Qualys Security Conference Virtual 2018. New Agents, Patch Management and Free Services. Today I attended a very interesting online event – Qualys Security Conference Virtual 2018. It consisted of 11 webinars, began at 18:00 and will end at 03:45 Moscow time. Not the most convenient timing for Russia, but it was worth it. 🙂
Last time I was at offline QSC event in 2016, so for me it was especially interesting to learn about the new features of Qualys platform.
New Cloud Agents and Modes
As usual, Qualys payed much attention to their Cloud Agents. This year, 2 new agents were announced:
- Container (Docker) Agent
- Passive Agent
Container Agent will be used in the Container Security service with the following capabilities:
- CI/CD pipeline Integration with Jenkins
- Assess Images
- Monitor running containers
- Track drift of containers from images
- Fully Integrated on Qualys Platform
Passive Agent will be obviously an analogue of Tenable Nessus Network Monitor. And it will be used in Passive Network Discovery module with following features:
- Passively sniff on network
- Real-time device discovery & identification
- Identification of APT network traffic
- Extract malware files from network for analysis
In addition, Qualys now have new Mobile Security Platform through acquisition of 1Mobility. So, there will be Cloud Agents on iOS, Android & Windows Mobile.
By the way, interesting fact is that AWS policy prohibits the scanning of nano, micro and small instances. So Cloud Agent is the only way to get the data from these assets.
Service Releases
Here is the schedule of 2017-2018 Qualys releases:
Secure Config Assessment – Released – Q3’17
File Integrity Monitoring – Released – Q4’17
Indication of Compromise – Released – Q4’17
CertView – Released – Q2’18
CloudView Cloud Security – Released – Q2’18
Container Security – Released – Q2’18
Patch Management – Beta – Q3’18
Passive Network Discovery – Beta – Q3’18
Network Access Control – Beta – Q4’18
Secure Enterprise Mobility – Preview – Q4’18
Of course, I was most interested in Patch Management. In fact, detecting a vulnerability is only half the battle. It is much more important to ensure that this vulnerability will be patched. And you often have to be very flexible to motivate the IT staff to do it.
What if the VM solution will also patch the systems as well? This is a real game changer.
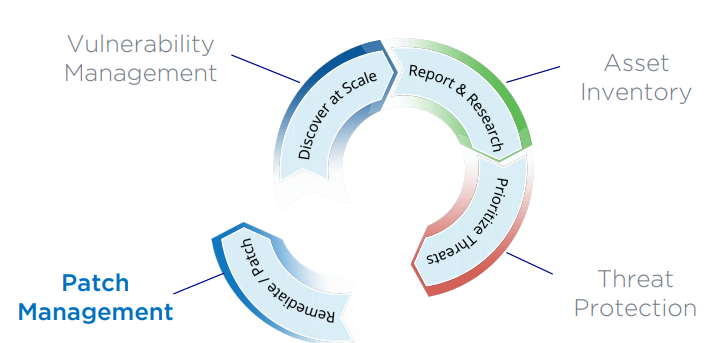
Qualys decided to follow this path. And it looks like they will be the first among big VM vendors who present this functionality. So far only it will patch only Windows system and 55 most popular third-party software products. Patching will be implemented by the same Cloud Agents. Patches will be downloaded from the Qualys servers. For Linux systems, packages will be taken from the internal repositories.
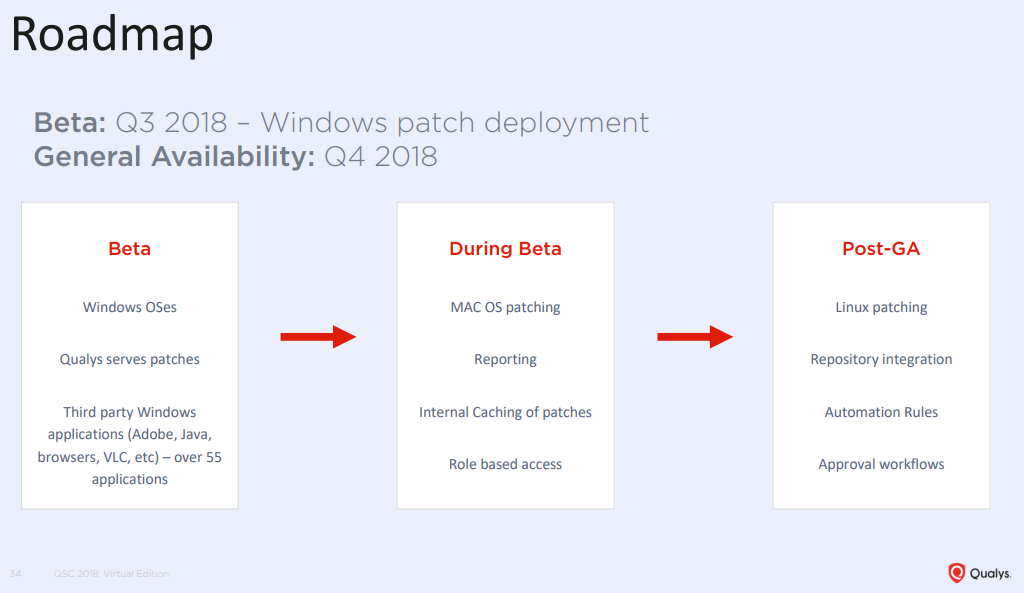
Patch Management dashboard:
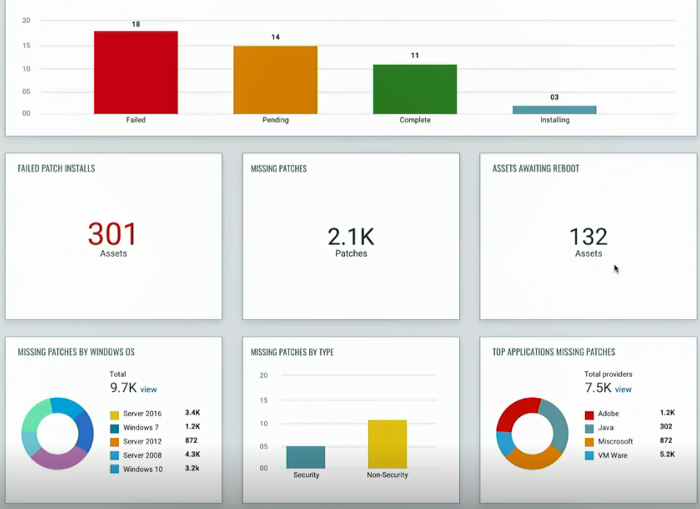
Аn interface where you can approve patches and start deployment jobs:
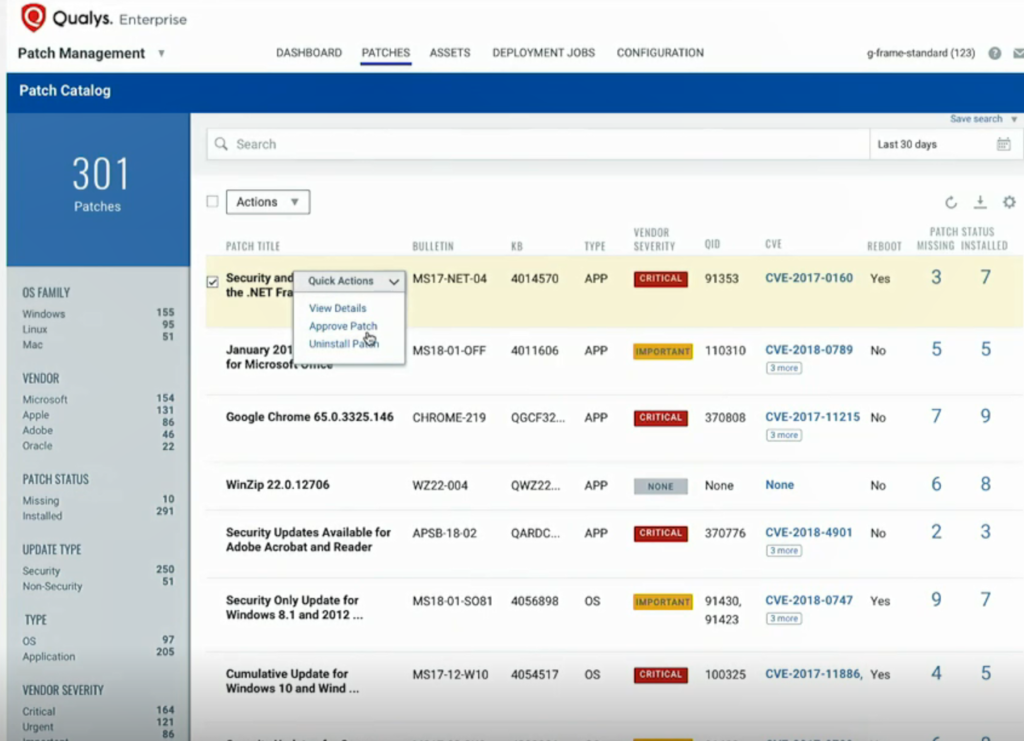
And here is Patch Management statistics for some group of hosts:
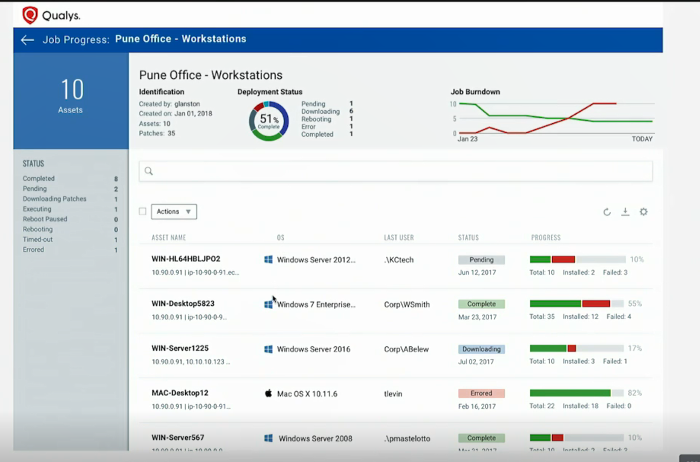
They are going to make rules for automated approval of the patches and support of the different roles, so this task of approval could be done by your IT team.
Talking about the modules, it will also be interesting to look at Passive Network Discovery as well.
Vulnerability Detection and Prioritization
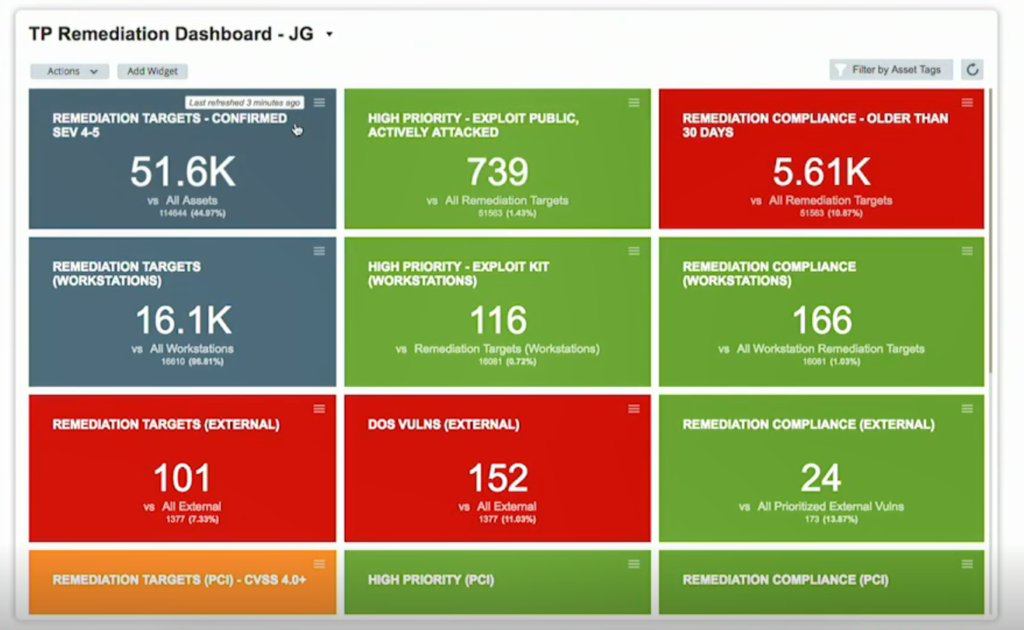
Once again, I can admire the great dashboards in Threat Protection! The groups seem very useful.
In the part of Vulnerability Detection, a very interesting feature was announced. It will allow you to add your own detectives for vulnerabilities. I like it! 🙂
Qualys Remote Detection Interface (QRDI)
Provides “custom” vulnerability detections for unauthenticated remote scans
Phase 1 – HTTP (Limited Release)
Phase 2 – HTTP Headers (May 2018)
Phase 3 – TCP packets (July 2018)
I highly recommend webinar “Vulnerability Risk Management” by Jimmy Graham. He not only talked about the Qualys products, but also about good practices in Vulnerability Management . So, even if you are not a Qualys customer, it might be useful. He also described in great detail WannaCry patching case, which I also used in my report “PHDays8: Digital Bet and thousands tons of verbal ore“. I am very glad that we had the similar interpretations.
Free Services
It’s great that Qualys is working on some free services as well. This time they presented a solution for monitoring Clouds Assets and SSL certificates across your infrastructure (obviously based on famous Qualys SSL Labs).

They also promise some new and free “Qualys Community Edition”, but it’s still unclear what it will be:

Fun
As a demonstration of API, Qualys introduced a very cute voice controlled chat bot .
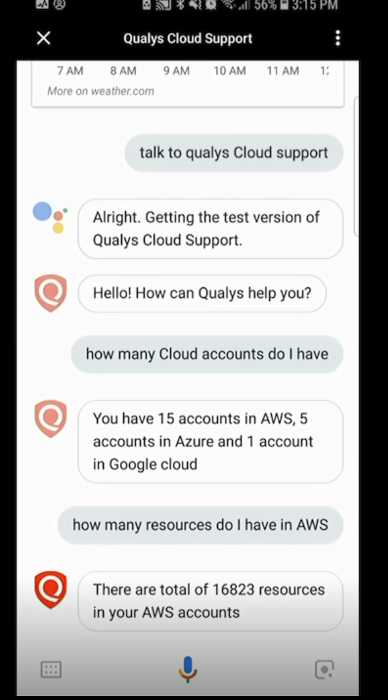
In conclusion
Virtual conference is a interesting format. It is as informative as traditional QSC and you do not need to go anywhere. And all slides and video recordings are immediately available. But on the other hand, there is a lack of communication.
As usual, Qualys has great interfaces, everything is beautiful and intuitive. On the other hand, the functionality is divided into many services/modules, so it can be confusing. But for Qualys it is obviously easier to develop and sell modules this way.
If you do not want to spent too much time Vulnerability Management, you have a good budget and you want to see all the functionality available in one web interface, Qualys might be the best choice for you. It will be especially interesting when their Patch Management module will be finished.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Well, I still think “automated patching” is just a fancy useless toy. Either you have proper remediation process with patch testing or you don’t, and nothing would really change with that.
For me the patching tool should be separate from the assessment tool. How often have wee seen in SCCM a patch applied only for a scanner to find it hasn’t been done properly. Using the same technology to patch and scan will lose this.
I am interested in the Qualys Community Edition – hopefully it will be a Nessus Professional killer providing the features Tenable removed from version 7. Qualys have a real opportunity here.