November “In the Trend of VM” (#21): vulnerabilities in Windows, SharePoint, Redis, XWiki, Zimbra Collaboration, and Linux. The usual monthly roundup. After several months, here’s a big one. 🔥
🗞 Post on Habr (rus)
🗞 Post on SecurityLab (rus)
🗒 Digest on the PT website (rus)
A total of nine vulnerabilities:
🔻 RCE – Windows Server Update Services (WSUS) (CVE-2025-59287)
🔻 RCE – Microsoft SharePoint “ToolShell” (CVE-2025-49704)
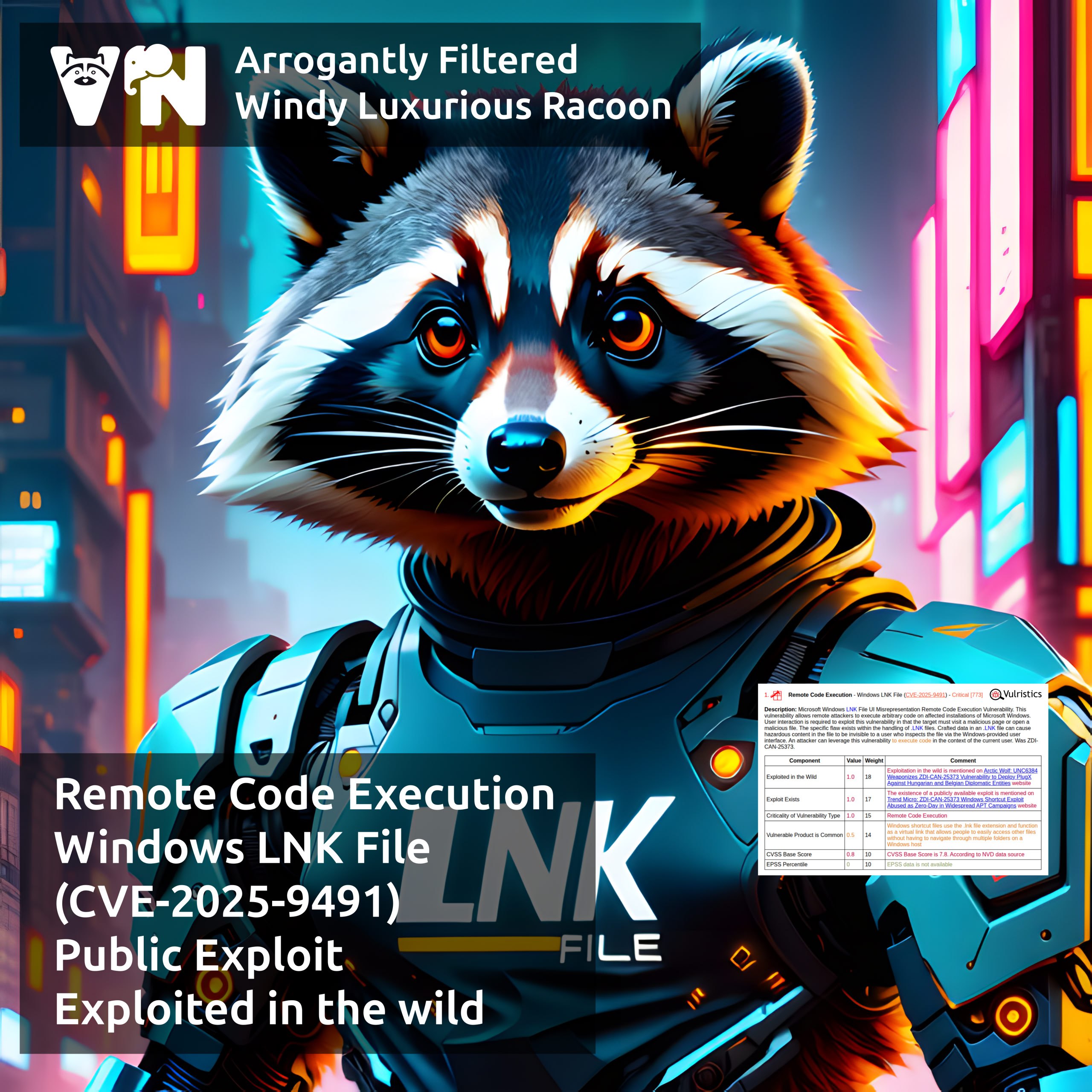
🔻 RCE – Windows LNK File (CVE-2025-9491)
🔻 EoP – Windows Remote Access Connection Manager (CVE-2025-59230)
🔻 EoP – Windows Agere Modem Driver (CVE-2025-24990)
🔻 RCE – Redis “RediShell” (CVE-2025-49844)
🔻 RCE – XWiki Platform (CVE-2025-24893)
🔻 XSS – Zimbra Collaboration (CVE-2025-27915)
🔻 EoP – Linux Kernel (CVE-2025-38001)