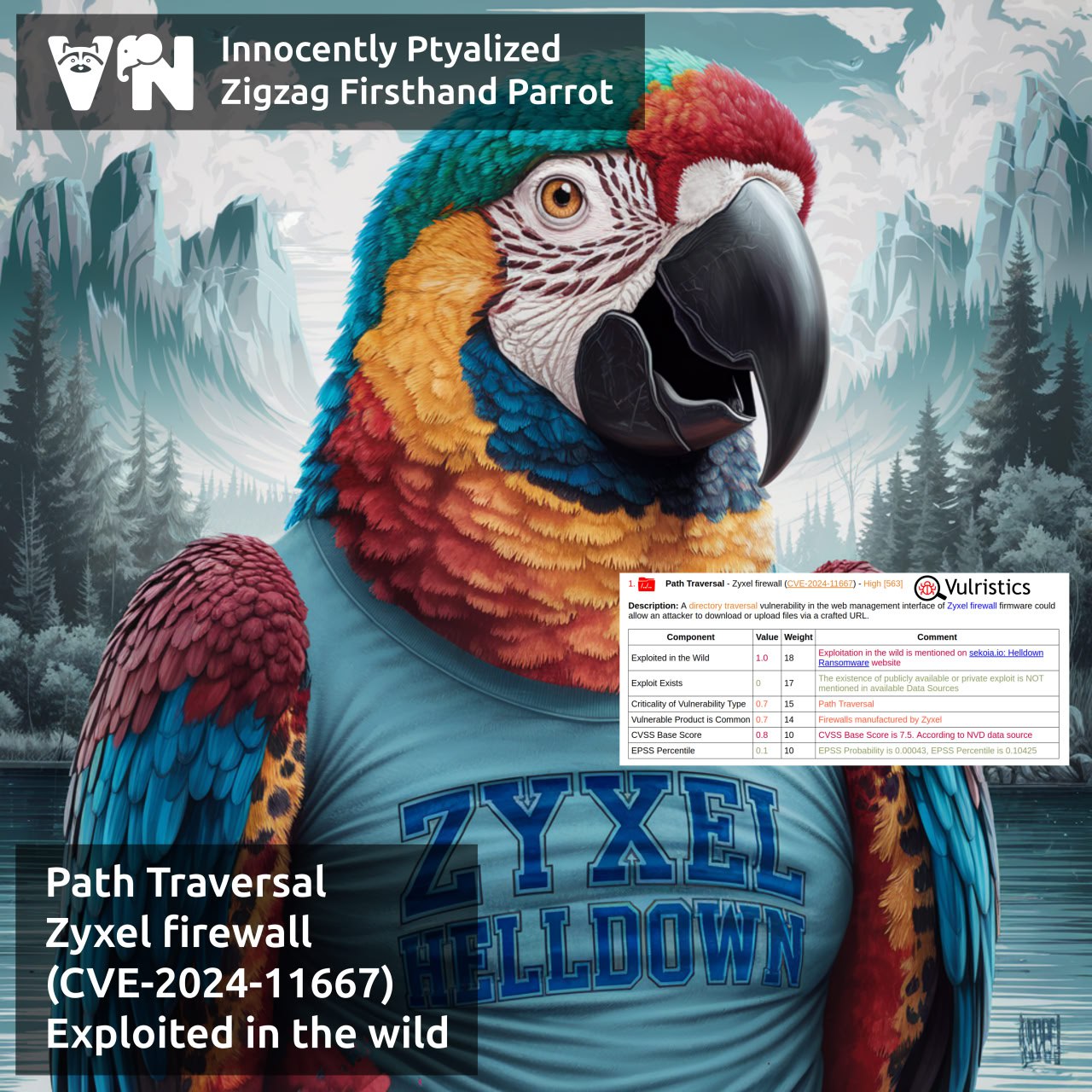
About Path Traversal – Zyxel firewall (CVE-2024-11667) vulnerability. A directory traversal vulnerability in the web management interface of Zyxel firewall could allow an attacker to download or upload files via a crafted URL. The vulnerability affects Zyxel ZLD firmware versions from 5.00 to 5.38, used in the ATP, USG FLEX, USG FLEX 50(W), and USG20(W)-VPN device series.
👾 Specialists from Sekoia discovered this vulnerability being exploited on their honeypots by ransomware attackers from the Helldown group. There are no public exploits yet.
Zyxel recommends:
🔹Update firmware to version 5.39, which was released on September 3, 2024
🔹Disable remote access until devices are updated
🔹Learn best practices for device configuration
If your company uses Zyxel firewalls, please pay attention. 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.


Pingback: New episode “In The Trend of VM” (#10): 8 trending vulnerabilities of November, zero budget VM and who should look for patches | Alexander V. Leonov