What’s new in Nessus 8. Today Tenable released a new version of their famous vulnerability scanner – Nessus 8. The existing scanner nodes don’t see the updates yet, but the installation binaries are already available. So you may try to install it.
This major release will be way more positive than the previous one. Of course Tenable did NOT return the multi-user mode and API in Nessus Professional. But on the other hand, they did NOT cut the functionality even further. They even added new features in GUI. And, what is the most important, they did NOT switch to the assets-based licensing (at least yet). 🙂
Installation
I didn’t want to wait until my Nessus server will offer me to update it, so I decided to re-install Nessus from the existing Nessus 8 rpm package.
Copying package file to the remote host:
# scp ~/Downloads/Nessus-8.0.0-es7.x86_64.rpm user@nessus.corporation.com:~/
Deleting existing package file and installing a new one:
# rpm -e Nessus-7.1.2-es7.x86_64
# rpm -ivh Nessus-8.0.0-es7.x86_64.rpm
warning: Nessus-8.0.0-es7.x86_64.rpm: Header V4 RSA/SHA1 Signature, key ID 1c0c4a5d: NOKEY
Preparing... ################################# [100%]
Updating / installing...
1:Nessus-8.0.0-es7 ################################# [100%]
Unpacking Nessus Core Components...
- You can start Nessus by typing /bin/systemctl start nessusd.service
- Then go to https://nessus.corporation.com:8834/ to configure your scanner
# /bin/systemctl start nessusd.serviceI didn’t need to input my license or change my password. The update/reinstallation process works great.
Live Results
The main new feature is Live Results: vulnerability scanning without actual scanning. The idea is to split the data collection and the actual assessment. In this case it will be possible to figure out what new vulnerabilities have appeared on our assets after the update of the knowledge base. In fact, if we already know information about the hosts (including software versions) in the Knowledge Base (KB) from the last scan, why not to reuse this data?
It’s not very hard from the technical point of view. Of course, Tenable most likely needed to change the process of plugin execution significantly and change the plugins itself. But for me it was not clear how Tenable will introduce this functionality in GUI. Because in existing Nessus Professional paradigm, there are no assets, dashboards. Only independent scans. How will they differentiate Live Results and actual results in this case?
In fact, they did it easily. They did not changed the concept of individual scans, they just added a new check in the scan task:
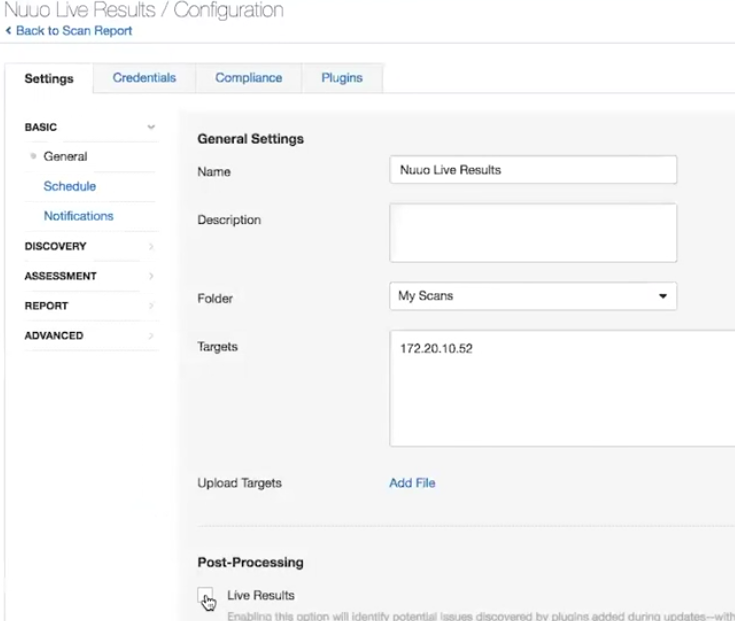
This and other images I’ve got from the product demonstration video at “Nessus at 20: Why It’s More Than a Product to Me“.
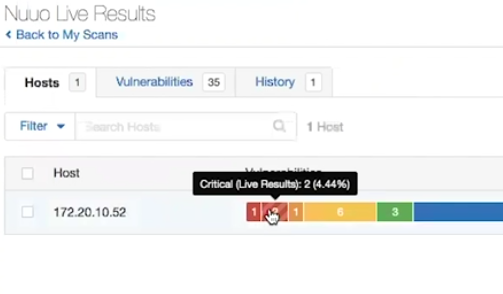
When it is enabled, they show additional vulnerabilities in the results painted striped like a candy:
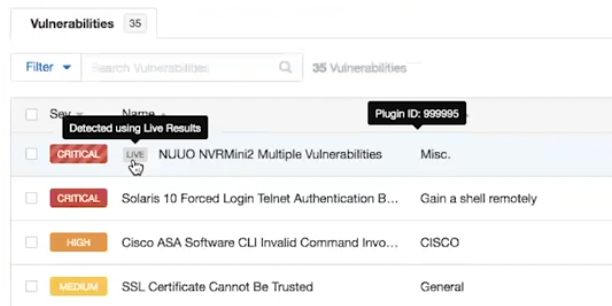
And the same in the list of vulnerabilities:
Vulnerability Snoozing/Inboxing and Vulnerability Grouping
This is a new way of seeing vulnerabilities in the Scan Results. It can be activated if you press on a gear here:
If you choose Grouping, the vulnerabilities will be grouped by Plugin Family.
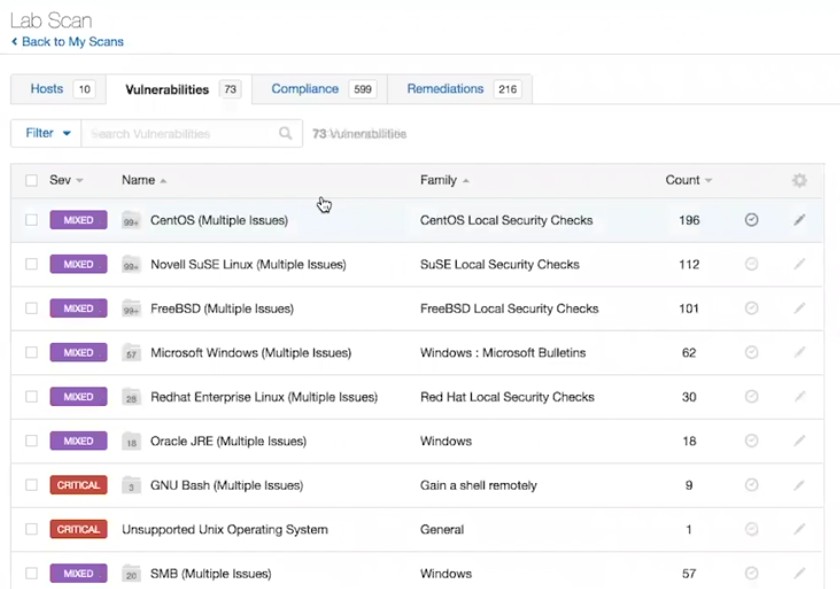
Well, sometimes it might me more informative if you can see what types of vulnerabilities are the most critical.
It is something similar with Snoozing. You can hide some vulnerabilities that you want to see in the results for some time and if you press on a gear you can actually see this hidden vulnerabilities.
I can’t say that it is something shockingly good and I was waiting this for a long time. Basically because I am more oriented on processing raw Nessus data. But it’s great that Tenable added these options. And it might be quite useful for those who works with Nessus GUI a lot.
Local Log Extraction
Now it will be possible to get Nessus logs from GUI. This is also quite useful feature. It’s not really convenient to go to the Nessus server by ssh, each time you need to retrieve scan logs ( see “Dealing with Nessus logs“). But it would be great if Tenable will make these logs more informative as well. 😉
So, that’s it. In all other aspects Nessus 8 seems pretty much like Nessus 7.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Adding custom NASL plugins to Tenable Nessus | Alexander V. Leonov