Forever “reserved” CVEs. In this post I would like to provide some links, that you can use to find out necessary information about vulnerability by its CVE ID. I also want to share my amazement, how the method of using the CVE identifiers is changing.

Traditionally, CVE was a global identifier that most of vulnerabilities had. Have you found malicious bug in some software? Send a brief description to MITRE and you will receive CVE id. Some time later NIST will analyze this CVE, will add CVSS vector and CPEs and will put a new item to the NVD database. MITRE and NVD CVE databases were really useful source of information.
Times change. Now typical is a situation, that some researcher (mostly a big company) publish a report with some CVE id. You go to MITRE and see “reserved”, than you go NVD and of course there is no such id. If issue is important, lots of people will discuss it using the id for references. But in MITRE and NVD description of this vulnerability will appear with a HUGE latency.
For example, last week critical vulnerability in Adobe Flash. It was discovered by researchers from Google’s Threat Analysis Group. Adobe released Adobe Security Bulletin APSB16-36 at October 26, 2016. It uses CVE-2016-7855 id.
Todays is the 1st of November. Let’s see the links:
- MITRE: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-7855 – RESERVED
- NVD: https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2016-7855 – CVE ID Not Found
- Vulners: https://vulners.com/cve/CVE-2016-7855 – Also not found, because it takes data from NVD and MITRE. However, if you just search for object, which has links to this CVE: https://vulners.com/search?query=cvelist:”CVE-2016-7855″, you will find 38 objects that already use this id.
Upd. November 2 – appeared description at at NVD and Vulners. Mitre is still “reserved”
And the only source that has normal description and CVSS vector for this CVE is IBM xforce: https://exchange.xforce.ibmcloud.com/new
If you search for “CVE-2016-7855” you will get a great Vulnerability Report:
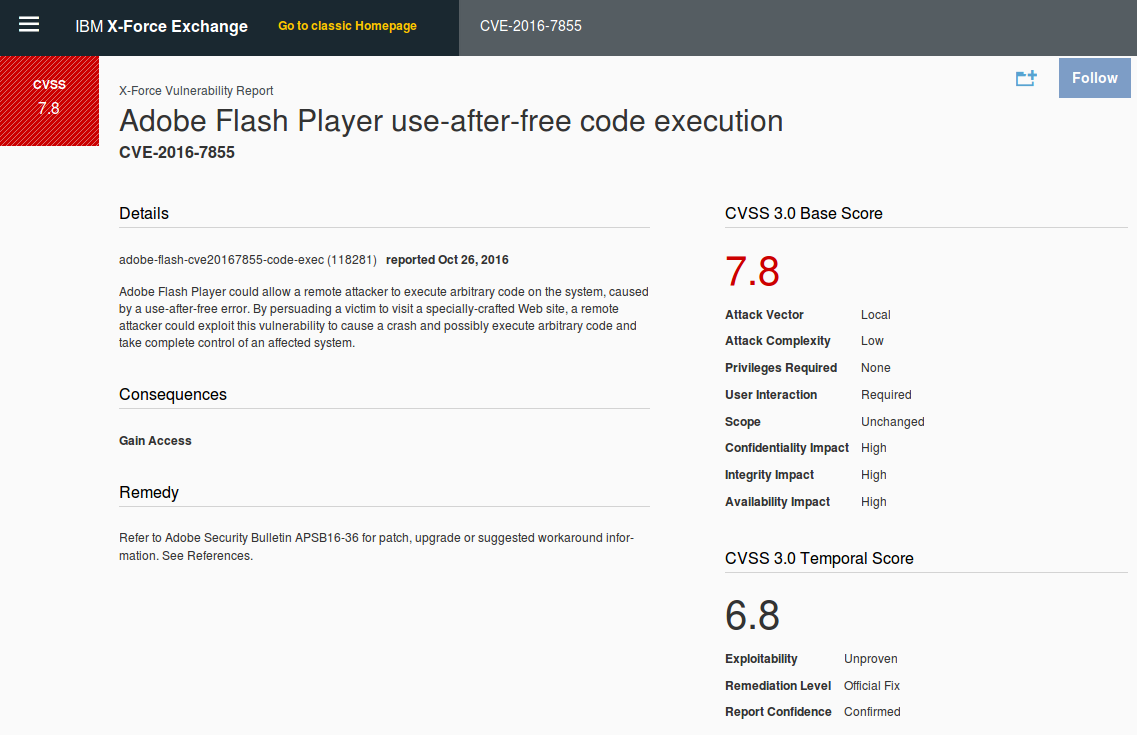
Why this happens? I suppose that the problem is CNA (CVE Numbering Authorities) program. Adobe Systems Incorporated is one of the participants. CNA don’t need to get CVE ID from Mitre for every issue, it already has some reserved:
The following series of communications occur between CNAs to MITRE:
(1) The CNA requests a pool of CVE IDs.
(2) The CNA announces the publication of a new CVE ID, which allows MITRE to update the CVE ID information on the CVE website.
(3) The CNA may need to consult with MITRE regarding CVE content decisions.
(4) The CNA notifies MITRE of suspected abuses of the CVE process by researchers.
(5) The CNA notifies MITRE and other parties when duplicate CVE IDs are detected.
Well, that seems, that step 2 may take long-long time. Maybe CNA is not really interested to make it fast. Or maybe Mitre don’t react efficiently. I don’t know. But I just see that CVE becoming a set of IDs and not a vulnerability base.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Divination with Vulnerability Database | Alexander V. Leonov
Pingback: Vulners Subsriptions and Apache Struts RCE | Alexander V. Leonov
Pingback: Kenna Security: Analyzing Vulnerability Scan data | Alexander V. Leonov