In my opinion, quality of knowledge base is the most important characteristic of Vulnerability Management (VM) product. Maybe it’s because I have spent significant amount of time making different security content for vulnerability scanners and this is some form of professional deformation. 🙂 The fact is that nowadays we have dozens of VM solutions on the market, which have very different knowledge bases and thus different abilities for detecting vulnerabilities. And really nobody talk about this. I can recommend related post “Tenable doesn’t want to be Tenable anymore” and especially HD Moore’s comment to that post. It describes the reason why nobody interested now in quality of detection. Maximum what we, end-users, can hear from the vendor about it’s knowledge base is an amount of vulnerability checks: 40000-80000 and approximate list of supported systems. There is a massive false belief that detection quality of the products is approximately the same and it’s better talk about dashboards, reports, SIEM-like capabilities. To demonstrate that the difference actually exists I made a pretty primitive comparison of Nessus and OpenVAS knowledge bases.
I chose these two products, mainly because information on their NASL plugins is available at Vulners.com. As I also wrote earlier how you can use easily parse Vulners archives in python, so you can repeat it for yourself. I talked about this topic at Pentestit webinar about Vulners. If you are familiar with Russian, you can also check this out. 😉 The slides for this presentation are available here.
Why I call this comparison fast and primitive? I don’t define the structure of KBs for this product and don’t carefully map one nasl script to another. I suppose it may be a theme for another posts. Instead I am looking at the CVE links. If two scanners detect can the same vulnerabilities, they should have the same CVE links in all the NASL scripts, right? In reality we have a great difference between the products and more than a half of the CVEs can’t be detected by using both of them.
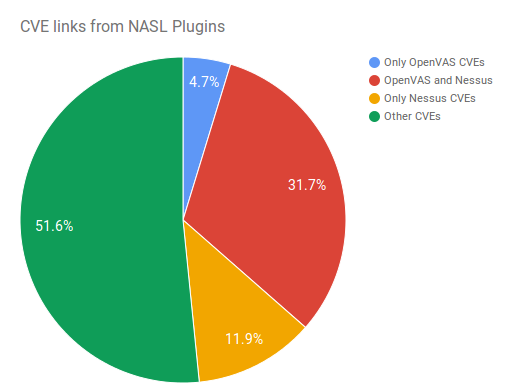
All CVEs: 80196
OpenVAS CVE links: 29240
Nessus CVE links: 35032
OpenVAS vs. Nessus: 3787;25453;9579
We can get group of the NASL scripts, “connected” with the links to the same CVEs. There are also thousands of NASL scripts in OpenVAS and Nessus that have some CVE links and can’t be mapped anyhow to the script in different KB.
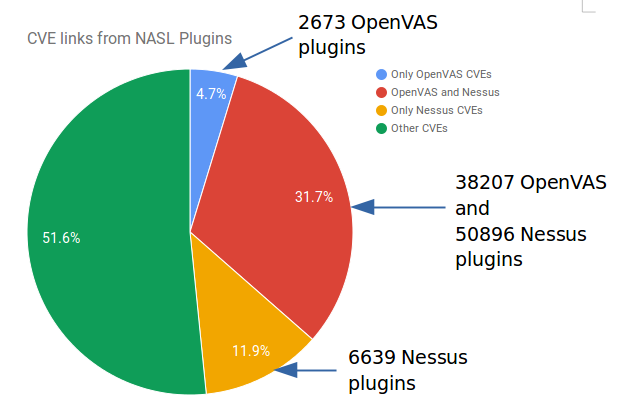
All NASL plugins:
OpenVAS: 49747
Nessus: 81349
Mapped plugins: 38207 OpenVAS and 50896 Nessus
Not mapped OpenVAS plugins: 2673
Not mapped Nessus plugins: 6639
I find the last part the most valuable and interesting. You definitely can use it to clarify the weak sides of your vendor’s solutions. What are the reasons of such difference? Well, it of course may be an error. Vendor haven’t added a link to the CVE id, but the check actually exists. That’s why this method of comparison is far from ideal.
Other reasons why vendor may ignore vulnerabilities:
- “Old” software and vulnerabilities. Vendor may think, that keeping vulnerabilities for some old software is useless. Well, for some vulnerabilities in non-supported Linux distributions, like Mandrake Linux, it can make sense.
- Vulnerabilities in plugins for some software. E.g. OpenVAS detects “WordPress VideoWhisper Live Streaming Integration Multiple Vulnerabilities“, Nessus not.
- “Local” software. E.g. OpenVAS detects vulnerabilities for French project “openMairie“, Nessus not.
- Non-enterprise software and devices. E.g. OpenVAS detects “D-Link DIR-100 Router Multiple Vulnerabilities“, Nessus not.
- Stopped adding new vulnerabilities for the software. E.g. OpenVAS detects “vBulletin 3.6.x to 4.2.2/4.2.3 Forumrunner ‘request.php’ SQL Injection“, Nessus not. Nessus detects Solaris vulnerabilities since 2010, OpenVAS not.
In other words:
- Vulnerability Scanner is a necessity
- However, don’t depend too much on them
- If Vulnerability Scanner does not detect some vulnerability — it’s YOUR problem not your VM vendor
- Choose VM solution you can control
- Have alternative sources of Vulnerability Data (vulners.com, vFeed)
So, once again. The reason of this post is not to say, that one vendor is better than another. Both Openvas and Nessus have their great sides. However, there are certain gaps in knowledge bases of vulnerability management products and I believe they can be fixed in dialogue of regulators, VM vendors, Security Content developers, and independent security practitioners.

Hi! My name is Alexander and I am a Vulnerability Management specialist. You can read more about me here. Currently, the best way to follow me is my Telegram channel @avleonovcom. I update it more often than this site. If you haven’t used Telegram yet, give it a try. It’s great. You can discuss my posts or ask questions at @avleonovchat.
А всех русскоязычных я приглашаю в ещё один телеграмм канал @avleonovrus, первым делом теперь пишу туда.

I like OpenVas. For this integrated automated scan with openVAS to penteston.com when u scanning site check openvas and it scan and send to u result about scan result when it finished.
Hello Rashad! This online service seems nice. I hope to check it out soon. Thanks for the information. =)
Thank you Alexander, waiting your post about this. If you with I give you free account for analyze it.
Alexander, great read. Thank you. Any advice for enterprises that rely on these tools to cover the gap of vulns that are not discovered?
Hello Adam! Thanks for kind words. =) Good practice is to use several vulnerability scanners and somehow combines the result. To scan the perimeter you can use free services: Qualys SSL labs, High-Tech Bridge SSL Server Security Test. Inside your network you can use OpenVAS. To scan Linux Servers with authentication, you can use a free Vulners Linux Audit service.
How about Qualys’s products?
Hello Mike! If we try to compare Nessus and Qualys the results should be similar. Even in theory the sets of detections plugins can’t be the same for two different scanners. Too many plugins VM vendors still need to make manually and there are too many vulnerable software products to support them all.
In practice it’s more difficult to prove because Qualys don’t like to show their vulnerabilities database. You can’t even search for QID in public service, as you can do for Tenable and Rapid7. I don’t have access to Qualys API ( “Exporting the Vulnerability KnowledgeBase to an external Database” https://community.qualys.com/docs/DOC-2976) if you have it access to Qualys API, you can try to make own comparison.
Pingback: ZeroNights16: Enterprise Vulnerability Management | Alexander V. Leonov
Pingback: Comparison of Nessus and OpenVAS CVE Differences – Technology News and Information by SeniorDBA
Pingback: Who wants to be a PCI ASV? | Alexander V. Leonov
Pingback: My comments on Forrester’s “Vulnerability Management vendor landscape 2017” | Alexander V. Leonov
Pingback: Problems of Vulnerability Prioritization and Detection | Alexander V. Leonov
Pingback: CyberCentral Summit 2018 in Prague | Alexander V. Leonov
Pingback: CISO Forum and the problems of Vulnerability Databases | Alexander V. Leonov
Pingback: OpenVAS vs Nessus – 382 degrees
Pingback: Vulnerability Management Product Comparisons (October 2019) | Alexander V. Leonov
Pingback: Сканирование на уязвимости и безопасная разработка - Deteact