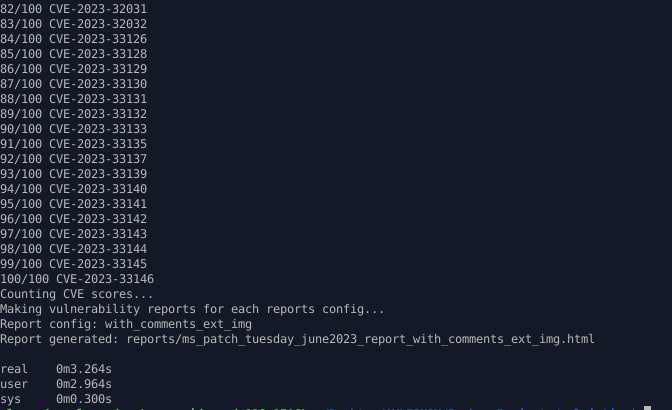
What I’ve done:
- For Microsoft generated descriptions, e.g. “Microsoft Excel Remote Code Execution Vulnerability”, vulnerability type and product are now directly parsed out of the description, keyword search is not performed.
- I rewrote the generic keyword search based on products.json. I have reduced the use of heavy functions without sacrificing the quality of the detections.
The bottleneck is downloading data from data sources. This should be resolved with own complete vulnerability feed, that could be generated by Vulristics. Thus, improving Vulristics, I am approaching the implementation of the feed. 😉
ADVs
Microsoft Patch Tuesday is not only about CVEs. Sometimes it is also about ADVs, as in the latest Patch Tuesday:
🔻ADV230001 – Guidance on Microsoft Signed Drivers Being Used Maliciously
🔻ADV230002 – Microsoft Guidance for Addressing Security Feature Bypass in Trend Micro EFI Modules
Sometimes the corresponding CVE is mentioned in the ADV description, sometimes it’s not. I don’t know why they do this and why they simply can’t use existing CVEs or allocate their own CVEs (since ADV is in the “update-guide/vulnerability/” section, and Microsoft is CVE Numbering Authority). But here’s the fact – MS use vulnerability IDs that can’t be used for mapping. 😑
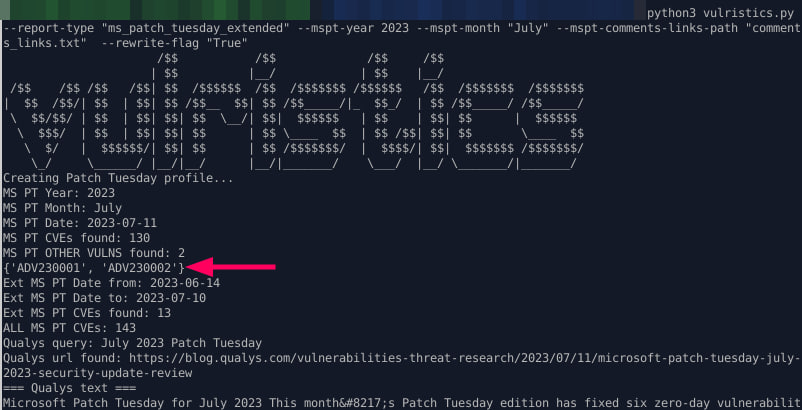
For now, I just ignore them and show them when generating the Vulristics report.
Vulristics comments
For Microsoft Patch Tuesday, July 2023, I took comments about vulnerabilities from reviews of:
🔹Qualys
🔹Tenable
🔹Rapid7
🔹ZDI
🔹Kaspersky
🔹Dark Reading
🔹Krebs on Security
🔹The Hacker News
🔹Sophos Naked Security
I tweaked the Vulristics reports a bit. Now you can see the criticality of the vulnerabilities that were mentioned in each of the comment sources.
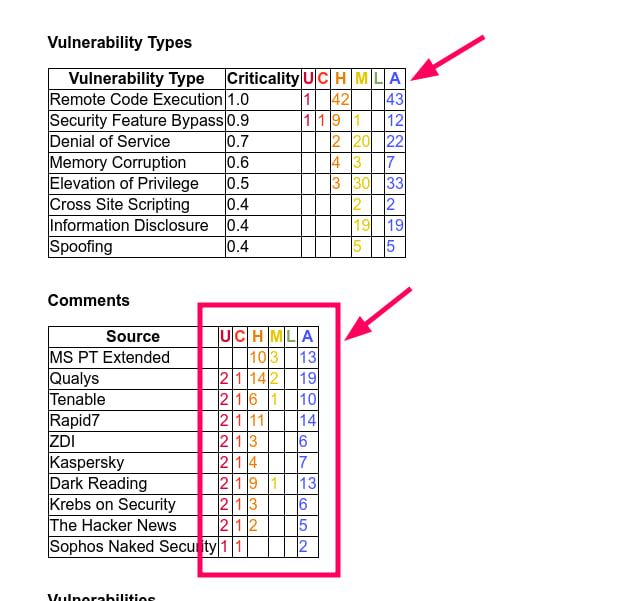
VM vendors (Qualys, Tenable, Rapid7) mention more vulnerabilities in their reviews. As well as Dark Reading. Sophos, for example, only mentions the very, very TOP. ZDI actually mentions a lot of vulnerabilities too, but most of them are simply listed in a table with a minimum of columns – so i ignore this.
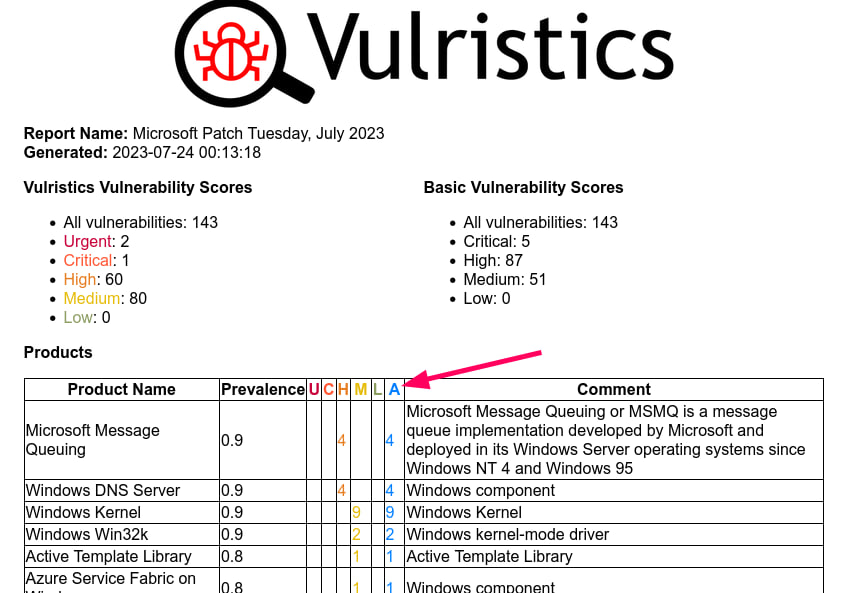
I also added the All (A) column to all tables with the total number of vulnerabilities for the product, type of vulnerabilities, or comment source.
Microsoft Patch Tuesday July 2023
$ cat comments_links.txt
Qualys|Microsoft and Adobe Patch Tuesday, July 2023 Security Update Review|https://blog.qualys.com/vulnerabilities-threat-research/2023/07/11/microsoft-patch-tuesday-july-2023-security-update-review
ZDI|THE JULY 2023 SECURITY UPDATE REVIEW|https://www.thezdi.com/blog/2023/7/10/the-july-2023-security-update-review
Kaspersky|Band-aid on a… corpse: Microsoft patches IE — again|https://www.kaspersky.com/blog/microsoft-patch-tuesday-july-2023/48606/
Dark Reading|Microsoft Discloses 5 Zero-Days in Voluminous July Security Update|https://www.darkreading.com/application-security/microsoft-discloses--zero-days-in-voluminous-july-security-update
Krebs on Security|Apple & Microsoft Patch Tuesday, July 2023 Edition|https://krebsonsecurity.com/2023/07/apple-microsoft-patch-tuesday-july-2023-edition/
The Hacker News|Microsoft Releases Patches for 132 Vulnerabilities, Including 6 Under Active Attack|https://thehackernews.com/2023/07/microsoft-releases-patches-for-130.html
Sophos Naked Security|Microsoft patches four zero-days, finally takes action against crimeware kernel drivers|https://nakedsecurity.sophos.com/2023/07/12/microsoft-patches-four-zero-days-finally-takes-action-against-crimeware-kernel-drivers/
$ python3 vulristics.py --report-type "ms_patch_tuesday_extended" --mspt-year 2023 --mspt-month "July" --mspt-comments-links-path "comments_links.txt" --rewrite-flag "True"
...
Creating Patch Tuesday profile...
MS PT Year: 2023
MS PT Month: July
MS PT Date: 2023-07-11
MS PT CVEs found: 130
MS PT OTHER VULNS found: 2
{'ADV230001', 'ADV230002'}
Ext MS PT Date from: 2023-06-14
Ext MS PT Date to: 2023-07-10
Ext MS PT CVEs found: 13
ALL MS PT CVEs: 143
...So now let’s go directly to MS Patch Tuesday CVEs 🙂
- All vulnerabilities: 143
- Urgent: 2
- Critical: 1
- High: 62
- Medium: 78
- Low: 0
Remote Code Execution – Microsoft Office (CVE-2023-36884) definitely catches the eye. This vulnerability even has a normal description, and not a minimal one. Exploitation of this vulnerability began in June 2023. Exploitation requires the victim to open a specially crafted malicious document, which would typically be delivered via email. In the blog, Microsoft mentioned that the attacks were targeted against defense and government entities in Europe and North America. There are still no patches, only workarounds. In the absence of a patch, Microsoft is urging users to use the “Block all Office applications from creating child processes” attack surface reduction (ASR) rule.
Also actively exploited:
🔻Security Feature Bypass – Windows SmartScreen (CVE-2023-32049). Windows SmartScreen is an early warning system designed to protect against malicious websites used for phishing attacks or malware distribution. An attacker must make the users click on a specially crafted URL to exploit the vulnerability. Exploitation would allow the attacker to bypass the “Open File” warning prompt and compromise the victim’s machine.
🔻Security Feature Bypass – Microsoft Outlook (CVE-2023-35311). Exploitation of this flaw requires an attacker to convince a potential victim to click on a malicious URL. Successful exploitation would result in the bypassing of the Microsoft Outlook Security Notice prompt, a feature designed to protect users. Microsoft says that while its Outlook Preview pane feature is an attack vector, user interaction is still required. This is likely being paired with some other exploit designed to execute code when opening a file.
🔻Elevation of Privilege – Windows Error Reporting Service (CVE-2023-36874). To elevate to administrative privileges, an attacker would need to have access to a user account with the ability to create folders and performance traces on the target system. Standard user accounts don’t have these permissions by default. Successful exploitation would allow an attacker to obtain administrative privileges on the target system.
🔻Elevation of Privilege – Windows MSHTML Platform (CVE-2023-32046). Windows MSHTML is a browser engine that renders web pages frequently connected to Internet Explorer. Successful exploitation requires the victim to open a specially-crafted malicious file, typically delivered either via email or a web page. Assets where Internet Explorer 11 has been fully disabled are still vulnerable until patched; the MSHTML engine remains installed within Windows regardless of the status of IE11, since it is used in other contexts (e.g. Outlook).
These are all vulnerabilities that have a public exploit or are exploited in the wild. Let’s see the rest.
There are no Exchange vulnerabilities, but there is an intriguing Remote Code Execution – Windows Active Directory Certificate Services (AD CS) (CVE-2023-35350). But, judging by the Microsoft description, this is not particularly critical. An attacker with Certificate Authority (CA) read access permissions can send a specially crafted request to a vulnerable Certificate Server. By default, only domain administrators are granted CA read access.
Additionally, the following RCEs highlighted in the reviews, can be noted:
🔸Microsoft Message Queuing (CVE-2023-32057, CVE-2023-35309). An attacker must send a malicious MSMQ packet to an MSMQ server to exploit this vulnerability. On successful exploitation, an attacker may perform remote code execution on the server side. You can block TCP port 1801 as a mitigation, but the better choice is to test and deploy the update quickly.
🔸Windows Routing and Remote Access Service (RRAS) (CVE-2023-35365, CVE-2023-35366, CVE-2023-35367). Exploitation requires an attacker to send crafted packets to an impacted server. RRAS is not installed or configured in Windows by default and those users who have not enabled the feature are not impacted by these vulnerabilities.
🔸Windows Layer-2 Bridge Network Driver (CVE-2023-35315). An unauthenticated attacker must send specially crafted file operation requests to a Windows Server configured as a Layer-2 Bridge to exploit the vulnerability. An attacker must gain access to the restricted network before running an attack. Successful exploitation of the vulnerability will lead to remote code execution on the target system.
🔸Microsoft SharePoint (CVE-2023-33134, CVE-2023-33157, CVE-2023-33159, CVE-2023-33160). They all require the attacker to authenticate or the user to perform certain actions, and this, fortunately, reduces the risk of hacking. However, because SharePoint can contain sensitive data and is usually accessible from outside the organization, those who use the on-premises or hybrid versions should update.
🔸Windows Pragmatic General Multicast (PGM) (CVE-2023-35297). Pragmatic General Multicast (PGM) is a multicast computer network transport protocol appropriate for multi-receiver file transfer applications. PGM provides a reliable sequence of packets to multiple recipients simultaneously. An attack can be performed only on the systems connected to the same network segment as the attacker. The attack cannot be performed across multiple networks (for example, a WAN).
Full Vulristics report: ms_patch_tuesday_july2023

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Традиционный аудио/видео эпизод по итогам июльского Microsoft Patch Tuesday | Александр В. Леонов