It looks like a pretty simple question. I used it to started my MIPT lecture. But actually the answer is not so obvious. There are lots of formal definitions of a vulnerability. For example in NIST Glossary there are 17 different definitions. The most popular one (used in 13 documents) is:
Vulnerability is a weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source
NISTIR 7435 The Common Vulnerability Scoring System (CVSS) and Its Applicability to Federal Agency Systems
But I prefer this one, it’s from the glossary as well:
Vulnerability is a bug, flaw, weakness, or exposure of an application, system, device, or service that could lead to a failure of confidentiality, integrity, or availability.
I think the best way to talk about vulnerabilities is to treat them as bugs and errors. Because people deal with such entities more often in a form of software freezes and BSODs. 😉
You probably heard a joke, that a bug can be presented as a feature if it is well-documented and the software developers don’t want to fix it.
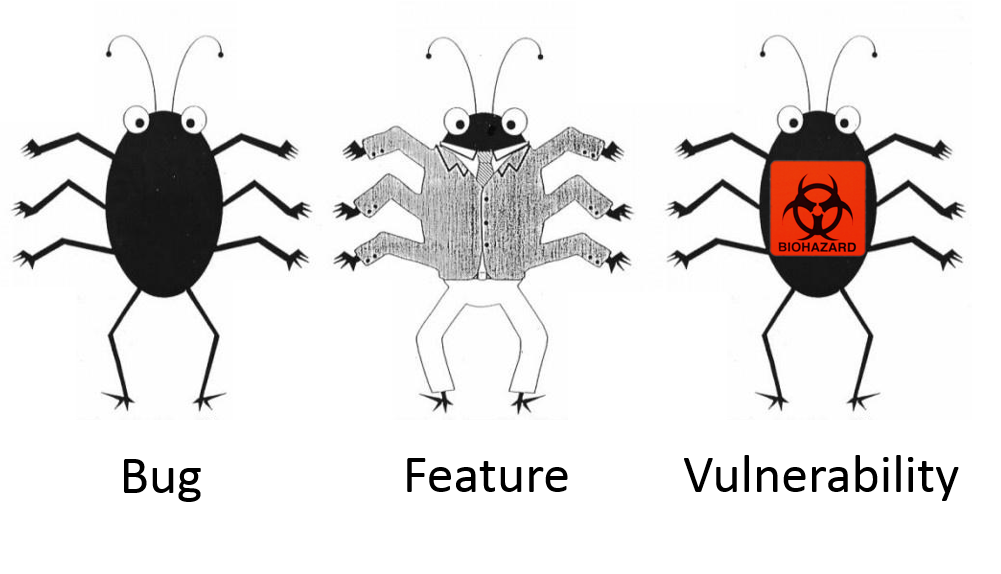
Vulnerability is also a specific bug that can lead to some security issues. Or at least it is declared.
Continue reading
