Exploit accounting in Vulristics: bug and new component name.
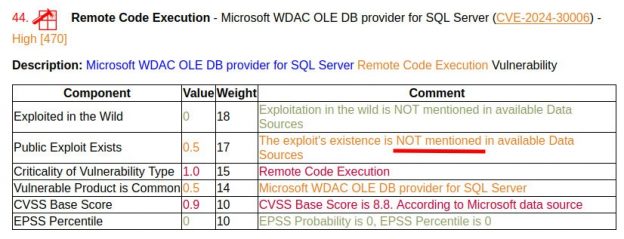
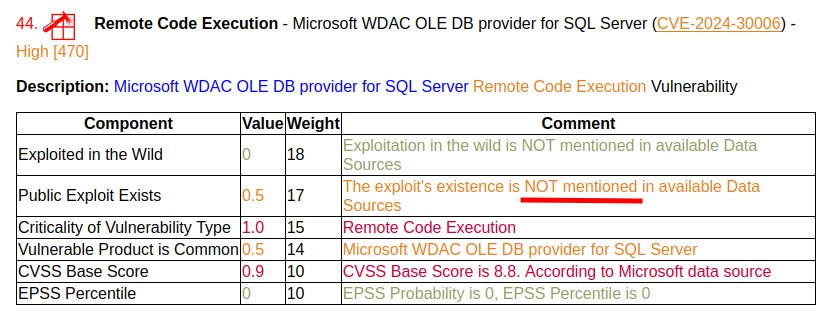
🔹 I discovered that sometime in April a bug was added to Vulristics: vulnerabilities without exploits received the value of the corresponding component 0.5, not 0. 🤦♂️ Somehow I didn’t pay attention to it and no one reported it to me. I corrected it with today’s commit. I’m going to regenerate the Microsoft Patch Tuesday and Linux Patch Wednesday reports for April and May. This, of course, is not a super-critical bug, but the final vulnerability score was distorted. If you use Vulristics, take note and update.
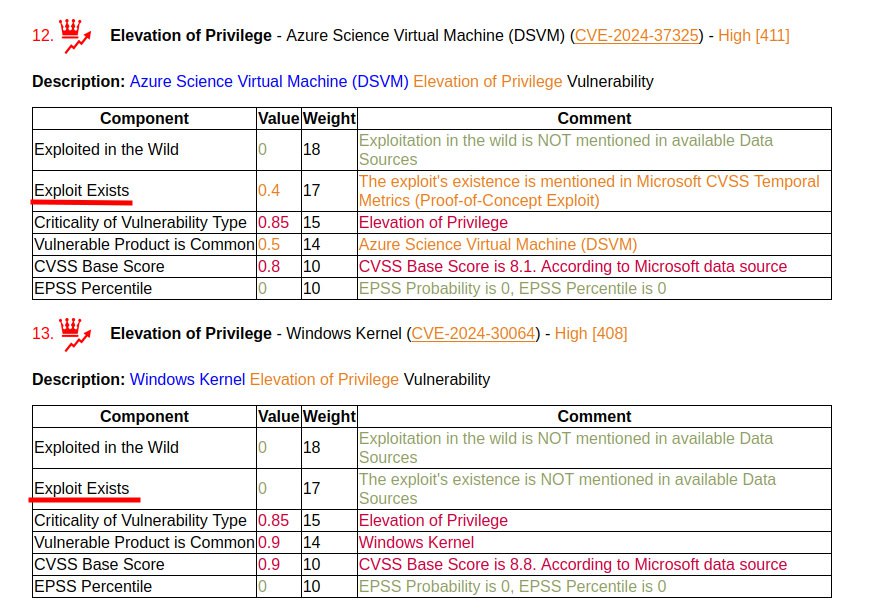
🔹 At the same time, I renamed the “Public Exploit Exists” component to the more logical “Exploit Exists”. It takes values:
1, if there is a public exploit (link or flag in the BDU)
0, if there is no exploit data at all
from 0 to 1, if there is data about a private exploit/PoC
🔹 I created a Changelog and added the “-v” or “–version” parameters. I have been running a project without versions since 2020. 😅🤷♂️