I decided to publish my simple console Password Manager. I called it barapass (github). I’ve been using It for quite some time in Linux and in Windows (in WSL). Probably it will also work natively in Windows and MacOS with minimal fixes, but I haven’t tried it yet.

Why do people use password managers?
Well, with password manager it’s possible to avoid remembering passwords and make them arbitrarily complex and long. And no one will be able to brute force them. Of course, you can simply store passwords in text files, but password managers are better than this because:
- no one will see your password over your shoulder;
- if an attacker gains access to the files on your host, it won’t possible to read your passwords from the encrypted file or storage (well, ideally);
- it’s easier to search for objects in the password manager and copy values from it.
I wanted something as simple as editing a text file with the key-value content. And I wanted it to be stored in a secure manner, and security could be easily checked, “simple and stupid”.
Why not use a ready-made password manager? (thousands of them)
IMHO, it’s very hard to control how password managers store the passwords and often very unpleasant vulnerabilities appear in them. I have everything in one small python file: a simple CLI, and functions for encryption/decryption. It’s only 200 lines.
Currently, barapass stores passwords encrypted using AES, but you can easily change it to any other cryptographic algorithm or a combination of them and use various methods to generate the keys. This customization can make it more secure in practical sense just because your passwords should be VERY interesting for the attacker to make this charades solving worth it. 🙂
How to run barapass?
You will need to install python3 with some additional modules:
pip3 install clipboard stdiomask pycryptodomeAnd also some tool to work with clipboard:
For CentOS/RHEL:
sudo yum install xclipFor Ubuntu/Debian:
sudo apt-get install xclipThen just run :
python3 barapass.py --interactiveHow to use barapass?
The scheme is following:
- Create a text file with key-value data
- Create an encrypted version of the file in barapass
- Use barapass to search for keys in the encrypted file and copy values to the clipboard
- If you need to edit the file, decrypt it in barapass, make changes and create a new encrypted version of the file
Something like this:
Encrypting and decrypting files
Barapass works with text files in this format:
$ cat testcred.txt
### My Email ###
MyEmail|URL|https://yandex.ru
MyEmail|account|my_email@yandex.ru
MyEmail|password|password1234
### My Server ###
MyServer|SSH_Command|ssh user@server.com
MyServer|SSH_Password|password1234
MyServer|DB_User|testuser
MyServer|DB_Password|testpass123You can encrypt testcred.txt in testcred.brp:
$ python3 barapass.py --interactive
Interactive mode (q for exit; fc for favorite commands)
Command >> encrypt testcred.txt testcred.brp
Container testcred.brp password >> ********
OK: Container testcred.brp was created successfully
Command >> qThis encrypted file looks like this:
{"profile": "Simple AES", "nonce": "zGIX48DdarHVWXbgYpoBWg==", "tag": "I+JR1hX6F/WuVxcjF/K2zQ==", "ciphertext": "9EIOPOTPZ1HvCGrxS7Uc8BQno2O75aX8khEut/sU9EvKFPFwsfofLqL38BTwPicddXiEvFXZdgu6aPg9Rlg44Oo099YhW1V3bS9HyvFPaiheeFat/goj+RynH8sC+Pz4OWFqtbgSPzS4YHdMB3cw2Od/gVFRf2UHVTz8wFuL6LqgGgz6BuehGQN9/snmUgMeXHyV65ZWsUCpCvFo4uIxTn4Evd5aIAvR048Wc8YHUxOYYKg4sD5K8dLcVQLtOjcUrJ4k1BVSbHq8QLzBCk720TzlwbhuaaLz7wWSvKj7ml3w8fI6vEQeBoKOH/3TK5q+xHkqDIdi8uT7/BDIYo9818CPSEiyOmoxGw=="}You can decrypt testcred.brp in clear text testcred2.txt like this:
$ python3 barapass.py --interactive
Interactive mode (q for exit; fc for favorite commands)
Command >> decrypt testcred.brp testcred2.txt
Container testcred.brp password >> ********
OK: Container testcred.brp was decrypted successfully
OK: Raw file testcred2.txt was created
Command >> q
$ cat testcred2.txt
### My Email ###
MyEmail|URL|https://yandex.ru
MyEmail|account|my_email@yandex.ru
MyEmail|password|password1234
### My Server ###
MyServer|SSH_Command|ssh user@server.com
MyServer|SSH_Password|password1234
MyServer|DB_User|testuser
MyServer|DB_Password|testpass123aSearching in encrypted file
To search in an encrypted file you should use encrypted file, enter the password and perform search request:
$ python3 barapass.py --interactive
Interactive mode (q for exit; fc for favorite commands)
Command >> use testcred.brp
Container testcred.brp password >> ********
OK: Container testcred.brp was decrypted successfully
OK: Container testcred.brp was loaded successfully
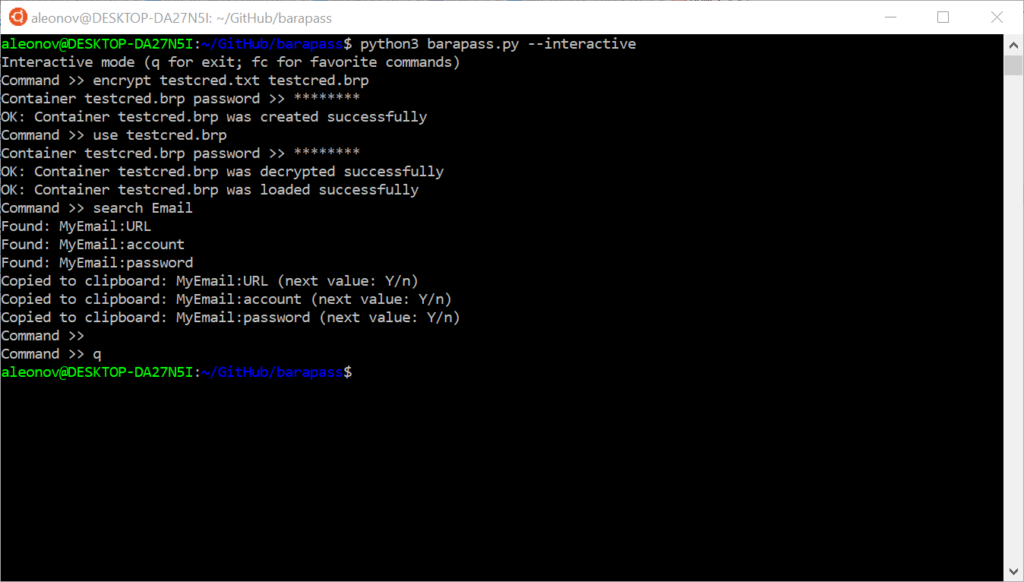
Command >> search Email
Found: MyEmail:URL
Found: MyEmail:account
Found: MyEmail:password
Copied to clipboard: MyEmail:URL (next value: Y/n)
Copied to clipboard: MyEmail:account (next value: Y/n)
Copied to clipboard: MyEmail:password (next value: Y/n)
Command >> qAll found results will be copied to the clipboard one by one, so that you can paste them where it is necessary.
Is it safe to copy passwords to clipboard?
Someone may say: what if the host is compromised and an attacker monitors the clipboard or searches for decrypted data in memory? Well, it’s possible. But the same attacker can also use keylogger or take screenshots. It’s hard to talk about secure authentication when the host is compromised. Anyway, it’s possible to store and retrieve passwords in more complex way, if necessary. 😉
In conclusion
If someone will use this or want to participate – welcome! In fact, I want to make CLI more user friendly with autocomplete and command history (with up and down arrow keys). I also think about some portable GUI for Linux, Windows and Android. So your help will be highly appreciated. 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Pingback: Barapass, Tsunami scanner, vulnerabilities in Windows DNS Server and SAP products, weird attack on Twitter | Alexander V. Leonov
Pingback: Там в очередной раз то ли поломали, то ли не поломали LastPass | Александр В. Леонов