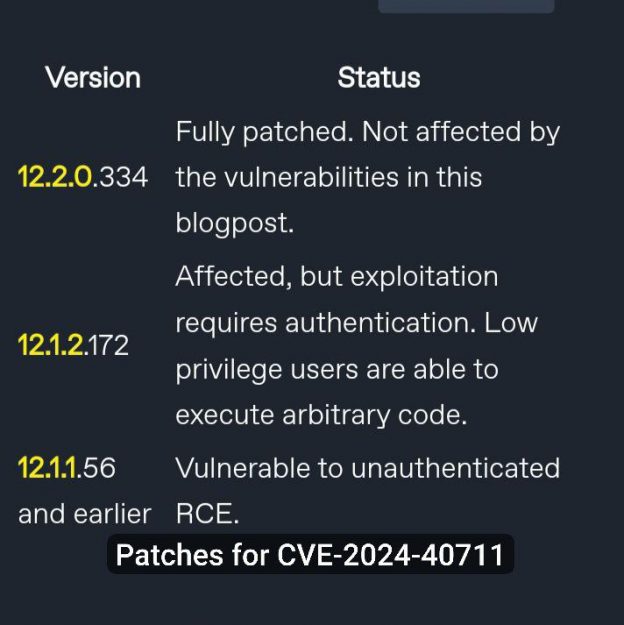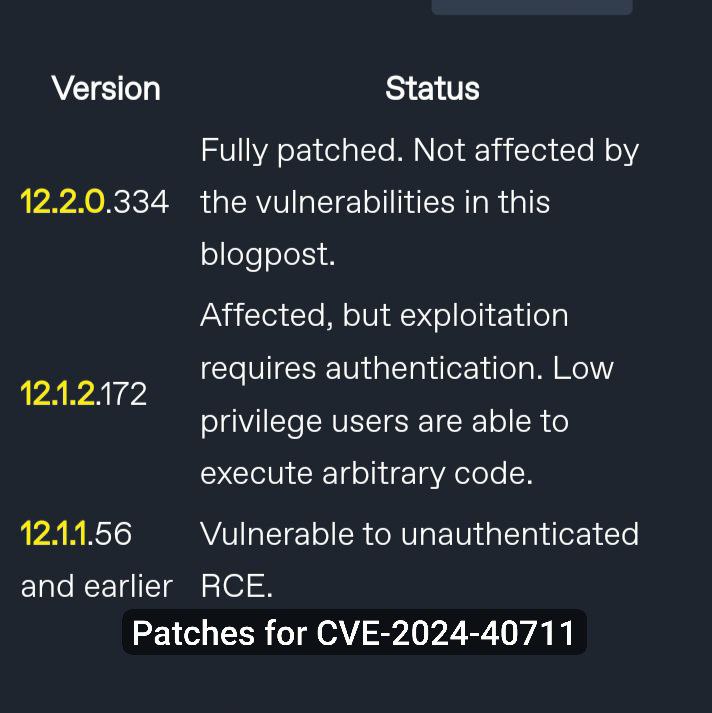
watchTowr Labs draws attention to some oddities with the fix for the Remote Code Execution – Veeam Backup & Replication vulnerability (CVE-2024-40711).
🔹 The description of the vulnerability in NVD tells us that authentication is not required to exploit the vulnerability, but the CVSS vector in the vendor bulletin indicates that authentication is required (“PR:L”).
🔹 The large number of changes in the patch hints that the vendor fixed some vulnerabilities without informing customers (silent patching).
🔹 The researchers concluded that CVE-2024-40711 was fixed in several stages. At first, exploitation of the vulnerability did not require authentication, then a patch was released and exploitation began to require authentication, and finally, the second patch completely fixed this vulnerability.
❗ Exploitation of the vulnerability allows an attacker to destroy backups and significantly complicate the restoration of the organization’s infrastructure.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.