Microsoft Patch Tuesday June 2020: The Bleeding Ghost of SMB. This time, Microsoft addressed 129 vulnerabilities: 11 critical and 118 important. In fact, in the file that I exported from the Microsoft website, I saw 2 more CVEs (CVE-2020-1221, CVE-2020-1328) related to Microsoft Dynamics 365 (on-premises). But there is no information on them on the Microsoft website, in the MITRE CVE database and NVD. Does this mean that these CVE ids were mentioned unintentionally and related to some critical issues? I don’t think so, but this is strange.
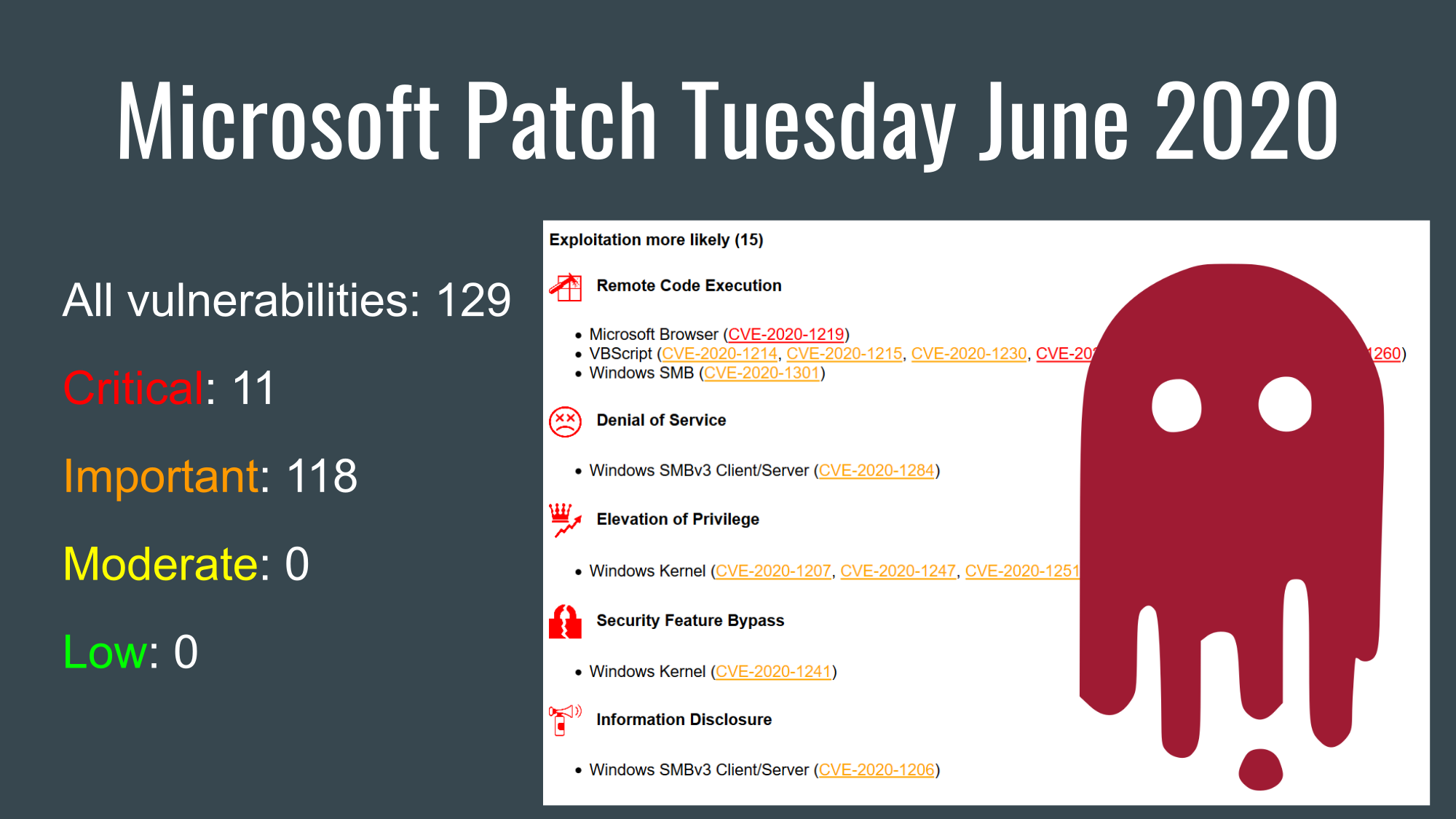
This time there were no vulnerabilities with detected exploitation, so let’s start with the group “Exploitation more likely” according to Microsoft.
Exploitation more likely (15)
 Remote Code Execution
Remote Code Execution
- Microsoft Browser (CVE-2020-1219)
- VBScript (CVE-2020-1214, CVE-2020-1215, CVE-2020-1230, CVE-2020-1213, CVE-2020-1216, CVE-2020-1260)
- Windows SMB (CVE-2020-1301)
 Denial of Service
Denial of Service
- Windows SMBv3 Client/Server (CVE-2020-1284)
 Elevation of Privilege
Elevation of Privilege
- Windows Kernel (CVE-2020-1207, CVE-2020-1247, CVE-2020-1251, CVE-2020-1253)
 Security Feature Bypass
Security Feature Bypass
- Windows Kernel (CVE-2020-1241)
 Information Disclosure
Information Disclosure
- Windows SMBv3 Client/Server (CVE-2020-1206)
I think the SMB vulnerabilities should be addressed first.
- Remote Code Execution in SMBv1 (CVE-2020-1301) protocol is called “SMBLost”. The attacker should send a specially crafted packet to the target SMBv1 server. But unlike the famous EternalBlue, the attacker have to be authenticated and there should be a shared partition on the server (e.g. “c:\” or “d:\”), so it should be much less harmful. Anyway, if SMBv1 is not a mission critical component of your infrastructure, disable it!
- Denial of Service in SMBv3 Client or Server (CVE-2020-1284). An authenticated attacker have to send a specially crafted packet to a vulnerable SMB server or host a maliciously configured SMBv3 server and convince the client to connect to it. The vulnerability exists in Windows 10 Version 2004 and Windows Server, version 2004 (Server Core installation).
- The most interesting SMB vulnerability is Information Disclosure in SMBv3 Client/Server (CVE-2020-1206). It is called “SMBleed”. And what makes it interesting is that the company, that discovered this vulnerability, ZecOps, released a PoC that combines SMBleed exploitation with the exploitation of March SMBGhost (CVE-2020-0796) vulnerability to gain unauthenticated RCE! (write up , PoC) And it seems much more reliable than the code that was published earlier (for example, PoC by chompie1337). This means that we are one step closer to real attacks that will exploit this vulnerability.
Of course, you can say that SMBleed, SMBGhost and this new DoS vulnerability (CVE-2020-1284) affect only different versions of Windows 10 and Windows Server Core installations 1903, 1909, 2004. These Windows Server versions are pretty rare for a corporate environments and vulnerable desktops are not such a big problem. Well, yes, but can you guarantee that you do not have virtual machines with Windows 10 that are used as servers? You can only guarantee this with a good IT inventory process!
What about other “Exploitation more likely” vulnerabilities? Well of course it’s worth mentioning RCEs in Microsoft browsers (CVE-2020-1219): Internet Explorer 11 and Microsoft Edge. Also a lot of RCEs in VBScript (CVE-2020-1214, CVE-2020-1215, CVE-2020-1230, CVE-2020-1213, CVE-2020-1216, CVE-2020-1260). So, keep your web browser up-to-date and try not to click on suspicious links.
Other Product based (36)
Microsoft SharePoint
 Remote Code Execution (CVE-2020-1181)
Remote Code Execution (CVE-2020-1181) Elevation of Privilege (CVE-2020-1178, CVE-2020-1295)
Elevation of Privilege (CVE-2020-1178, CVE-2020-1295) Cross Site Scripting (CVE-2020-1177, CVE-2020-1183, CVE-2020-1297, CVE-2020-1298, CVE-2020-1318, CVE-2020-1320)
Cross Site Scripting (CVE-2020-1177, CVE-2020-1183, CVE-2020-1297, CVE-2020-1298, CVE-2020-1318, CVE-2020-1320) Spoofing (CVE-2020-1148, CVE-2020-1289)
Spoofing (CVE-2020-1148, CVE-2020-1289) Open Redirect (CVE-2020-1323)
Open Redirect (CVE-2020-1323)
Windows Kernel
 Elevation of Privilege (CVE-2020-0986, CVE-2020-1237, CVE-2020-1246, CVE-2020-1262, CVE-2020-1264, CVE-2020-1266, CVE-2020-1269, CVE-2020-1273, CVE-2020-1274, CVE-2020-1275, CVE-2020-1276, CVE-2020-1307, CVE-2020-1310, CVE-2020-1316)
Elevation of Privilege (CVE-2020-0986, CVE-2020-1237, CVE-2020-1246, CVE-2020-1262, CVE-2020-1264, CVE-2020-1266, CVE-2020-1269, CVE-2020-1273, CVE-2020-1274, CVE-2020-1275, CVE-2020-1276, CVE-2020-1307, CVE-2020-1310, CVE-2020-1316) Information Disclosure (CVE-2020-1290)
Information Disclosure (CVE-2020-1290)
Windows Runtime
 Elevation of Privilege (CVE-2020-1231, CVE-2020-1233, CVE-2020-1235, CVE-2020-1265, CVE-2020-1282, CVE-2020-1304, CVE-2020-1306, CVE-2020-1334)
Elevation of Privilege (CVE-2020-1231, CVE-2020-1233, CVE-2020-1235, CVE-2020-1265, CVE-2020-1282, CVE-2020-1304, CVE-2020-1306, CVE-2020-1334) Information Disclosure (CVE-2020-1217)
Information Disclosure (CVE-2020-1217)
Among the products with the biggest number of vulnerabilities, we can once again highlight Microsoft SharePoint, and especially Remote Code Execution (CVE-2020-1181). “An authenticated attacker can execute code as the application’s pool process”. Other vulnerabilities are the Elevation of Privilege and Information Disclosure in Windows Kernel and Windows Runtime.
Other Vulnerability Type based (78)
 Remote Code Execution
Remote Code Execution
- Chakra Scripting Engine (CVE-2020-1073)
- GDI+ (CVE-2020-1248)
- Jet Database Engine (CVE-2020-1208, CVE-2020-1236)
- LNK (CVE-2020-1299)
- Microsoft Excel (CVE-2020-1225, CVE-2020-1226)
- Microsoft Office (CVE-2020-1321)
- Windows (CVE-2020-1300)
- Windows OLE (CVE-2020-1281)
- Windows Shell (CVE-2020-1286)
- Word for Android (CVE-2020-1223)
 Denial of Service
Denial of Service
- Connected User Experiences and Telemetry Service (CVE-2020-1120, CVE-2020-1244)
- Windows (CVE-2020-1283)
- Windows Registry (CVE-2020-1194)
 Memory Corruption
Memory Corruption
- Media Foundation (CVE-2020-1238, CVE-2020-1239)
 Elevation of Privilege
Elevation of Privilege
- Component Object Model (CVE-2020-1311)
- Connected Devices Platform Service (CVE-2020-1211)
- Diagnostic Hub Standard Collector (CVE-2020-1202, CVE-2020-1203)
- Diagnostics Hub Standard Collector (CVE-2020-1257, CVE-2020-1278, CVE-2020-1293)
- DirectX (CVE-2020-1258)
- Group Policy (CVE-2020-1317)
- Microsoft Store Runtime (CVE-2020-1222, CVE-2020-1309)
- Microsoft Windows Defender (CVE-2020-1163, CVE-2020-1170)
- OLE Automation (CVE-2020-1212)
- OpenSSH for Windows (CVE-2020-1292)
- Windows (CVE-2020-1162, CVE-2020-1324)
- Windows Background Intelligent Transfer Service (CVE-2020-1255)
- Windows Backup Service (CVE-2020-1271)
- Windows Bluetooth Service (CVE-2020-1280)
- Windows Error Reporting (CVE-2020-1234)
- Windows Error Reporting Manager (CVE-2020-1197)
- Windows Feedback Hub (CVE-2020-1199)
- Windows GDI (CVE-2020-0915, CVE-2020-0916)
- Windows Installer (CVE-2020-1272, CVE-2020-1277, CVE-2020-1302, CVE-2020-1312)
- Windows Lockscreen (CVE-2020-1279)
- Windows Mobile Device Management Diagnostics (CVE-2020-1204)
- Windows Modules Installer Service (CVE-2020-1254)
- Windows Network Connections Service (CVE-2020-1291)
- Windows Network List Service (CVE-2020-1209)
- Windows Now Playing Session Manager (CVE-2020-1201)
- Windows Print Configuration (CVE-2020-1196)
- Windows State Repository Service (CVE-2020-1305)
- Windows Text Service Framework (CVE-2020-1314)
- Windows Update Orchestrator Service (CVE-2020-1313)
- Windows WLAN Service (CVE-2020-1270)
- Windows WalletService (CVE-2020-1287, CVE-2020-1294)
 Security Feature Bypass
Security Feature Bypass
- Microsoft Outlook (CVE-2020-1229)
- Windows Host Guardian Service (CVE-2020-1259)
 Information Disclosure
Information Disclosure
- Internet Explorer (CVE-2020-1315)
- Media Foundation (CVE-2020-1232)
- Microsoft Edge (CVE-2020-1242)
- Microsoft Graphics Component (CVE-2020-1160)
- Microsoft Project (CVE-2020-1322)
- Visual Studio Code Live Share (CVE-2020-1343)
- Windows Diagnostics & feedback (CVE-2020-1296)
- Windows Error Reporting (CVE-2020-1261, CVE-2020-1263)
- Windows GDI (CVE-2020-1348)
- Windows Service (CVE-2020-1268)
 Spoofing
Spoofing
- Microsoft Bing Search (CVE-2020-1329)
- Microsoft Edge (Chromium-based) in IE Mode (CVE-2020-1220)
- NuGetGallery (CVE-2020-1340)
- System Center Operations Manager (CVE-2020-1331)
 Code Injection
Code Injection
- Azure DevOps Server (CVE-2020-1327)
Among other vulnerabilities, the most important are the various RCEs.
- 2 RCE in Microsoft Excel (CVE-2020-1225, CVE-2020-1226). This might be interesting for phishing.
- Yet another RCE in LNK file processing (CVE-2020-1299). This is the third this year.
- RCE in Windows CAB files processing (CVE-2020-1300). Quote from zdi: the attackers “could also spoof a network printer and dupe a user into installing the specially crafted CAB file disguised as a printer driver. Users are often conditioned into trusting printer drivers when offered one, so it would not be surprising to see this get exploited”.
- VM vendors also pay attention to RCE in Chakra Scripting Engine (CVE-2020-1073), GDI+ (CVE-2020-1248), Jet Database Engine (CVE-2020-1208, CVE-2020-1236), Windows OLE (CVE-2020-1281) and Windows Shell (CVE-2020-1286).
What else besides RCEs?
- Nice Denial of Service in Windows Registry, but “an attacker would need access to the system in order to launch a crafted application to exploit this flaw.”
- A lot of Elevation of Privilege, but VM vendors highlight only vulnerabilities in OpenSSH for Windows (CVE-2020-1292) and Windows GDI (CVE-2020-0915, CVE-2020-0916).
- Security Feature Bypass in Microsoft Outlook (CVE-2020-1229). It may “allow attackers to automatically load remote images – even from within the Preview Pane” and may be used with GDI+ RCE.
- Among Information Disclosure vulnerabilities, ZDI highlights vulnerabilities in Microsoft Edge (CVE-2020-1242) and in Windows Diagnostics & feedback (CVE-2020-1296).
In conclusion
It’s rather interesting month, but the focus is still mainly on SMB RCE vulnerabilities and the possible use of these vulnerabilities in malware attacks.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.
