October “In the Trend of VM” (#20): vulnerabilities in Cisco ASA/FTD and sudo. A traditional monthly roundup. This time, once again, no Microsoft vulnerabilities. 😲
🗞 Post on Habr (rus)
🗞 Post on SecurityLab (rus)
🗒 Digest on the PT website (rus)
Only three identifiers in total:
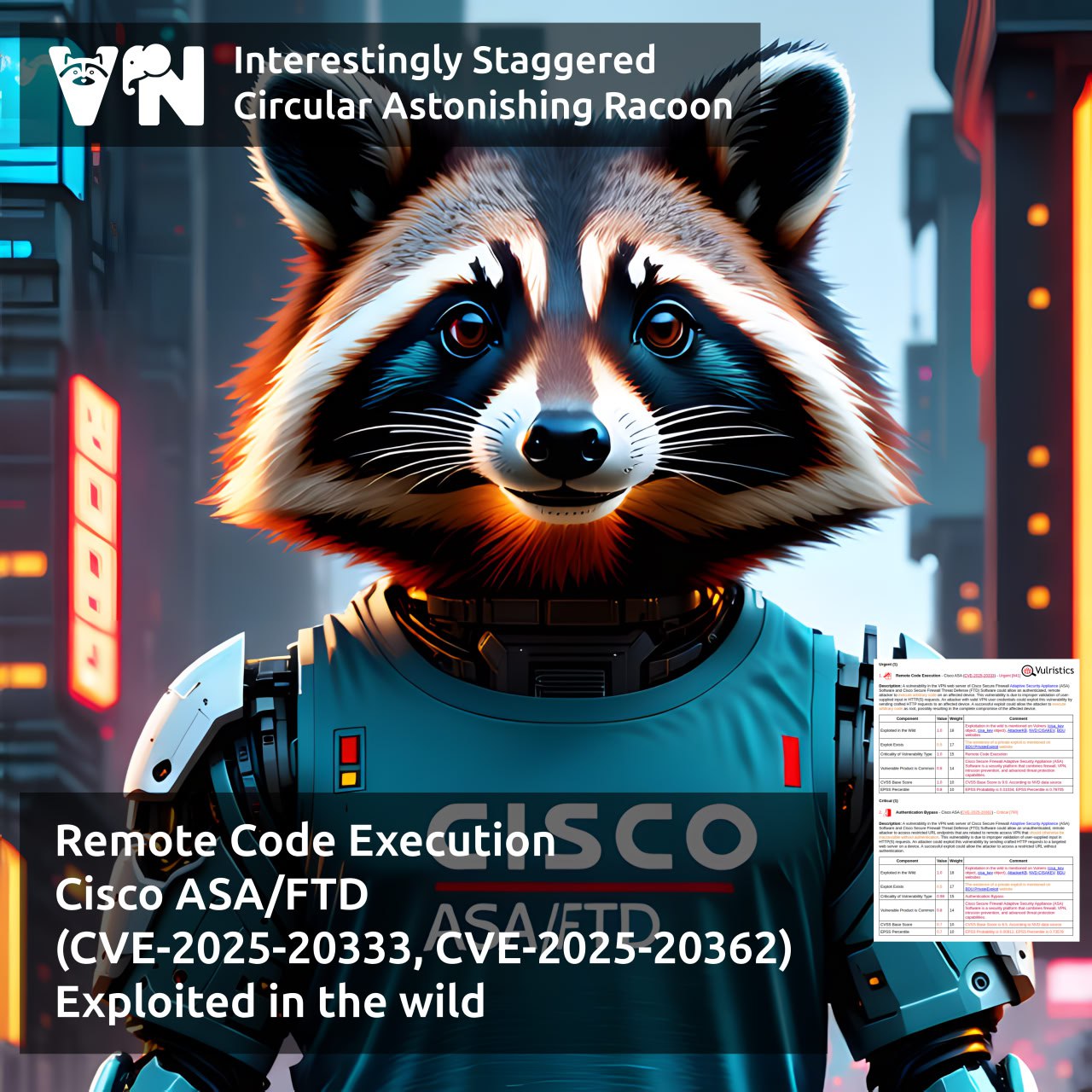
🔻 Remote Code Execution – Cisco ASA/FTD (CVE-2025-20333, CVE-2025-20362). This vulnerability chain has been exploited in attacks since May 2025, but there are no public exploits yet.
🔻 Elevation of Privilege – Sudo (CVE-2025-32463). There are signs of in-the-wild exploitation and many public exploits are available.