This episode is based on posts from my Telegram channel avleonovcom, published in the last 2 weeks. So, if you use Telegram, please subscribe. I update it frequently.

Barapass update
I recently released an update to my password manager barapass. BTW, it seems to be my only pet project at the MVP stage, which I use every day.
What’s new:
- Now I am sure that it works on Windows 10 without WSL. And you can run it beautifully even with the icon. ? Read more about installation in Windows in this file.
- Not only “copy the next value to the clipboard” (or “revolver mode” ) is now possible in the search results section. You can also get the previous value or copy the same value one again if it was somehow erased in the clipboard. Previously, I had to retype the search request each time to do this, and it was quite annoying. By the way, I unexpectedly discovered that the user input history inside the application magically works in the Windows shell (using up and down arrows) without any additional coding. On Linux it does not.
- You can set a startup command, for example, to decrypt the container.
- The startup command and quick (favorite) commands are now in settings.json and not hard-coded.
- settings.json, container files and decrypted files are now in “files” directory. It became more convenient to update barapass, just change the scripts in the root directory and that’s it. I divided the scripts into several files, now it should be more clear how it works.
So, if you need a minimalistic console password manager in which you can easily use any encryption you like – welcome! You can read more about barapass in my previous post.
Google Tsunami
Have you heard about this new open source Tsunami vulnerability scanner released by Google (github)? What do you think about it? Is it the real thing or just another useless automation layer over nmap? I am now more for the second option. And I’m pretty skeptical that they will make effective and safe plugins for exploit-based vulnerability detection. The fact that this is 99.5% Java code doesn’t make me enthusiastic as well. But, of course, I want to believe that it will be new “kubernetes” in the Vulnerability Management area. Let’s discuss in @avleonovchat
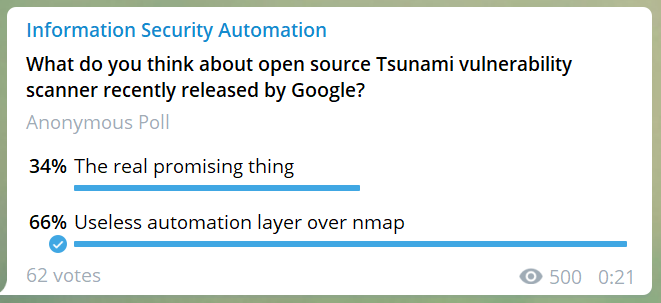
Vote here: https://t.me/avleonovcom/731
RCE in Windows DNS Server
Yep, yet another short post about SIGRed (video, MS CVE-2020-1350). Getting RCE with only a DNS request is really impressive. And it was there for 17 years! OMG, what attackers could do with this in corporate environment! Checkpoint guys stated that “Due to time constraints, we did not continue to pursue the exploitation of the bug (which includes chaining together all of the exploitation primitives), but we do believe that a determined attacker will be able to exploit it.”
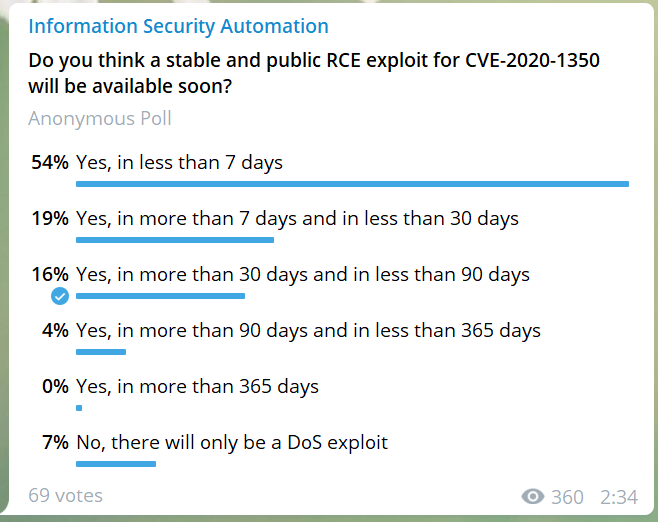
Vote here: https://t.me/avleonovcom/733
SAP RECON
If your organization uses SAP (my condolences), you should initiate some patching right now and make sure this stuff is NOT available on your network perimeter. There is already an exploit available for these vulnerabilities:
CVE-2020-6287 – unauthenticated attacker can “execute configuration tasks to perform critical actions against the SAP Java system, including the ability to create an administrative user”
CVE-2020-6286 – unauthenticated attacker can make Path Traversal
I also found a funny bug: Nessus has a remote plugin to detect these vulnerabilities, but you were not be able to find it on Tenable website by “CVE-2020-6287” in CVE filter. Why? When they edited CVE list in plugin, they have put “CVE-2020-6286” there twice.
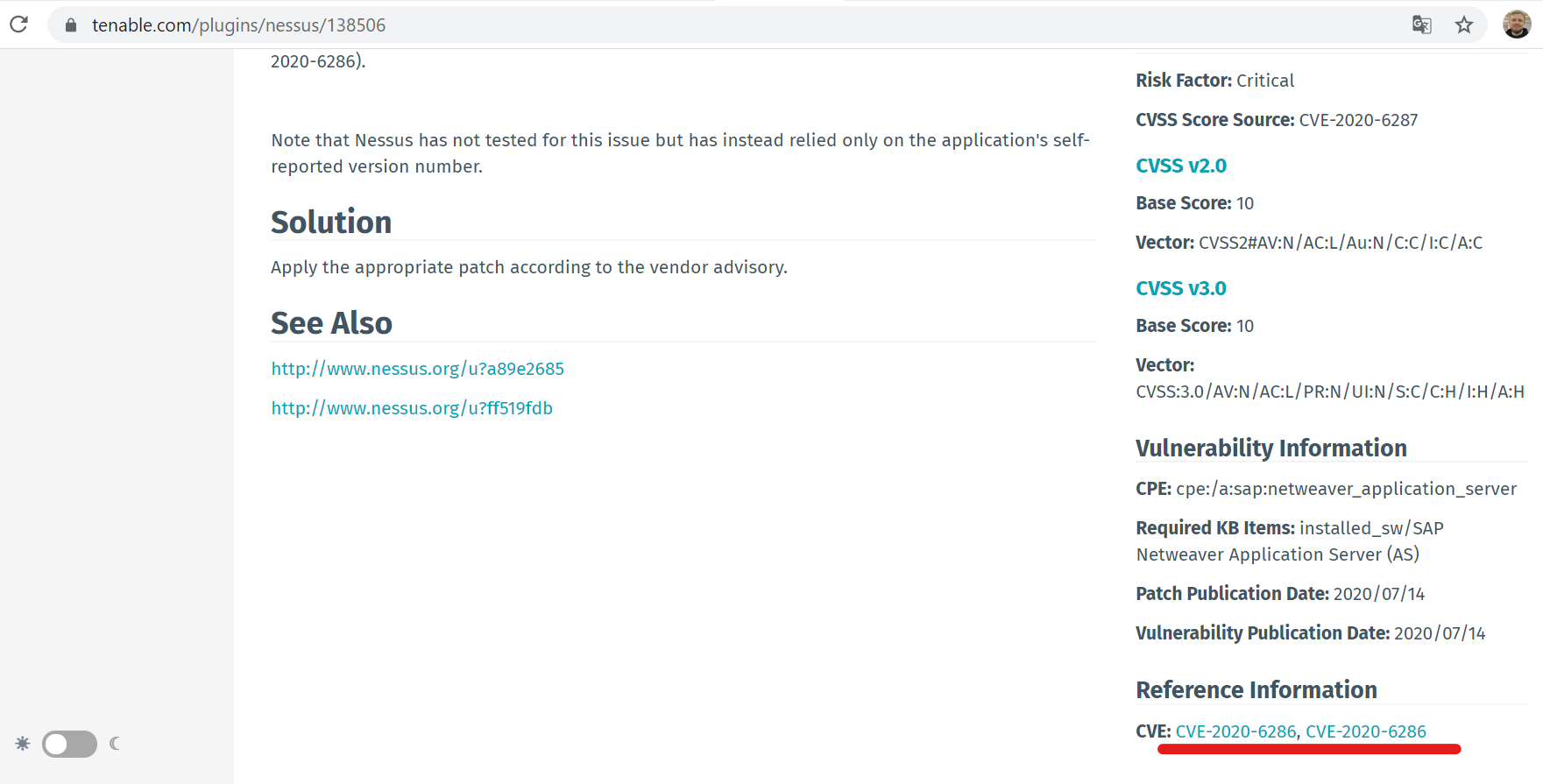
??♂️ Sometimes such things happen.
Weird attack on Twitter
A little bit about Twitter? Of course, the last incident puzzled me a lot. Let’s say you have an access to the Twitter accounts of Bill Gates, Elon Musk, Obama, Apple and others, and you post a silly Bitcoin scam? Whaat? ?
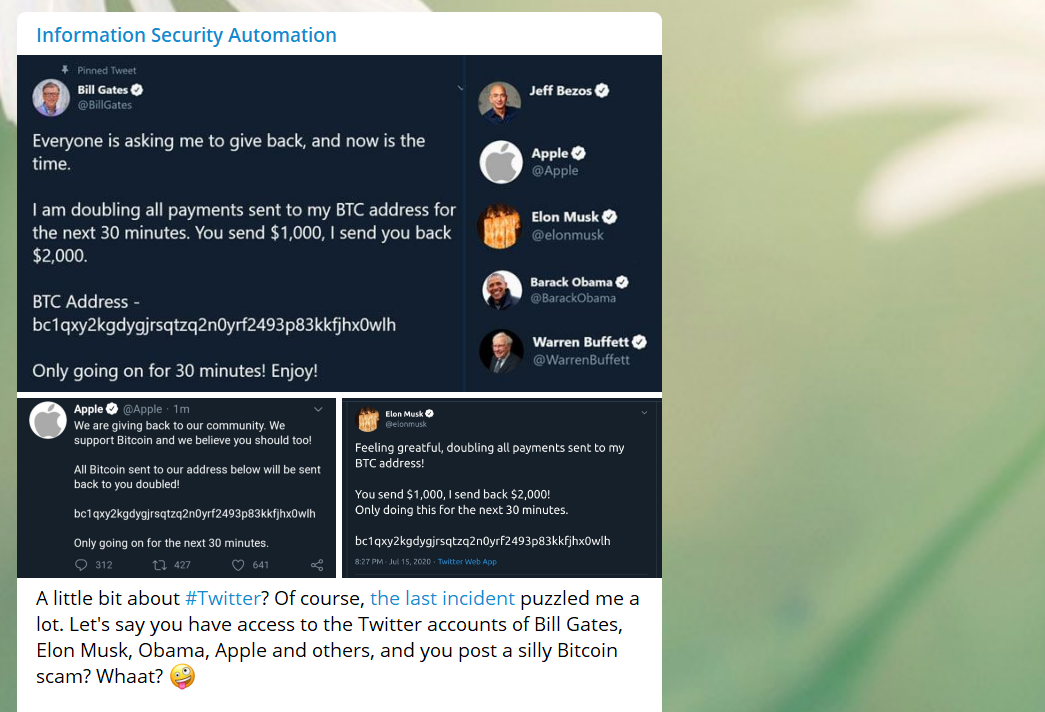
I recently had some practice in writing email templates for antiphishing trainings (btw, my video about antiphishing) and was amazed what results can be achieved with regular email messages if you add a little bit of imagination and choose the right time. Even IT security professionals open files and urls, input credentials on fake sites, etc.!
It is absolutely clear that these attackers could have done something humongous. Starting from the massive gathering of user accounts / distribution of any malware through high-quality phishing websites and ending with advanced market manipulation. And instead of all this, some messages about bitcoins. It’s strange.
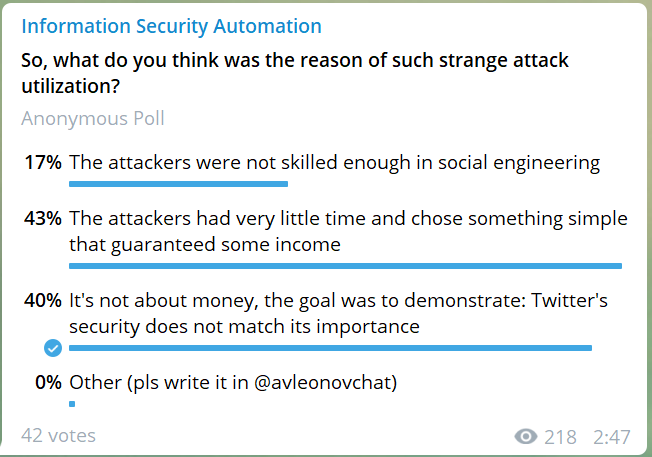
Vote here: https://t.me/avleonovcom/741

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Там в очередной раз то ли поломали, то ли не поломали LastPass | Александр В. Леонов