Vulners.com search API. Upd. Vulners released updated Vulners API. What is written below is still working. But now it’s all this can be done much easier.
The greatest thing is “references=true”. It makes possible to get all the referenced objects (exploits, detection plugins, etc.) and bulletin description in ONE search request.
So, for example bellow this query will be enough: https://vulners.com/api/v3/search/lucene/?query=cvss.score:10%20type:centos%20order:published&references=true
Life is getting better! 😉
In a previous post I made a brief review of Vulners.com security content database and search engine. Today let’s see how to automate searching of vulnerabilities, exploits, patches, bugbounty results, etc, with vulners.com search API.

It is really easy. We just need to send POST-request to https://vulners.com/api/v1/luceneSearch/ with JSON structure containing search query, size of results you want to get (10000 is maximum), and number of search result entities you would like to skip (optional). Huge size parameter limit makes possible, for example, getting all 2267 CentOS security bulletins with only one request. At the moment, no authorization is required to make requests and no limits for API use exist. Of course, the service is in active development phase and this functionality may be changed soon.
So, let’s get latest CentOS bulletin with most critical vulnerability:
curl -H "Content-Type: application/json" -X POST -d '{"query":"cvss.score:10 type:centos order:published", "size":1}' https://vulners.com/api/v1/luceneSearch/ | python -m json.tool
(json.tool for pretty printing)
{
"exactMatch": null,
"results": [
{
"_id": "CESA-2015:0806",
"_index": "bulletins",
"_score": null,
"_source": {
"affectedPackage": [
{
"OS": "CentOS",
"OSVersion": "6",
"arch": "i686",
"operator": "lt",
"packageFilename": "java-1.7.0-openjdk-1.7.0.79-2.5.5.1.el6_6.i686.rpm",
"packageName": "java-1.7.0-openjdk",
"packageVersion": "1.7.0.79-2.5.5.1.el6_6"
},
--[ Lot's of packages ]--
{
"OS": "CentOS",
"OSVersion": "7",
"arch": "x86_64",
"operator": "lt",
"packageFilename": "java-1.7.0-openjdk-demo-1.7.0.79-2.5.5.1.el7_1.x86_64.rpm",
"packageName": "java-1.7.0-openjdk-demo",
"packageVersion": "1.7.0.79-2.5.5.1.el7_1"
}
],
"bulletinFamily": "unix",
"cvelist": [
"CVE-2005-1080",
"CVE-2015-0460",
"CVE-2015-0480",
"CVE-2015-0469",
"CVE-2015-0477",
"CVE-2015-0478",
"CVE-2015-0488"
],
"cvss": {
"score": 10.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:COMPLETE/I:COMPLETE/A:COMPLETE/"
},
"description": "Upstream details at : https://rhn.redhat.com/errata/RHSA-2015-0806.html\nUpdate to the following versions:\nCentOS 6:\n\t- java-1.7.0-openjdk-1.7.0.79-2.5.5.1.el6_6.i686.rpm\n\t- java-1.7.0-openjdk-1.7.0.79-2.5.5.1.el6_6.src.rpm\n\t- java-1.7.0-openjdk-1.7.0.79-2.5.5.1.el6_6.x86_64.rpm\n\t- java-1.7.0-openjdk-demo-1.7.0.79-2.5.5.1.el6_6.i686.rpm\n\t- java-1.7.0-openjdk-demo-1.7.0.79-2.5.5.1.el6_6.x86_64.rpm\n\t- java-1.7.0-openjdk-devel-1.7.0.79-2.5.5.1.el6_6.i686.rpm\n\t- java-1.7.0-openjdk-devel-1.7.0.79-2.5.5.1.el6_6.x86_64.rpm\n\t- java-1.7.0-openjdk-javadoc-1.7.0.79-2.5.5.1.el6_6.noarch.rpm\n\t- java-1.7.0-openjdk-src-1.7.0.79-2.5.5.1.el6_6.i686.rpm\n\t- java-1.7.0-openjdk-src-1.7.0.79-2.5.5.1.el6_6.x86_64.rpm\nCentOS 7:\n\t- java-1.7.0-openjdk-1.7.0.79-2.5.5.1.el7_1.src.rpm\n\t- java-1.7.0-openjdk-1.7.0.79-2.5.5.1.el7_1.x86_64.rpm\n\t- java-1.7.0-openjdk-accessibility-1.7.0.79-2.5.5.1.el7_1.x86_64.rpm\n\t- java-1.7.0-openjdk-demo-1.7.0.79-2.5.5.1.el7_1.x86_64.rpm\n\t- java-1.7.0-openjdk-devel-1.7.0.79-2.5.5.1.el7_1.x86_64.rpm\n\t- java-1.7.0-openjdk-headless-1.7.0.79-2.5.5.1.el7_1.x86_64.rpm\n\t- java-1.7.0-openjdk-javadoc-1.7.0.79-2.5.5.1.el7_1.noarch.rpm\n\t- java-1.7.0-openjdk-src-1.7.0.79-2.5.5.1.el7_1.x86_64.rpm",
"hash": "093c3c4926cddc59c5cb7d0f6481862254eea904c09348726336c78b2688eb85",
"href": "http://lists.centos.org/pipermail/centos-announce/2015-April/021066.html",
"id": "CESA-2015:0806",
"lastseen": "2016-01-29T21:59:49",
"modified": "2015-04-15T00:00:00",
"objectVersion": "1.0",
"published": "2015-04-15T00:00:00",
"references": [
"http://lists.centos.org/pipermail/centos-announce/2015-April/021066.html",
"http://lists.centos.org/pipermail/centos-announce/2015-April/021069.html"
],
"reporter": "CentOS Project",
"title": "CentOS Errata and Security Advisory (Critical)",
"type": "centos"
},
"_type": "bulletin",
"highlight": {
"affectedPackage.OS": [
"CentOS",
"CentOS",
"CentOS",
"CentOS"
],
"description": [
" versions:\nCentOS 6:\n\t- java-1.7.0-openjdk-1.7.0.79-2.5.5.1.el6_6.i686.rpm\n\t- java-1.7.0-openjdk",
".rpm\nCentOS 7:\n\t- java-1.7.0-openjdk-1.7.0.79-2.5.5.1.el7_1.src.rpm\n\t- java-1.7.0-openjdk-1.7.0.79"
],
"href": [
"http://lists.centos.org/pipermail/centos-announce/2015-April/021066.html"
],
"references": [
"http://lists.centos.org/pipermail/centos-announce/2015-April/021066.html",
"http://lists.centos.org/pipermail/centos-announce/2015-April/021069.html"
],
"reporter": [
"CentOS Project"
],
"title": [
"CentOS Errata and Security Advisory (Critical)"
],
"type": [
"centos"
]
},
"sort": [
1429056000000
]
}
]
}
We can see bulletin id, bulletin type, all patched packages, description of the bulletin, related CVEs, CVSS score and vector, other technical information.
However, we don’t see references to related Nessus plugins, security bulletins, discussions. As we see on the webdsite, CESA-2015:0806 has a lot of such references.
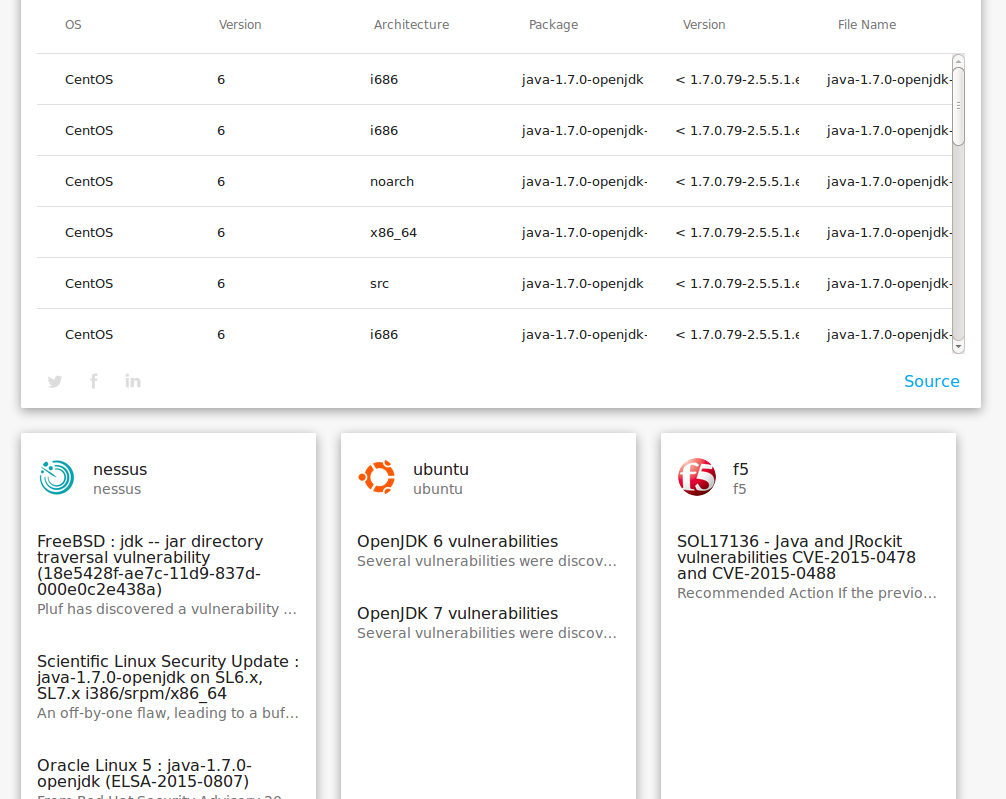
At the moment, we can get it only from the html code of bulletin page. We need this “{\”result\”.*” JSON part:
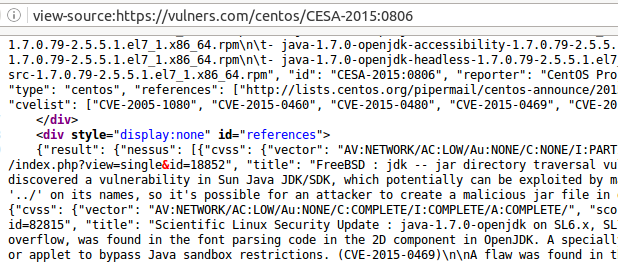
curl https://vulners.com/centos/CESA-2015:0806 | grep "{\"result\"" | python -m json.tool
Here is a small part of the JSON with a reference to Nessus detection plugin CENTOS_RHSA-2015-0806.NASL:
{
"cvelist": [
"CVE-2005-1080",
"CVE-2015-0477",
"CVE-2015-0478",
"CVE-2015-0480",
"CVE-2015-0488",
"CVE-2015-0469",
"CVE-2015-0460"
],
"cvss": {
"score": 10.0,
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:COMPLETE/I:COMPLETE/A:COMPLETE/"
},
"description": "Updated java-1.7.0-openjdk packages that fix multiple security issues are now available for Red Hat Enterprise Linux 6 and 7.\n\nRed Hat Product Security has rated this update as having Critical security impact. --[Long description]-- All users of java-1.7.0-openjdk are advised to upgrade to these updated packages, which resolve these issues. All running instances of OpenJDK Java must be restarted for the update to take effect.",
"href": "https://www.tenable.com/plugins/index.php?view=single&id=82801",
"id": "CENTOS_RHSA-2015-0806.NASL",
"lastseen": "2016-03-19T06:14:51",
"published": "2015-04-16T00:00:00",
"title": "CentOS 6 / 7 : java-1.7.0-openjdk (CESA-2015:0806)",
"type": "nessus"
},
As we see, format is quite similar: list of CVEs, CVSS vector and score, description, link to plugin description on Tenable website, plugin id, title, entity type and dates when plugin was published and was seen by Nessus parser for the last time.
These two requests will be enough to automate the search process.
In conclusion, one more example of “skip” parameter use. Let’s get the second latest CentOS bulletin with critical vulnerability. Request will be:
curl -H "Content-Type: application/json" -X POST -d '{"query":"cvss.score:10 type:centos order:published", "size":1, "skip":1}' https://vulners.com/api/v1/luceneSearch/ | python -m json.tool

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Have you heard about vulners.com? | Alexander V. Leonov
Pingback: PCI DSS 3.2 and Vulnerability Intelligence | Alexander V. Leonov
Pingback: Vulners.com vulnerability detection plugins for Burp Suite and Google Chrome | Alexander V. Leonov
Pingback: ISACA Moscow Vulnerability Management Meetup 2018 | Alexander V. Leonov