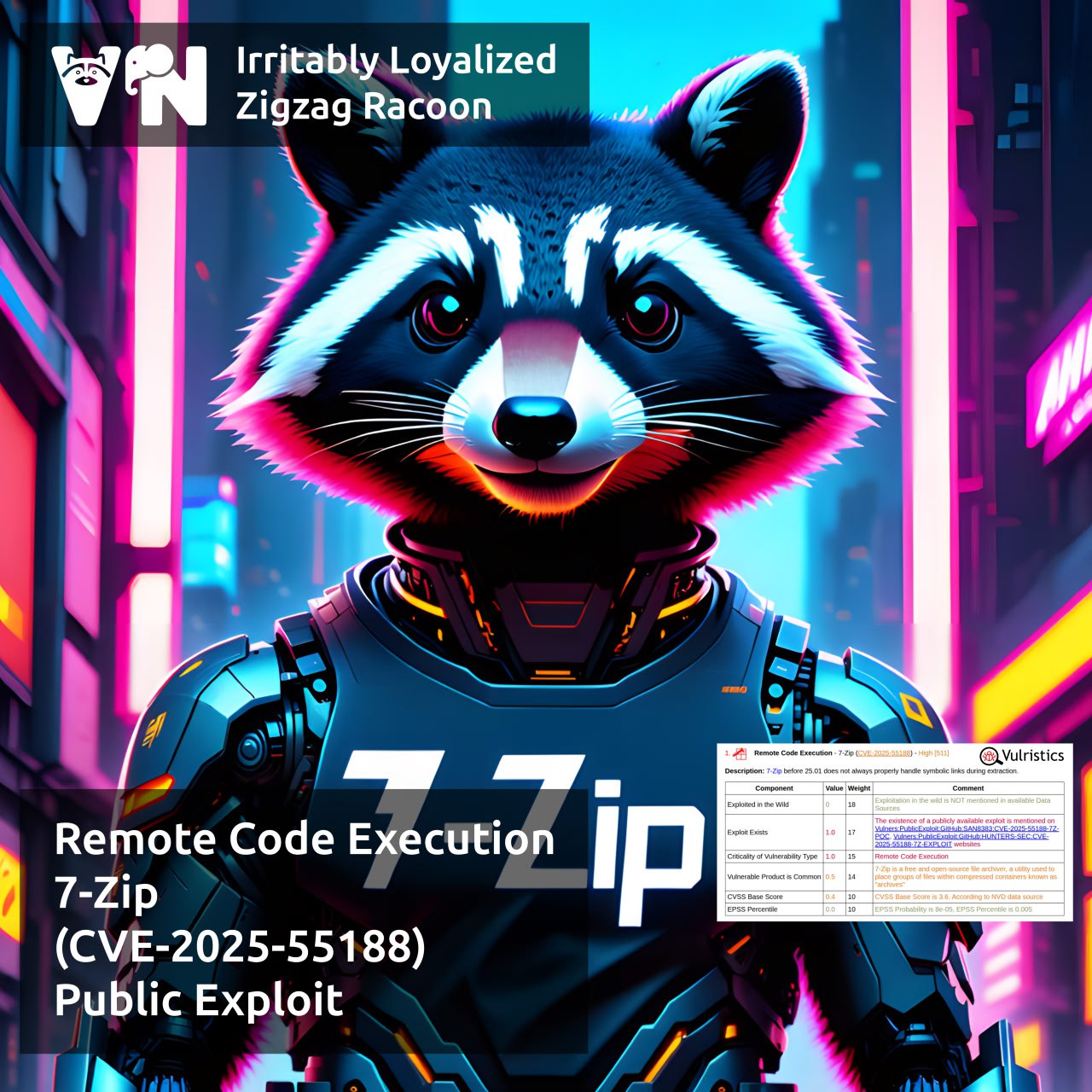
About Remote Code Execution – 7-Zip (CVE-2025-55188) vulnerability. 7-Zip is a popular open-source archiver. It’s a Windows application, but the project also provides command-line versions for Linux and macOS. The gist of the vulnerability: 7-Zip improperly handles symbolic links and, when extracting a specially crafted archive, can overwrite arbitrary files outside the extraction directory. Sounds like the recent WinRAR vulnerability, right? 😉
🔻 It’s mainly exploited on Linux. Attackers can overwrite SSH keys, startup (autostart) scripts, etc.
🔻 Exploitation is also possible on Windows, but the 7-Zip extraction process must have permission to create symlinks (requires running as Administrator or enabling Developer Mode). 🤔
🩹 The vulnerability was fixed in 7-Zip 25.01, released on August 3.
🛠 The researcher lunbun reported it on Aug 9 and posted a write-up on Aug 28. PoCs have been available on GitHub since Aug 11.
👾 No signs of in-the-wild exploitation so far.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.