I think, most of financial and trade companies know about vulnerability scanning mainly because of PCI DSS. Vulnerability Assessment is, of course, an important issue, but when regular scanning is prescribed in some critical standard it become much more important for businesses.

This post will be about PCI ASV from the point of view of a scanning vendor. I decided to figure out what technical requirements exist for ASV solutions and how difficult/expensive it is to become an ASV.
Perimeter scanning
Basically, PCI ASV scan is a form of automated network perimeter control, performed by an external organization. All Internet-facing hosts of merchants and service providers should be checked 4 times a year (quarterly) with Vulnerability Scanner by PCI ASV (PCI DSS Requirement 11.2.2.). It is necessary to check the effectiveness of patch management and other security measures that improve protection against Internet attacks.
It is important that the ASV scanning is not a product, it’s a service of a PCI ASV security solution provider. Providers may use their own scanners or the software of third parties, including, for example, OpenVAS and other free security assessment tools. The main thing is that provider should show good results in practical scanning tests, during the PCI ASV evaluation process.
Some providers may give their customer web-interface access to the scanner to launch the scans. Some providers may hold quarterly scanning without any participation customer’s employee. Usually communication between ASV provider and the customer is minimized: customer lists the scan targets and makes sure that the scanner won’t be blocked by firewall. ASV provider sends scan report to the customer, customer then forwards it to the acquirer.
The ASV prepares scan reports according to the ASV Scan Report requirements and submits reports to the scan customer. The scan customer submits reports to their acquirers or payment brands as directed by the payment brands.
Stages of the ASV scanning process:
- Scoping
- Scanning
- Reporting/remediation
- Dispute Resolution
- Rescan (as needed)
- Final reporting
Some details of the process you can find in “Approved Scanning Vendors (ASVs) Program Guide” (38 pages, May 2013)
- Customer sets IP ranges and domains for scanning. ASV should “identify active IP addresses and services”, and then confirm the list of targets.
- ASV is “providing a determination as to whether the scan customer’s components have met the scanning requirement”. As I understand, if ASV have detected host that he doesn’t know how to scan, he must inform the customer.
- ASV must store the scan reports for 2 years.
- Customer must make sure that load balancers and firewalls won’t intercept ASV scanning.
Becoming PCI ASV
Ok, let’s say we want to become a new ASV. There is a special page on the PCI website.
Interesting things you can find there:
- Each year status should be re-approved.
- You should pass “remote test conducted on the PCI Security Standards Council’s test infrastructure”. You need to scan it, in other words.
- There will be vulnerabilities and misconfigurations in the PCI test infrastructure, which you will need to detect.
- There will be network hosts and Web applications in the PCI test infrastructure.
Technically it looks like we need some combination of unauthenticated network and WAS-scanner.
In addition to the scan ability PCI will also check the application form and the report forms (executive and detailed test reports). They will also emulate the processes of making application and scan result discussion by phone.
If you fail the test, you can try again. But you will have to pay a re-testing fee. After three unsuccessful attempts you may be sent on “waiting period”.
Ok, so far it sounds logical. But what particular systems provider will have have to scan during the ASV test? Required Components for PCI DSS Vulnerability Scanning are listed in “Approved Scanning Vendors (ASVs) Program Guide” at page 17:
- Firewalls and Routers
- Operating Systems
- Database Servers
- Web Servers
- Application Server
- Common Web Scripts
- Built-in Accounts
- DNS Servers
- Mail Servers
- Web Applications
- Other Applications
- Common Services
- Wireless Access Points
- Backdoors
- SSL/TLS
- Remote Access
- Point-of-sale (POS) Software
Easier to say – everything. What systems will be actually deployed in the PCI test infrastructure is not clear. Program Guide is not about technical details actually, it is more about basic description of the ASV assessment process, which I have already mentioned earlier.
Ok, let’s say we believe that there won’t be any problems with scanning test, what else do we needed?
Some organizational requirements from “Requirements for Approved Scanning Vendors (ASVs) v2.1“.
- The company should be registered and have some experience in providing security scans.
- “E-mail submissions will not be accepted”. You need to send application by regular mail.
- Some requirements against conflict of interests. Company should be careful in providing other security services (maybe including some hardening consulting?) and additional products (firewalls, IDS/IPS, “Database or other encryption solutions”, “Security audit log solutions”, File integrity monitoring solutions”, Anti-viruses) to the customers:
The ASV Company must have an internal separation of duties between the scanning service they provide and any managed security services provided to Scan Customers.
I think, it can be tempting NOT to find vulnerabilities in own products, so:
The ASV Company must fully disclose in a separate document and attach to the scan report if they perform PCI Scanning Services to customers who use any security-related devices or security-related applications that have been developed or manufactured by the ASV Company, or to which the ASV Company owns the rights, or that the ASV Company has configured or manages
Company should provide
A description of company’s practices to maintain scanning independence, including but not limited to, practices, organizational structure/separation, employee education, etc., in place to prevent conflicts of interest in a variety of scenarios
- Procedure: consider an application, invoice, after payment coordination of testing date.
- Company should have at least two employees performing or managing PCI Scanning Services
[They] must be qualified by PCI SSC. ASV Employees are responsible for performance of the PCI Scanning Services in accordance with the ASV Program Guide attending annual training provided by PCI SSC, and legitimately pass — of his or her own accord without any unauthorized assistance — the examination conducted as part of training. If an ASV Employee fails to pass any exam in connection with such training, the ASV Employee must no longer perform or manage PCI Scanning Services until successfully passing all required exams on a future attempt.
- Requirements for the employee experience. Years of work or/and certifications.
- In fact, all the procedures need to be repeated every year:
All ASV Companies and Employees must be re-qualified by PCI SSC on an annual basis, based on the ASV Company’s original qualification date. Re-qualification by PCI SSC is based on payment of annual fees, proof of training attended, achieving a passing result on the annual ASV Lab Scan Test and satisfactory feedback from the ASV Company Scan Customers (the merchants or service providers that received PCI Scanning Services) to PCI SSC
- Company should pay fees:
- The Initial Test for New Solution fee, which must be paid in full within 30 days of notification.
- An annual ASV re-qualification test fee for subsequent years.
- For each ASV Employee, a fee for PCI SSC training. This is an annual fee.
Fees in US$:
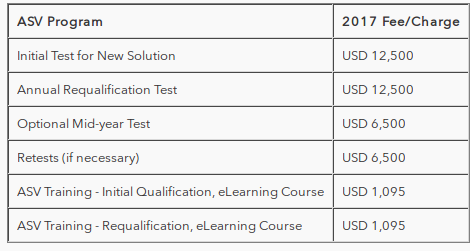
Source: https://www.pcisecuritystandards.org/program_training_and_qualification/fees
In conclusion
PCI ASV scanning is a good niche for vulnerability-scanning companies (I like this term in PCI documents, as well as “security scanning сommunity”). Mainly because this type of scanning is mandatory for the huge amount of the customers.
However, blurred requirements for the scanners it is really bad. It is impossible to detect every vulnerability in every software. Take for example, comparison of Nessus and OpenVAS. I can configure testing environment in various manners, choosing different network devices and OSes, so Nessus or OpenVAS, or both will not find dome vulnerabilities and probably fail the test.
IMHO, it would be much better to have a closed list of supported systems. The minimum cost of maintaining the ASV status is $14,700 per year. This is when all the tests are passed without errors from the first try. With current cost of testing, it is much profitable to use the Qualys, Tenable or Rapid7, scanner under the hood rather than try to test own scanning engine.
Pricing for ASV scanning is not regulated:
All fees and dates related to the ASV’s scanning services are typically negotiated between the ASV and the scan customer. The scan customer either pays all fees directly to the ASV, or may pay fees to the scan customer’s acquirer or other aggregating entity (if the acquirer or other aggregating entity has a contract with the ASV on behalf of a group of merchants).
If customer can freely choose ASV provider and there is no a big difference between them, as soon as they perform scanning through the Internet, why not to do make aggregator for PCI ASV services? The site where customers could set the list of target hosts, choose the best ASV solution by cost and additional services and launch the scan from the same interface? Using this platform it would possible to sell additional services like pentest, some special forms of scanning, maybe bugbounty and vulnerability intelligence. I haven’t seen such sites yet. Maybe startup? 😉

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

Alexander, thank you! Very useful.
Could you comment this part: “Some requirements against conflict of interests. Company shouldn’t provide PCI certification and audit at the same time”?
Why do you think that it’s a conflict of interests? Which statement of “Qualification Requirements” describes this statement?
Hi Andrey,
Thank you for your comment! It was probably my false interpretation of ASV Qualification Requirements “2.2 Independence”. I have read the requirements more carefully and now it’s clear that it’s not actually about PCI certification, but about providing other security services (maybe including some hardening consulting?) and additional products to the customer: “The ASV Company must have an internal separation of duties between the scanning service they provide and any managed security services provided to Scan Customers. ” p.7 and the company should provide “A description of company’s practices to maintain scanning independence, including but not limited to, practices, organizational structure/separation, employee education, etc., in place to prevent conflicts of interest in a variety of scenarios” p39
Fixed it. Thanks again!
Hi Alexander,
And also ASV Company should annually pay for insurance, that must compliance with requirements listed in Qualification Requirements for ASV (Appendix B: Insurance) 🙂
Do you know of any online training courses to become an ASV for individuals?
Pingback: What is a vulnerability and what is not? | Alexander V. Leonov
Pingback: По итогам выступления на Positive Customer Day | Александр В. Леонов